SOP & Decision Making Framework For Penetration Testing Assignment
Question
Task:
This is an individual assessment comprised of two tasks. Task 1 and task 2 carry 50% respectively of the overall portfolio mark. Task 1 will assess your understanding of the statutory and ethical issues surrounding penetration testing and also assess your understanding of the process itself. Task 2 will assess your ability to conduct a full-scale penetration test. You are expected to demonstrate an insight into the implications of the problem introduced in each task by using clear and concise arguments. You will receive formative feedback as part of the module to demonstrate how to be concise in your written work. Please ensure, in completing these tasks you deploy the techniques you have been taught. If you produce work that is not concise and to the point, then marks may be reduced. The reports should be well written (and word-processed), showing good skills in creativity and design. Sentences should be of an appropriate length and the writing style should be brief but informative.
Task 1 – SOP for PenTesting
Task 1 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to undertake research and critically compare the published penetration testing methodologies. You are expected to comment on the statutory and ethical considerations of a penetration tester. You are expected to design/develop a Standard Operating Procedure (SOP), including a decision-making tree, to describe how you will undertake task 2. In particular: intelligence gathering (target profiling), vulnerability identification and analysis, and target exploitation (including post exploitation). An SOP is defined as a set of step-by-step instructions compiled by an organisation to help workers carry out routine operations.
Task 2 – Penetration Test
Task 2 is weighted at 50% of the overall portfolio mark. It is expected that this task of the portfolio will be the equivalent of 2000 words. You are expected to conduct a penetration test against a target system that will be provided to you. You are required to present your findings in a factual manner to convince decision makers of a large corporation on business strategies. Do not provide a narrative of your intelligence gathering activities in the main report. You should include this in an appendix. You can use the VPN for undertaking this activity.
Answer
The role of Pentesting explored in the context of penetration testing assignment is used for the maintenance of security, which is useful in identifying vulnerability in the web, or mobile application. The main objective that is adopted by pentesting is the analysis of the vulnerability and acts in stimulating the cyber-attack in an effective manner. The ethical hacking ensures that the system is secure and does not possess any kind of issues associated with the threat to the customer. The step by step strategic implication is used to identify the vulnerability and then measures are taken to solve the issue. The use of SOP is done to execute the entire pentesting process in a profound manner without any kind of problems. The whole process of Pentesting is legal, thus the use of ethical consideration will be showcased in the concern penetration testing assignment. Proper SOP and decision-making framework will be used to explain the method of pentesting in a systematic manner. The study obtained in the penetration testing assignment will take into consideration the different procedure that is used in the execution of pentesting vividly.
Task 1 – SOP for PenTesting
Penetration testing methodology
The strategic evaluation of the different methodologies is essential for the execution of the services in an organized manner and thus reducing the level of confusion. OSSTMM framework consist of 10 domains of security which are taken into consideration under which human safety is foremost. This framework ensures that the protection of security is done on the basis of open source management. As mentioned in the article “linking continuous improvement to manufacturing performance”, which is undertaken in the penetration testing assignment to prepare the concerned study, the frame incorporates the Quarantive verification of the vulnerability, and then effective measures are taken for safety. The focus of this framework is the identification of the objects that need to be tested (Schniepp, 2017). It is useful in identifying the valid regulations and thus takes up the initiatives of safety execution of cyber security. The use of open-source in the framework incorporates a verity of cyber security issues in a flexible manner and serves in mitigating the vulnerability in a profound way. Whereas OWASPmethodology consist of positive and active mode is considered to be the two main parts of the OWASP methodology. As mentioned in the article “Web from preprocessor for crawling”, the core objectives of the issues are identified in the testing methodology. The two main question that are identified is associated with what and when (Muñoz and GarcíaVillalba, 2015.) The testing on the cryptography, which is weaker in nature is completed effectively with the help of the concern pentesting methodology (Poláceket al., 2016). Vulnerability injections in the web application such as JAVA, HTML as well as CSS are identified in an effective manner with the help of the OWASP methodological framework. At the same time NIST methodology is associated with the effective execution of the NIST methodological framework is considered to be essential. The proper incorporation of the attributes of tool testing is evaluated in the concern pentesting methodology.
The test discussed in the penetration testing assignment is mainly used in the categories of tools. Thus the execution of NIST methodical framework is profound in their own way. At the same time PTES methedology is associated with the evaluation of the different modeling aspects and factors of structural testing (Muñoz and GarcíaVillalba, 2015). As mentioned in the article “Quantitative evaluation of vulnerability scanning, it is an after explaining strategic measures”, that the security of the devices need the test of the tools used in the application in an effective manner (Holm et al., 2015). However, ISSAF methodology is a very complicated methodological framework and thus takes into account the practical evaluation of vulnerability and mitigates them in an effective manner without any confusion.
Penetration test and its Statutory and legal consideration
The execution of influencing the analysis of pentesting in a systematic manner is done. The use of strategic measures is useful in ensuring the fact that the information is safeguarded with the help of the data protection tools.
Computer Misuse Act 1920: The government to ensure that the ethical hacking with the permission of the government of the cybersecurity will be done in a sequential manner incorporates different regulations. The use of the act explored in the penetration testing assignment is to reduce the effective of misusing cyber regulations. Issues regarding privacy are identified to be profound in the execution of pentesting (Levendowski, 2018). Proper networking, as well as the step by step procedure, is incorporated to ensure that the system has the ability to execute the mitigation strategies in a sequential manner. The introduction of the Cyber Security Enhancement Act 2002 has been a boot to the sector of cybersecurity. The use of active measures is done to ensure that the pentesting methods can use ethical consideration and secure the privacy of the customer in an effective manner. Activated related to fraud is common (Kami?ski et al., 2018).
Data protection Act 2018: It is, therefore, essential for the team executing pentesting to take up the approaches of implementing effective measures and safeguard the private information for being public. The entire pentesting procedure is ethical, and the hacking done in mitigating the identified vulnerability is moral in nature. Interaction in the pre-engagement stage of pentesting is considered useful in ensuring the fact that the situation is analyzed in a systematic manner.
The collection of proper and relevant information regarding the existence of application vulnerably is essential for this penetration testing assignment. It assures that the system is able to serve the drawback in an effective manner without any issue. The hacking experts in a profound manner take measure for the proper inspection of the threat and its intensity in this stage. This ensures that the risks are identified before it caused much damage to the system and the documents stored in it. The actual operation is executed in an ethical manner. The stages of pentesting incorporate the proper coding to mitigate the issues in an effective manner (Shumpei and Mihail, 2018). This is the inspecting stage. The threat and the action after the mitigation process are identified, and symptoms are evaluated in an effective manner.
Task 2 SOP
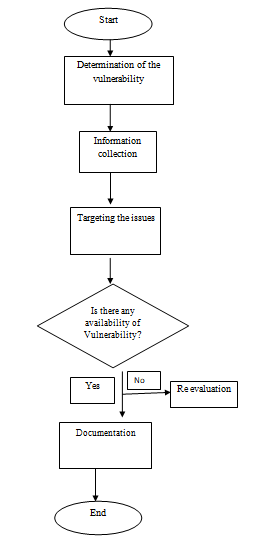
Figure 1: SOP
(Source: Developed by the author)
The process of developing SOP is considered to be effective within the case scenario of penetration testing assignment in incorporating coordinative measures in the business organization. The use of SOP is consisted to be effective in enhancing the systematic execution of the business evaluation. The process is essential in reducing the vulnerability of the individuals and thus increases the strategic measurements of the pen-testing (Holm et al., 2015). The weakness in the individual documents is reduced with the help of the SOP procedure.
Following are the steps for the effective execution of SOP pentesting provided in the context of penetration testing assignment:
Execute outline the process list that needs type: It is essential for the pentesting process to execute the strategy in a systematic manner. The identification of the issues and collecting proper information about the steps that need to be incorporated within the vulnerability mitigation is mandatory. Keeping a close watch on the strategic measures are necessary. It is essential that all the methods to be pointed out in a systematic manner to reduce the level of confusion and ensure the effective execution of the pentesting process (Dutta and Karak, 2017).
Process planning: This stage noted in the penetration testing assignment will be useful for task 2. In this stage, proper planning will be done regarding targeting the vulnerability profit as well as gathering useful information to mitigate the issues of vulnerability in web applications.
Information collection regarding SOP: This step is considered effective in maintaining the proper documentation of the service executing procedure (Chrusciel-Nogalskaet al., 2017). It is evaluated that the effective collection of information is considered to be effective in maintaining the ethical aspect of pentesting using SOP.
Review writing and collecting feedbacks: It is therefore essential to obtain the proper feedbacks so that the entire system can be modified in a systematic manner. The stage is useful in evaluating the positive or negative approach of the process in a profound way. The written documents are effective in the evaluation of the issues faced during the pentesting procedure in a well-organized manner.
Maintain of SOP: The execution of the strategic measures to incorporate the pretesting process is vital. The readings used to prepare this penetration testing assignment mentions that it is essential that the team identify the issues and motivate it's after a regular interval of time. This is effective in ensuring the fact that the process is executed in a practical manner and, thus enable in the stable and systematic execution of the study (Baiardi and Sgandurra, 2015).
The effective incorporation of the SOP within a business is considered to be beneficial in ensuring the execution of the entire project within the allocated time frame. The regular inspection of the framework reduced the amount of vulnerability that ensures that the team is able to serve the business in a profound manner. The proper incorporation of SOP in business organization and thus, maintain private security.
Decision-Making Tree for Task 2
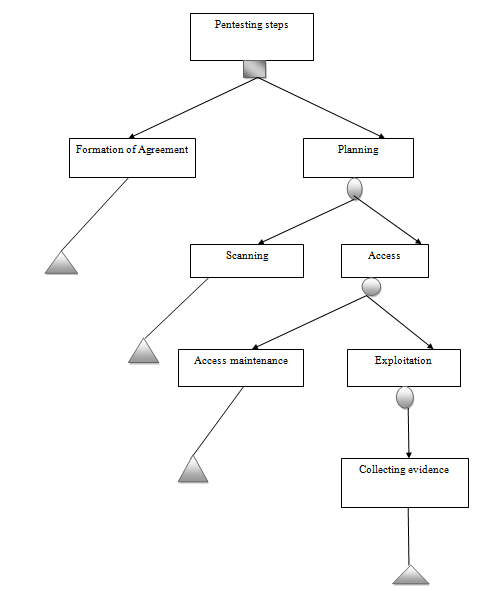
Figure 2: Decision-making tree
(Source: Created by Author)
The effective evaluation of the decision making tree as prepared in the penetration testing assignment is to identify the mechanical implication of the strategic execution. The examined form of planning is executed with the help of the decision-making tree. The tree ensures that fact that all the decision-making approaches are performed in a systematic manner reducing the level of confusion. The use of structural representation of the decision-making tree is considered to be beneficial in evaluating the fact of incorporating essential information for the effective mitigation of the issues without any confusion (Baiardi and Sgandurra, 2015). The increase in the level of uncertainty is considered to be effective in ensuring the fact that the team is effective in introducing a systematic pentesting procedure. This procedure is considered to be beneficial in reducing employee confusion in an effective manner and thus reduce the level of web application vulnerabilities. The use of the decision tree is useful in ensuring the forecaster of the task that is essential for the execution of the services in a vivid manner.
The effective incorporation of the pen-testing approaches takes into consideration a flow of steps for the execution of ultimate results. The agreement phase is associated with the identification of the intensity of the vulnerabilities. The vulnerabilities of the when are evaluated, and strategic measures are taken to evaluate the systematic approach in an effective manner. The stage of planning mentioned in this segment of penetration testing assignment is a crucial part of the testing procedure (Levendowski, 2018). It enables the collection of information about the IP address, and the practical evaluation of the used tools is done. Scanning of the entire procedure is effective and thus is included in the decision making tree. The tree is useful in understanding the needs of the system and thus ensures that the strategies are incorporated in a profound manner. Maintain access is also evaluated as the stage of system rebooting. This enables the stem to identify the vulnerable stage for further rectification. The mitigation of the detected vulnerability, as well as an evaluation of the strategic measures by collecting authentic feedbacks, is needed (Schniepp, 2017). The use of the decision making tree is effective in reducing the level of flaws and the team is able to attain clarity in their minds. This at the same time is effective in ensuring the fact that the team does not take up any inconvenient measures for the strategic implications.
It can, therefore, state that the incorporation of the strategic measures using the decision making a tree in task 2 is an excellent approach. This approach illustrated in the penetration testing assignment evaluated the entire procedure of pen-testing and, thus, useful branches the different aspects of decision for the better execution of the result. The use of the design making tree has the ability to provide a clear concept to the worker, and they will able to serve the task in an effective manner. The degree of confusion also decreasing and the team is able to gain success in the identified job.
Conclusion
Overall discussion build on this penetration testing assignment concludes that the use of pentest method is profound. It has the ability to reduce the amount of web-related vulnerability. The use of SOP approaches is helpful in the execution step wise procedure for the execution of the pentesting strategies is an effective manner. The purpose of the design making trees developed within the penetration testing assignment is also useful in identifying the visual clarification about the different decision making measures taken for the effective conduction of pentest. It is recognized that pentest safeguards private information and is ethically implicated. The guidelines measures ensure that the pentesting method is secure and has the ability to protect the personal data of the individuals in an effective manner.
Reference list
Baiardi, F. And Sgandurra, D., 2015. Assessing ICT risk through a Monte Carlo method. Environment Systems & Decisions, 33(4), pp. 486-499.
Chrusciel-Nogalska, M., Smektala, T., Tutak, M., Sporniak-Tutak, K. And Olszewski, R., 2017. Open-Source Software In Dentistry: A Systematic Review. Penetration testing assignment International Journal of Technology Assessment in Health Care, 33(4), pp. 487-493.
Dutta, S. And Karak, N., 2017. Blends of Mesuaferrea L. seed oil based polyurethane with epoxy resin. Pigment & Resin Technology, 36(2), pp. 74-82.
Holm, H., Sommestad, T., Almroth, J.AndPersson, M., 2015.A quantitative evaluation of vulnerability scanning. Information Management & Computer Security, 19(4), pp. 231-247.
Kami?ski, B., Jakubczyk, M. And Szufel, P., 2018. A Framework For Sensitivity Analysis Of Decision Trees: CejorCejor. Central European Journal of Operations Research, 26(1), pp. 135-159.
Levendowski, A., 2018. How Copyright Law Can Fix Artificial Intelligence's Implicit Bias Problem. Washington Law Review, 93(2), pp. 579-630.
Muñoz, F.R. And GarcíaVillalba, L.J., 2015. Web from preprocessor for crawling. Multimedia Tools and Applications, 74(19), pp. 8559-8570.
Polácek, T., Doubravský, K.AndDohnal, M., 2016.Reconciliation as a Tool for Decision Making within Decision Tree Related to Insolvency Problems. Trendy Ekonomiky a Managementu, 10(25), pp. 33-39.
Schniepp, S., 2017. What's in Your SOP? Pharmaceutical Technology Europe, 29(12), pp. 49-50.
Shumpei, I.AndMihail, M., 2018.Linking continuous improvement to manufacturing performance. Penetration testing assignment Benchmarking, 25(5), pp. 1319-1332.












