Research Methodology Assignment: Cyber Threats To Information Technology Of Bhutan Government
Question
Task: The purpose of this research methodology assignmentis to present and write up the research design on the topic “Knowing your enemy: Understanding the threats of information security in government organisations in Bhutan”.
Answer
1. Abstract
It is worth mentioning that a proposal is being developed regarding the threats of the information security system within the government organisations in Bhutan. The introduction chapter prepared within the research methodology assignment will provide a brief description of the overall research. By conducting this research, it will be possible for the researcher to identify the dominant threats of information security within the government organisation and find out preventive measures that can help to mitigate the threats of the information security system. On the basis of the understanding of the researcher of the given topic i.e., new arising cyber threats in the government organisations in Bhutan, a research has been conducted to the researcher’s best ability. Below is a detailed description of the research methodology used in the research. Every aspect and approach used in the methodology is described in the following paragraphs. An introduction and conclusion of the same have also been drawn at the beginning and end.
2. Introduction
As government organisations of Bhutan recently left the traditional methods of traditional methods of functioning and started using globally trending technologies, they are not very expert in maintaining enough efficient information technology guidelines. Hence, this research is based on the purpose of identifying the most dominant cyber threats to information technology of the government organisation of Bhutan and putting them in different categories as per their severity. In this research, the methodology found to be the most suitable for the purpose is the mixed approach. Both qualitative and quantitative data will be required for the completion of this research.
3. Main Section
3.1. Planned Research Design
This research requires old as well as new data for the study to be successful. This means both secondary i.e., qualitative and primary i.e., quantitative sources of data will be required. Hence, a mixed approach is the most suitable research methodology for this study. Qualitative or secondary data are the ones that are already collected by someone else before the researcher. Common sources of secondary data are articles, books, journals, newspapers, literature reviews etc. The major benefit of using secondary data is that it saved huge time (11). Else, collecting required data one by one all alone can be a lengthy process. Also, sometimes analysing the past changes might not be possible with primary sources of data. In that case, secondary data becomes absolutely essential to compare the current situation with the old one. However, secondary data might not be useful in marketing research of businesses as businesses have a dynamic environment and the old data might be outdated which will have no relevance with the modern situations. As qualitative data are found from old sources, they might have been used in many other researches previously. Still, they remain applicable to the new ones, except in certain cases (12). A qualitative database is associated with secondary data, where verbal or visual materials were originally created for some other purpose. In the case of cyber threats faced by government organisations, qualitative data will be useful for looking into previous studies to analyse the types of information security threats commonly used by the users.
On the other hand, the second component of a mixed approach is the quantitative data. Quantitative data or primary source is a document, artifact, diary, autobiography, manuscript, record or any other source of information that was created particularly at the time of the study. In the case of research, primary data are collected through surveys, questionnaires, interviews, public polls etc, experiments, field observations, life histories, case studies, action research, ethnographic research etc. There are certain benefits as well limitations of using primary data. Starting with the benefits, the first one is resolving research issues (13). Every research problem has something unique. Hence, performing own research helps to collect unique and specific information relevant for the particular research only. Next, it provides better accuracy and relevance. It provides better control of the researcher over the type of information. The information found is the most current one. Finally, the researcher owns the information. Sharing it or not depends completely on him. However, there are also some disadvantages to this approach. First of all, it is not always possible to perform, secondly, it can be highly time-consuming as well as expensive (14). In this case, a survey has been conducted to find out the common threats faced by employees of the organisation.
3.2. Planned Sample
As said previously, the approach used under research methodology is a mixed approach which includes the use of both qualitative and quantitative data. In the case of quantitative data i.e, collecting data from the primary source, the tool chosen is a survey. A survey is a process of collecting data from a pre-defined group of respondents. The process includes asking a set of questions to a group of people related to the issue. It can be conducted online as well as offline. Here the sample i.e., the related group of respondents is the employees of the organisation. However, including every single employee in the survey becomes tough. Hence, the sample size chosen for this survey was of 100 employees. Each one of them was provided a questionnaire with 10 close-ended general questions (15). There were multiple choice answers for each one. The respondents were supposed to put a tick on a single option of their choice. The questions were typically related to the issues the employees face regarding the cyber threats of information systems in their organisation. The options of some questions were based on the Likert scale where the respondents had to rate the severity of the threats they face.
An important thing to be kept in mind while conducting a survey is ethical considerations. This is a crucial part of any research. A research can even fail if ethical considerations are ignored. Some principles of ethical considerations are- The research should not cause any harm to the respondents in any way, the dignity of the participants always be respected, respondents should be included in the process only with their full consent, the personal details of the respondents must be kept private, the research data must be kept confidential, the anonymity of the respondents must be maintained etc. Finally, the pattern of sampling used in this survey is stratified random sampling (16). This process includes the division of related populations available into small sub-groups known as strata. These strata or sub-groups are formed based on certain common attributes or characteristics shared by a number of people. In this case, the respondents were grouped based on their job positions. This process is also called proportional random sampling or quota random sampling. This pattern was chosen to save time and avoid confusion as the sample size chosen was not very small. Also, this requires less time and effort as well as less finance.
3.3. Planned Instruments for Data Collection
Before focusing on the data collection, it is important to describe that research is being conducted to understand the threats of information security within the government organisations in Bhutan. After selecting the appropriate research design, the researcher needs to select the proper data collection method by which the overall study can be set up in a proper manner. According to [1], data collection is determined as the process of collecting, analysing and measuring appropriate insights for the study by utilising appropriate techniques. The author also described that it is the process through which the researcher measures and gathers data about a particular research topic in an incorporated systematic way that allows the researcher to answer the research questions and assess the outcomes. In order to collect proper information about the threats of information security within the government organisations in Bhutan, the researcher is considering a mixed data collection method. The mixed data collection method is also determined as a process in which the researcher has to collect both qualitative and quantitative data about the research topic. As stated by [2], collecting both qualitative and quantitative data will be appropriate for the researcher to conduct the research regarding the threats of information security within government organisations.
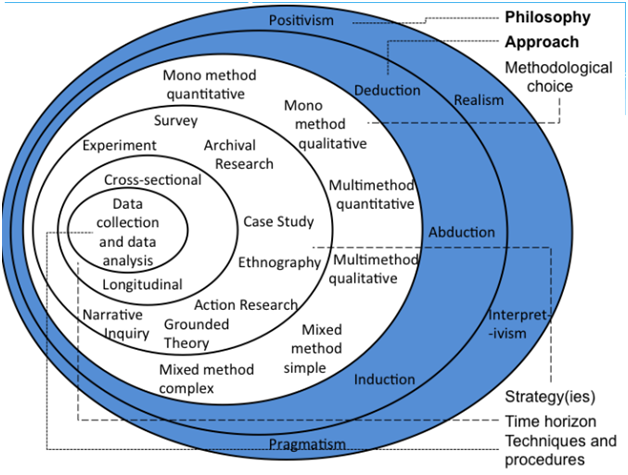
Figure 1: Mixed data collection method
(Source: [3])
It is very necessary to mention that the researcher will collect qualitative data from the primary data sources in which the researcher needs to select appropriate news articles, proceedings and ICT related conferences where data regarding the security threats are available. The researcher can also collect qualitative data about the security threats from the previous studies by which it will be possible to analyse the kinds of information security threats that are faced by the users within their corporations. Collecting information about the information security threats from different sources such as news articles, proceedings and ICT related conferences can enable the researcher to create a clear understanding of the information security threats. As per [3], the researcher also needs to collect quantitative data from the primary data sources in which the researcher will collect appropriate data about the information security threats through experiments, surveys as well as interviews. Particularly, in this research, the researcher needs to prepare some survey questionnaires and choose 100 respondents, in order to identify the common threats that are experienced within the organisation. Based on their responses, it will be possible to evaluate the severity of the threats and find out the most dominant threats within the organisations.
3.4. Planned Variables in the Study
In this particular study, there are mainly two planned variables that involve independent variables and dependent variables. It is required to describe that the government organisations within Bhutan are being considered as the independent variable and the threats of the information security system are considered as the dependent variable in this particular study. According to [4], the independent variable is considered as the variable that the experimenter changes or manipulates and is expected to have a direct impact on the dependent variable. Based on this theory, it can be stated that the government organisations within Bhutan are independent variables because the government organisations in Bhutan are not influenced by external factors, instead, the Government of Bhutan can have a direct impact or can directly affect the information security system, but instead, the information security system cannot impact the government organisations of Bhutan. It is also necessary to explain that the government organisations within Bhutan can develop new regulations which can influence the information security system to introduce changes within their system. So it is clear that the consideration of government organisations in Bhutan as the independent variable is appropriate.
The researcher has considered the information security system as the dependent variable in this particular research. As stated by [5], the dependent variable is considered as the variable that is measured as well as tasted within an experiment and it depends on the independent variable. The researcher also described that a dependent variable is something that relies on other factors. In this particular research, the information security system is considered as the dependent variable by the researcher because the information security system is largely dependent on the government organisations within Bhutan. The information security system cannot impact the government organisations of Bhutan because based on the policies developed by the government organisation of Bhutan, the information security system can function or needs to introduce changes. After this analysis, it has become possible for the researcher to create a clear understanding of planned variables in this study in which it has been identified that the government of Bhutan cannot be influenced by the information security system. It also has been observed that the information security system is dependent on the government organisations of Bhutan and this information security system can properly function or needs to introduce changes if the government organisations of Bhutan develop new policies.
3.5. Plan for Data Analysis
After collecting qualitative data from news articles and ICT conferences and quantitative data through the survey, the researcher needs to select an appropriate data analysis method in order to analyse collected information in an efficient manner. According to [6], data analysis is considered as the process of applying logical or statistical techniques in a systematic way to illustrate, evaluate as well as describe the collected information about the research topic. The author also explained that data analysis is a necessary element that helps the researcher to ensure that the integration of data is the appropriate and accurate analysis of the research findings. It is required to mention that data analysis is a procedure utilised by the researcher in order to reduce data to a particular phenomenon and interpret it for deriving insights. Data analysis is also considered the integral portion of the overall research. In this particular research, the researcher is considering a descriptive statistical analysis method to illustrate and describe the information about the threats of the information security system within the government organisations of Bhutan collected from news articles and the survey.
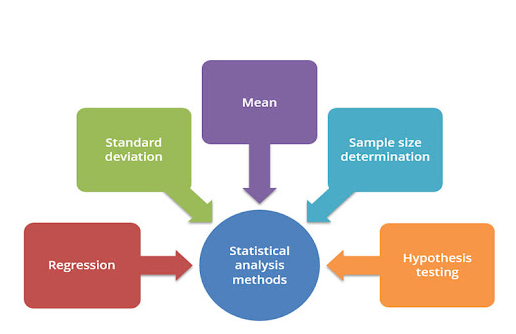
Figure 2: Statistical analysis method
(Source: [8])
The researcher needs to use structural equation models such as Excel in order to analyse the identification of preventive measures for mitigating the threats of information security. As described by [7], descriptive statistics are utilised by the researcher to describe the common features of the information within research. In addition to this, the researcher is also considering the thematic analysis method in order to analyse qualitative data which is gathered from news articles and ICT related conferences. As stated by [8], thematic analysis is considered a technique used by the researcher to analyse qualitative data. It has been identified that the researcher effectively examines the information in order to find out common themes like patterns, ideas and topics that repeatedly come up. It is necessary to mention that the researcher will analyse the collected information based on some specific themes. By considering the thematic analysis method, it will be possible for the researcher to properly illustrate and describe the threats of the information security experienced by government organisations of Bhutan. The researcher can also create a clear interpretation of the preventive measures to mitigate existing threats of information security. So it is clear that in order to analyse quantitative data, the researcher is selecting descriptive statistical analysis and to analyse qualitative data, the researcher is considering a thematic analysis method.
3.6. Plan for Data Presentation
As the approach chosen for the research is mixed, i.e., using both qualitative and quantitative data, hence the data presentation must also be of mixed type. The data found from the survey is represented first in a graphical form and next it is described in detail. Graphical data representation is generally used to represent numerical data. A diagram is used to reflect the relationship between ideas, concepts, data and information. This makes the understanding of the results easy as well as prevents boredom. This type of representation is dependent on information of a particular domain (17). There can be various graphical diagrams that can be used to represent the results found. First is the line graph. A line graph or linear graph represents a continuous data or sometimes future possible events. The next type is the bar graph. This type uses solid bars to represent various categories of data. The third type is histograms. This used bars to represent the frequency of data in certain intervals. The next type is the line plot. This shows the frequency of occurrence of a data. Each time a data occurs, an “x” is put above the line. Another type that shows the frequency of data with certain intervals is the frequency table. Next, the most commonly used graph is the circle graph or pie chart (18). The frequency is represented in percentage considering the complete circle as hundred percent. In this type o research, bar graphs and pie charts are the most commonly used graphical representations.
There are certain rules to be followed while presenting the data with graphical diagrams. Each graph should be given a suitable title about the content of its representation. The measurement unit must be mentioned. A proper scale must be chosen to represent the data in a proper manner, an index should be provided for the appropriate color, shade etc. The data source of the graph and its information must be mentioned. Graphical representation is used by almost all researchers in their studies (19). There are several merits of using this such as, it can easily be understood by anyone even without any prior knowledge, it is time-saving, It allows relating and comparing data for different time periods, in some cases where finding the mean, median modes of data, or finding interpolation and extrapolation of data is data is important, graphical data representation can be helpful. In this research study, after the graphical representation of the answers received of all the 10 questions is completed, a detailed description of all the figures is provided for an even better understanding (20). Hence, the data is presented in two ways for the simplest understanding.
3.7 Evaluation/Validation strategies used
While planning methods, creating research design as well as writing up the results, it is very important for the researcher to consider validity and reliability. According to [9], validity and reliability are the concepts utilised by the researcher in order to assess the quality of the study. It has been recognised that validity and reliability mainly refer to how well a technique or a method measures something. The author also explained that reliability is the consistency of a particular measure and validity is the efficiency of a measure. The reliability mainly indicates how consistently a particular method can measure something. For example, if the same outcome can consistently be obtained by utilising similar techniques under the same situations, then the overall measurement is reliable. In this particular research, the researcher has selected a descriptive statistical analysis method in order to analyse the collected information. It can be stated that the researcher has maintained the reliability of the descriptive statistical method in the research as they ensure that the outcome of the analysis is similar to the actual calculation.
As stated by [10], validity mainly indicates how appropriately a method can measure something. For example, if the study has a high validity then it indicates that the outcome corresponds to the characteristics and real properties along with variations in the social or physical world. The author also mentioned that if reliability is high that means the measurement is valid. The method utilised for collecting primary data is valid because the researcher has conducted formal communication by selecting those participants to know whether they have adequate knowledge about the threats of the information security system or not.
4. Conclusion and future work
As per the case provided of Bhutan, the government organisations that have currently changed their operations from the traditional style to the modern technologies are facing some cyber threats regarding their information system. As a conclusion of the study based on the mentioned topic, the components required for conducting mixed approach methodology could be successfully identified. After the completion of this research, the researcher will gain a better understanding of the approach and will be able to work better with the same in the future. Also, it gave an experience of conducting a survey which will be useful for further career.
5. References
[1]A. Karnoe, L. Kayser and L. Skovgaard, "Identification of Factors That Motivate People With Multiple Sclerosis to Participate in Digital Data Collection in Research: Sequential Mixed Methods Study", JMIR Human Factors, vol. 6, no. 4, p. e13295, 2019.
[2]M. Abir, R. Taymour, J. Goldstick, R. Malsberger, J. Forman, S. Hammond and K. Wahl, "Data missingness in the Michigan NEMSIS (MI-EMSIS) dataset: a mixed-methods study", International Journal of Emergency Medicine, vol. 14, no. 1, 2021.
[3]E. Flood-Grady, L. Solberg, C. Baralt, M. Meyer, J. Stevens and J. Krieger, "Engaging Institutional Stakeholders to Develop and Implement Guidelines for Recruiting Participants in Research Studies Using Social Media: Mixed Methods, Multi-Phase Process", Journal of Medical Internet Research, vol. 23, no. 10, p. e23312, 2021.
[4]M. Brauer and J. Curtin, "Linear mixed-effects models and the analysis of nonindependent data: A unified framework to analyze categorical and continuous independent variables that vary within-subjects and/or within-items.", Psychological Methods, vol. 23, no. 3, pp. 389-411, 2018.
[5]I. Arana Araya, "The Quest for Uncontested Power: Presidents' Personalities and Democratic Erosion in Latin America, 1945–2012", Political Psychology, 2021.
[6]A. Rajšp and I. Fister, "A Systematic Literature Review of Intelligent Data Analysis Methods for Smart Sport Training", Applied Sciences, vol. 10, no. 9, p. 3013, 2020.
[7]N. Duboust, M. Watson, M. Marshall and K. Kerrigan, "Towards intelligent CFRP composite machining: Surface analysis methods and statistical data analysis of machined fibre laminate surfaces", Proceedings of the Institution of Mechanical Engineers, Part B: Journal of Engineering Manufacture, vol. 235, no. 10, pp. 1602-1617, 2021 [Online]. Available: https://journals.sagepub.com/doi/pdf/10.1177/0954405420960920. [Accessed: 30- Oct- 2021]
[8]M. Kiger and L. Varpio, "Thematic analysis of qualitative data: AMEE Guide No. 131", Medical Teacher, vol. 42, no. 8, pp. 846-854, 2020.
[9]A. Souza, N. Alexandre, E. Guirardello, A. Souza, N. Alexandre and E. Guirardello, "Propriedadespsicométricasnaavaliação de instrumentos: avaliação da confiabilidade e da validade", Epidemiologia e Serviços de Saúde, vol. 26, no. 3, pp. 649-659, 2017.
[10]J. Rose and C. Johnson, "Contextualizing reliability and validity in qualitative research: toward more rigorous and trustworthy qualitative social science in leisure research",Research methodology assignmentJournal of Leisure Research, vol. 51, no. 4, pp. 432-451, 2020.
[11]N. Ruggiano and T. Perry, "Conducting secondary analysis of qualitative data: Should we, can we, and how?", Qualitative Social Work, vol. 18, no. 1, pp. 81-97, 2017. Available: 10.1177/1473325017700701.
[12]M. Johnston, "Secondary Data Analysis: A Method of which the Time Has Come", Qualitative and quantitative methods in libraries, vol. 3, no. 3, pp. 619-626, 2017. [Accessed 30 October 2021].
[13]K. Sileyew, "Research design and methodology", In Cyberspace, 2019. [Accessed 30 October 2021].
[14]J. Glidewell et al., "Population based surveillance of congenital heart defects among adolescents and adults: surveillance methodology", Birth Defects Research, vol. 110, no. 19, pp. 1395-1403, 2018. Available: 10.1002/bdr2.1400.
[15]S. Rahi, "Designing survey research: recommendation for questionnaire development, calculating sample size and selecting research paradigms.", Economic and Social Development: Book of Proceedings,, pp. pp.1157-1169, 2019. [Accessed 30 October 2021].
[16]T. Nguyen, M. Shih, D. Srivastava, S. Tirthapura and B. Xu, "Stratified random sampling from streaming and stored data", Distributed and Parallel Databases, vol. 39, no. 3, pp. 665-710, 2020. Available: 10.1007/s10619-020-07315-w.
[17]E. Genge, "Graphical tools of discrete longitudinal data presentation in R", Ekonometria, vol. 23, no. 3, pp. 26-39, 2019. [Accessed 30 October 2021].
[18]J. In and S. Lee, "Statistical data presentation", Korean Journal of Anesthesiology, vol. 70, no. 3, p. 267, 2017. Available: 10.4097/kjae.2017.70.3.267.
[19]P. Cuffe, "K. Healy: Data Visualization: A Practical Introduction [Book Review]", IEEE Transactions on Professional Communication, vol. 62, no. 3, pp. 310-311, 2019. Available: 10.1109/tpc.2019.2922787.
[20]Z. Peng, ". Graph representation learning via graphical mutual information maximization", In Proceedings of The Web Conference 2020, pp. 259-270, 2020. [Accessed 30 October 2021].












