Discussion On Threat Intelligence Vs SIEM
Question
This assessment explores the concept of cyber threat intelligence. The assessment will develop your skills to research and analyse contemporary network security issues and evaluate strategies to mitigate risks facing organisations.
Threat Intelligence is currently a popular term used within the cyber security domain. Conduct research on this term from a network security context and answer the following questions
Tasks:
- Define and describe the term Threat Intelligence.
- Draw a figure or visual diagram to illustrate your description of Threat Intelligence provided in Task 1. You can use any graphic illustration software to complete this task. The figure can be the size of half a page to a full A4 page. Ensure everything in the figure is legible. Add a description at the bottom of the figure clearly describing what the reader is expected to understand from the figure.
- How is Threat Intelligence different from a SIEM? You should first define what a SIEM is, and then contrast between characteristics of Threat Intelligence and SIEM.
- Discuss whether Threat Intelligence is important to the following organisations and provide justification.
- University
- Local News Agency
- Review two commercial/open-source products that offer Threat Intelligence. You review should describe the advantages and disadvantages of these products in your own words. Do not copy-and-paste content from their vendor websites.
When you assess the above organisation, make assumptions about the organisations size, functions, and their needs from a business perspective as well as technical requirement. Lastly, consider the kind of threats the organisation is likely to face based on these assumptions. This should allow you to justify your response.
Answer
Introduction
The present report presents a precise description on Threat Intelligence vs SIEM. There are different forms of security threats and attacks that are present. It is necessary that the prevention and control for these security threats is provided so that the information properties can be safeguarded at all times. The purpose of this report on Threat Intelligence vs SIEM is to cover the information on threat intelligence and compare the same with SIEM. The threat intelligence is described in terms of the local new agency. The report includes the description of threat intelligence along with the threat intelligence info graphic. The organization assessment and product review is covered in the study on Threat Intelligence vs SIEM.
Threat Intelligence
There is extensive use of digital technologies that can be seen in the present times. The increase in the use of automation and the enhanced connectedness has brought several changes in the business operations, economic flow, and the cultural lifecycle. However, there are also numerous risks that have emerged with the increased use of technology. These risks outlined in the study of Threat Intelligence vs SIEM are in the form of information security threats and attacks (Malone, 2015). There are ways in which the threats can be predicted and controlled. Threat Intelligence can be defined as the use of intelligent system and analytics for the purpose of threat prevention and mitigation. The context behind the security threats is determined in threat intelligence and these come in the form of associated motivation and capabilities along with the nature of the threat and the patterns used. This can assist in taking effective decisions regarding the steps that shall be taken towards security.
Threat Intelligence can be defined as the evidence-based knowledge that also comprises of the context and mechanisms along with the indicators and implications associated with the existing or upcoming threats. In the discussion on Threat Intelligence vs SIEM, the intelligence can be utilized to take effective decisions on the response that a system or an application shall provide to the threat. The number and types of the security threats is increasing with every passing day and it is essential that effective controls are applied on these threats (Shakarian, 2018). There are a few organizations that carry out the analysis on the threat data and incorporate the same on their network. However, they do not have clarity on the mechanisms that shall be applied on the additional data which puts undue burden on the analysts. All of these issues and concerns can be resolved with the aid of threat intelligence solutions. The effective solutions utilize the machine learning algorithms for automating the data sets and process them to integrate with the existing solution. The unstructured data is captured from a variety of sources and the threat context is determined with the identification of the tactics, techniques, and specific procedures used by the threat actors. There are several benefits that result with the correct use and application of threat intelligence.
As per the research on Threat Intelligence vs SIEM, there are information security teams that are present in the business organizations. These teams often fail to process the alerts that they receive regarding the violation of the security norms. Threat intelligence provides the mechanism to integrate the security solutions with the data sets and automate the alerts and the other threats. There are vulnerability management resources that are deployed by the business firms and the patterns that are obtained in threat intelligence enable them to accurately prioritize the vulnerabilities for their resolution. There are fraud management teams that are also engaged with the organizations and the knowledge regarding the tactics and procedures followed by the attackers enable them to develop the strategies for the overall prevention and avoidance of the security threats. This leads to the improvement in the overall security and privacy of the business organization and the data sets that it uses (Jasper, 2016).
Threat Intelligence Infographic
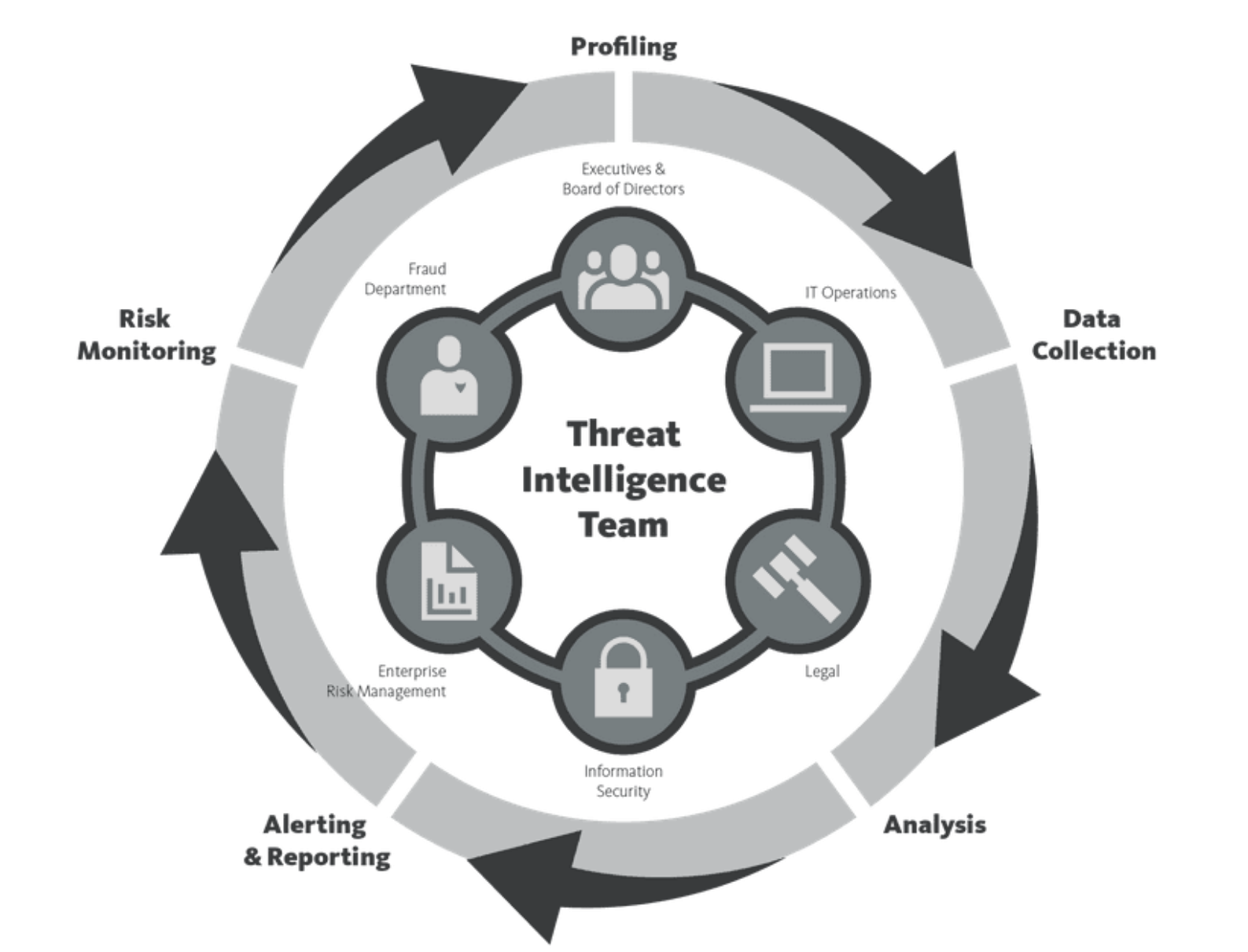
Threat Intelligence Diagram (Zrahia, 2018)
The different stages that are involved in the threat intelligence framework are shown in the diagram above. The first step includes profiling which is followed by the collection of the data sets for the purpose of threat intelligence. These data sets are analysed and there are alerts and reports that are generated on the basis of the results. The monitoring of the risks and threats is also done as per the information.
Threat Intelligence vs SIEM
SIEM is an abbreviation for Security Information & Event Management and it is software that provides the IT team and resources to gain insight to the processes and activities.
In the discussion on Threat Intelligence vs SIEM, it is stated the both the aspects are not the same and there are differences that are present between the two. SIEM is a broad concept which may include several techniques for the purpose of streamlining the IT functions along with the information security and privacy. There are varied security techniques that may be used as part of SIEM and threat intelligence can be one of these. Threat intelligence makes use of the intelligent codes and algorithms to determine the threat lifecycle. However, in case of Threat Intelligence vs SIEM, SIEM may be a combination of these intelligent techniques and other techniques to manage the security of the information sets and to handle the different events that may result out of the same. There are also differences that may be present in the lifecycle of Threat Intelligence vs SIEM. The threat intelligence can be combined with SIEM and it can be one of the techniques that may be used for security management (Keim & Mohapatra, 2019).
Organisation Assessment
University
Organization Background
The organization is a university that provides a number of courses to the students. Currently, there are numerous students and faculty members that are associated with the university. The university also provides distant learning options to the students.
Organization Needs
The organization needs in terms of information security are relevant as the data of the students, such as student demographics, grades, course taken, and likewise is private and sensitive information. Also, the course data and faculty details can be shared only with the authorized entities. The occurrence of security threats can cause damage to the university reputation.
Security Threats
There are security threats that the university database is exposed to in terms of the database injection and malware attacks. The data is also accessible through the university portal which may result in the network and web-based security attacks.
Threat Intelligence
It illustrated in the Threat Intelligence vs SIEM that the effective solutions use the machine learning algorithms for automating the data sets and process them to incorporate with the current arrangement (Janiszewski et al., 2019). The unstructured data is caught from an assortment of sources and the threat context is resolved with the distinguishing proof of the tactics, techniques, and explicit methods used by the threat actors. There are a few advantages that outcome with the right use and application of threat intelligence. There are information security teams that are available in the business associations. These teams regularly neglect to process the alerts that they get with respect to the infringement of the security norms. Threat intelligence gives the system to incorporate the security solutions with the data sets and computerize the alerts and different threats. There are threat management resources that are sent by the business firms and the patterns that are gotten in threat intelligence empower them to precisely organize the vulnerabilities for their goals. There are fraud management teams that are additionally drawn in with the associations and the information in regards to the tactics and techniques followed by the assailants empower them to build up the procedures for the overall counteraction and shirking of the security threats. This prompts the improvement in the overall security and privacy of the business association and the data sets that it uses.
Local News Agency
Organization Background: The organization that has been selected in the context of Threat Intelligence vs SIEM is a local news agency that comprises of 40 employees and the primary functions of the organization include the coverage of the news and sharing of the same with the public through tele media, print media, and social media platforms. The organization works on the real-time basis as the news collected is required to reach to the people as early as possible.
Organization Needs
In order to function adequately, there are several technologies that are used by the local news agency. The use of web-based communication tools and computer networks is done along with the cloud databases and computer systems. These are required for streamlining the data sets and making sure that the automation of the entire process is done. These technologies are also relevant from the business perspective as the new agency can be successful only when it is the first in the business to pass the news to the people.
Security Threats
There are several security threats that are associated with the organization. This is because of the increased competition in the industry. All of the business entities wish to stay ahead of their competitors. This may lead to the execution of security threat by the competitors. The insider threats may be given shape by the competitors by gaining the confidence of the employee of the local news agency (Oriola, 2018). The malware inflections or flooding attacks may be carried out in this manner.
There is also a lot of customer data that is associated with the news agency. The attackers can capture this data by carrying out unauthorized monitoring of their networks. The patterns from the social media channels can also be obtained which may result in the misuse of the information shared.
Threat Intelligence
The study on Threat Intelligence vs SIEM signifies that the need for threat intelligence is significant for the organization so that it may be able to achieve the business goals. The threat intelligence will allow the local news agency to predict the security threats in advance and the measures to control the same will be accordingly taken. The context behind the security threats is resolved in threat intelligence and these come as related motivation and capabilities alongside the nature of the threat and the patterns used. This can assist in making effective decisions in regards to the strides that will be taken towards security. The intelligence can be used to take effective decisions on the reaction that a framework or an application will give to the threat. The number and types of the security threats is expanding as time passes and it is fundamental that effective controls are applied on these threats. The local news agency will also be able to ensure that it provides undisrupted services to the consumers.
Product Review
There are several open-source threat intelligence products available in the market that may be used by the organization.
|
Product |
MISP – Threat sharing framework |
Open CTI |
|
Description |
MISP is one of the widely used threat intelligence and threat sharing platform that is open-source. The tool is developed with the objective that sharing of the threat information can lead to the avoidance and prevention of the security threats and issues (Misp, 2020). |
Open CTI is one of the threat intelligence tools which is used to share and visualize the information around the threats. It provides a unified platform to ensure that all of the threat intelligence activities can be carried out from the same platform (Opencti, 2020). |
|
Advantages |
· Automatic correlation to determine the relationship between varied threat channels and sources · Sharing functionality is in-built so that the threat sharing can be easily done · Flexible and free text import · Easy to use |
· Automated reasoning · Use of consistent data model · Data access management · Knowledge graph |
|
Disadvantages |
There is a basic technical understanding that is required to utilize the tool. The initial costs may be involved in the areas as installation and trainings. |
There are no regular updates that are made to this tool which is a cause of concern. |
Conclusion
In the discussion on Threat Intelligence vs SIEM, threat intelligence can offer numerous benefits to the business firms that make use of these tools. It has become essential for the business firms to obtain an understanding of the threat patterns and trends so that the same can be prevented and avoided. The detailed threat patterns are obtained with the aid of threat intelligence tools and these are extremely effective in the overall maintenance and promotion of the data and network security.
References
Janiszewski, M., Felkner, A., & Lewandowski, P. (2019). A Novel Approach to National-level Cyber Risk Assessment Based on Vulnerability Management and Threat Intelligence. Journal of Telecommunications and Information Technology, 2, 5–14. https://doi.org/10.26636/jtit.2019.130919
Jasper, S. E. (2016). U.S. Cyber Threat Intelligence Sharing Frameworks. Threat Intelligence vs SIEM International Journal of Intelligence and CounterIntelligence, 30(1), 53–65. https://doi.org/10.1080/08850607.2016.1230701
Keim, Y., & Mohapatra, A. K. (2019). Cyber threat intelligence framework using advanced malware forensics. International Journal of Information Technology. https://doi.org/10.1007/s41870-019-00280-3
Malone, R. (2015). Protective intelligence: Applying the intelligence cycle model to threat assessment. Journal of Threat Assessment and Management, 2(1), 53–62. https://doi.org/10.1037/tam0000034
Misp. (2020). MISP - Open Source Threat Intelligence Platform & Open Standards For Threat Information Sharing (formely known as Malware Information Sharing Platform). Www.Misp-Project.Org. https://www.misp-project.org/index.html
Opencti. (2020). OpenCTI - Open platform for cyber threat intelligence. OpenCTI - Open Platform for Cyber Threat Intelligence. https://www.opencti.io/en/
Oriola, O. (2018). A Cyber-Threat Intelligence Framework for Improved Internet Facilitated Organized Crime Threat Management. International Journal of Computer Trends and Technology, 60(1), 1–14. https://doi.org/10.14445/22312803/ijctt-v60p101
Shakarian, P. (2018). Dark-Web Cyber Threat Intelligence: From Data to Intelligence to Prediction. Threat Intelligence vs SIEM Information, 9(12), 305. https://doi.org/10.3390/info9120305
Zrahia, A. (2018). Threat intelligence sharing between cybersecurity vendors: Network, dyadic, and agent views. Journal of Cybersecurity, 4(1). https://doi.org/10.1093/cybsec/tyy008












