Networking Assignment: It Networking & Communication
Question
Task:
You are a Network and Security Engineer for the ABC Consulting Private Limited, which is a leading
network and security provider for the small and medium scaled offices.
Task 1: Your task is to propose a network design for the small scaled company and sketch a
basic logical network diagram of the office with 5 departments. You are free to assume:
• Name of the Office and Departments
• Networking Hardware’s such as routers, switches, hubs, modems wireless access
points, firewalls etc.
Task 2: Using your expert knowledge on TCP/IP Model and its layers, sketch the TCP/IP
protocols and identify at least one protocol used by each layer.
Task 3: At each level of the TCP/IP model, there are security vulnerabilities and therefore,
security prevention measures that can be taken to ensure that enterprise applications are
protected. As a network and security engineer, your task is to identify the security threats and
propose a solution on each layer.
The report should be prepared in Microsoft word and uploaded on to the LMS. The word limit
of the report is 2000 words. The report should be a properly constructed as an academic
report. The report should include references in IEEE style.
Answer
Introduction of the Report
The aim of the selected report on networking assignment outlined the proceedings of the network framework, where the admin of the ABC Consulting Private Limited, one of the leading network and security providers for small scale and medium scale business, will be responsible for proposing the necessary topology to accomplish the network credentials in the best possible manner. The outline of the study focused in the segments of networking assignment is classified into three parts, where different points analyzed different networking concepts such as TCP/IP Protocol with its potential threats and solutions along with supporting the findings by matching the requirements in the best possible manner.
Task A: Network Design and Topology
Outlining the framework
In the present scenario of networking assignment, the findings of the report will illustrate the requirement network credentials for the selected company, the Iconic, which is a growing E-commerce Sydney based fashion company. The organization mainly operates its business operational activities by maintaining a comprehensive online platform. The headquarters of the company is situated in the harbour city of Australia, Sydney, and from there, the entire business operations get operated by the participation of five operational departments. Therefore, ABC Consulting Private Limited has been hired by the management of the Iconic, to provide the best possible networking solution by implementing adequate network securities to stay all time connected by maintaining the optimum network speed and connectivity.
Nevertheless, in this situation as stated in the networking assignment, the job role of the network admin is to configure the network topology based on segment-wise, which will sketch a basic logical diagram that will support both wired as well as wireless access over the networks by interconnecting all the departments with the Head Office.
Background of the organization with its business operations
As the reason behind the selected brand operates its business operational activities on the digital platform, a considerable amount of IT infrastructure is required in order to support the proceedings of the business in the required manner. In the present scenario, there are five operating departments in the organizational framework, which are responsible for maintaining the pattern of the business by ensuring zero downtime tolerance value. The concept of E-commerce has provided as one of the significant break thoughts in recent times, where it promoted how online shopping has become one of the significant trends [1]. Therefore, major technological advancements, along with maintaining an excellent networking platform, are the fundamental core areas of discursions in the findings of the current study.
Network Infrastructure and Connectivities
There are five major operating departments present within the selected company, the Iconic. In order to provide the best service to the customers in the platform of the digitized business operations, the management of the chosen organization has decided to develop a comprehensive online business platform which will provide the best possible outcome to maintain its competitive edge. The customer service department, online order receiving department, finance, and administrative departments, along with marketing and logistics departments, is the departmental wise categorization for Iconic, which needs to be connected with its head office.
In this network circumstances as outlined in the networking assignment, the admin of the ABC Consulting Private Limited has decided to apply the core as well as the fundamental concepts of VLAN over the network. Each department of the selected company will comprise of a single VLAN, which will have the option to communicate both with the other departments along with the head office. After configuring the process of departmental wise VLAN network framework, the subsequent set of activity, which the admin need to perform, is to develop a Virtual Private Network (VPN) configuration, which will result in the direction towards maintaining an optimum network level with the head office by ensuring the adequate security measures [2].
The proposed network by the admin of ABC Consulting Private Limited will have the best use of different kinds of networking peripherals to meet the current network credentials in the required manner. This will have the choice to provide the option for both the wired as well as the wireless network framework, where all the employees’ departmental wise will be able to connect their devices to the network along with their work stations to complete all the necessary back end operational activities for proceedings. Additionally, it is also specified in the networking assignment that the admin needs to configure the network mechanism, inter VLAN Routing over the network, to divide the broadcast domain in a LAN environment along with setting up a VPN Network for the connectivity with the HQ with required security credentials.
Current network functionality with best possible Mechanism
|
VLAN Configuration: It is the primary activity for the network admin with the view towards connecting all the departments for the selected brand Iconic. This will provide the option to make the required network segment and will address scalability and ensure the proper network management [3]. |
|
Inter LAN Routing Configuration: With the view towards developing adequate interconnectivity over the network, it has become necessary for the administrator to configure the idea of inter VLAN Routing, which will ensure and maintain the required connectivities in the direction towards forwarding traffic and data between different VLANs by configuring a dedicated router over the network framework [4]. |
|
VPN Configuration: In these circumstances of networking assignment, the final job for the network administrator is to configure VPN for maintaining the essential connectivity with the head office. The process will extend the private network across the public network over the use of the internet. It will allow all the employees for Iconic to send and receive data across the shared networks directly connected with the company's private network. |
Network Hardware Composition
|
Hardware Composition and Requirements |
|
|
Routers |
2 |
|
Switches |
5 |
|
Wireless Access Points |
3 |
|
Work Stations |
25 |
|
Firewalls |
3 |
|
Cables and Connectors |
As per the requirements |
Network Topology (Expected)
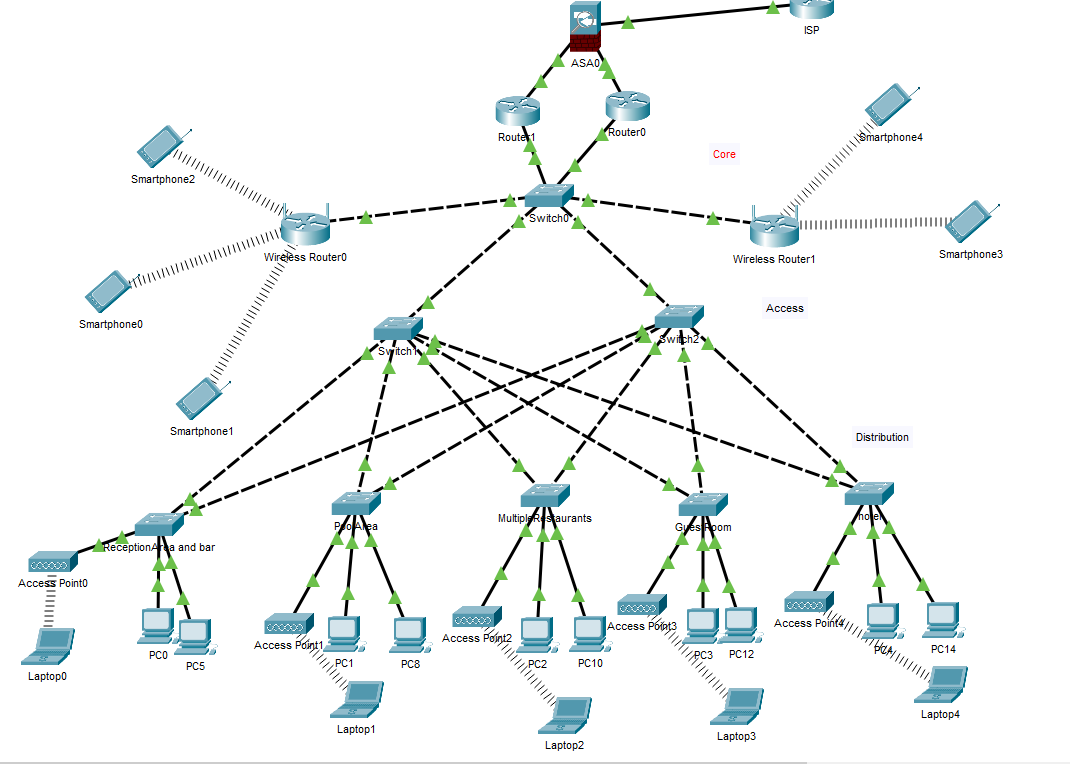
Task B: Describing TCP/IP module with its functional protocol
Defining TCP/IP Protocol: According to the research on networking assignment, the concept of TCP/IP over any kind of particular network defines a set of rules, where the functional, as well as the operational activities of the internet activities, along with its connectivities, are performed over different layers [5]. It is one of the best forms of a routable protocol, which maintains various kinds of network layer-wise segmentation applied on the internet based on similar computer networks and connectivities. The layer-wise segmentation of the TCP/IP stags is classified as follows, which comprised of five functional layers with its operating activities.
|
The Application Layer |
|
The Transport Layer |
|
The Network Layer |
|
The Data Link Layer |
|
The Physical Layer |
Each layer of the TCP/IP framework outlined in the present context of networking assignment maintains physical standards, network interface, transformations along with internetworking activities. All of these layers support different kinds of core functionality based on the operational activities of quite a few protocols, which provides quite a few interactive modules.
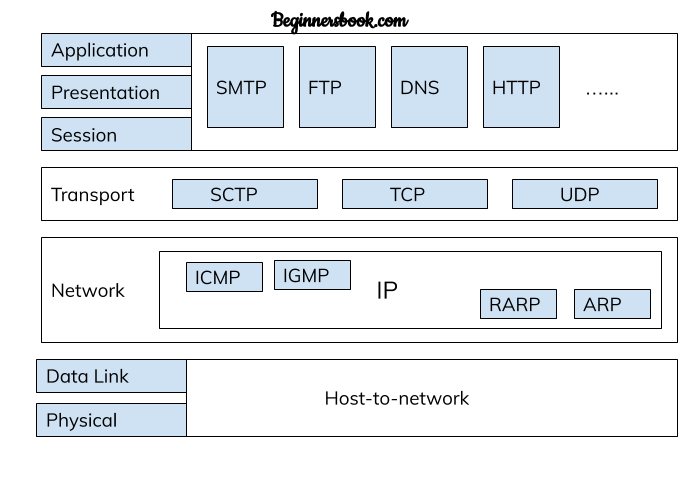
Figure 1: TCP/IP Framework
What are the functionalities of protocol with each layer defined in the networking assignment?
The concept of the TCP/IP network stag defines as a whole evolves vast as well as comprehensive platforms, where a range full of networking activities are performed maintain intact connectivity of the moving segments. However, in this current scenario, the role of the working protocols proved to be essential, where the functionalities based on layer wise segmentations are discussed within this networking assignment:
Network Access Layer
The network access layer is the last layer of the TCP/IP connectivities, which combines the grouping activities of the physical layer as well as with the data link layer. The segment, in particular, is responsible for developing the data transmission mechanism over the network between all the connected diverse [6]. The process as a whole defines the form of encapsulating the IP datagram into frames, which are transmitted over the system by mapping the IP Address framework with the required set of connections [7].
Functional Protocol in Network Access Layer is as follows:
|
Ethernet |
|
Token Ring |
|
FDDI |
|
X.25 |
|
Frame Relay |
Internet Layer
Internet Access layer defined the 2nd layer of the TCP/IP suite, where its functional ability describes the process to send the required data packets over the network by selecting the best possible path [8]. There is a range of protocols, which are operated in the selected layer, and some of them are discussed in the subsequent part.
List of the protocol used in the Internet Layer is as follows:
|
IP Protocol |
|
Address Resolution Protocol (ARP) |
|
ICMP Protocol |
Transport Layer
As per the investigation on networking assignment, the notion of the transport layer comprised in the direction towards performing the operational activities based on the TCP/IP module [9]. The mechanism of the transport layer protocol defines the context, which mainly framed in the direction towards maintaining the required flow control along with the correction of the data framework.
List of the protocol used in the transport layer areas:
|
User Datagram Protocol (UPD) |
|
Transmission Control Protocol (TCP) |
Application Layer
The selected layer in this segment of networking assignment is one of the most specific segments in the TCP/IP protocol suite, which maintains a wide range of networking activities, which are performed with the view towards preserving the required network functionalities [10]. It is the highest layer of the framework and, most importantly, enhances the users to develop intact and core communication options.
The lists of the functional protocol are as follows:
|
Telnet |
|
SNMP |
|
SMTP |
Task 3: Evolving and identifying the segment wise security requirements
The possibilities of the external attacks, as well as security vulnerabilities, remain all the time high measured with different kinds of network credentials [11]. Based on the selected network circumstances, the concept of the TCP/IP Network framework will define the best possible set of rules and faces quite a few ranges of attacks and security vulnerable discussed in the following part of the networking assignment:
Potential Application Layer Threats and Security Issues with Solutions over TCP/IP:
|
The notion of the SQL Injection is one of the potential threats that occur in the application layer resulting in sensitive data loss over the network framework in the mode of unauthorized transactions. |
|
The best solution for the identified issues where the network admin needs to perform the Snort, which will implement effective detection measures for SQL Injection over the network [11]. |
Potential Transport Layer Threats and Security Issues with Solutions over TCP/IP:
|
The port scan attracts one of the most popular networks vulnerable, which takes place over the transport layer resulting in the direction where the attackers try to find newer ways towards breaking into the framework [12]. |
|
The network admin needs to install the required firewall option and setups in the direction towards applying the concept of the intrusion prevention system (IPS) over the set of connections. |
Potential Network Layer Threats and Security Issues with Solutions over TCP/IP:
As stated in the networking assignment, it is essential to restrict the possibilities of getting SYN Flooding/ Denial of Service attack over the network layer protocol, where the attackers send SYN requests over the network, which makes the entire network functionality unresponsive and affects the functionality of the selected contract [13].
In current networking circumstances, the admin needs to install a network firewall, which will act as a primary line of defence by providing adequate filtering options for SYN possibilities.
Potential Data Link Layer Threats and Security Issues with Solutions over TCP/IP:
|
The possibilities of Media Access Control (MAC) Address Spoofing remain all the time high in the selected layer. In this network circumstances as explored in the context of networking assignment, the attackers try to overwrite the CAN entry table in the network framework, which mainly affects the forwarding frames over the network connectivities. |
|
The role of installing intelligent WLAN over the network will provide an adequate solution for the network admin to detect the selected vulnerable over the set of connections [14]. |
Potential Physical Link Layer Threats and Security Issues with Solutions over TCP/IP:
In this scenario of networking assignment, the physical damage or network getting unplugged are the two possible threats in the selected layer of TCP/IP Stags [15].
In these networking circumstances, the role of the administrator is to keep all the connected networking devices as well as protected in the office, by using the best possible network cables and connectivities.
Summary of the Report on networking assignment
The findings of the current report on networking assignment illustrated and developed the required network framework, which proved to be very much essential in the direction towards meeting the expected as well as the current outcome. There are three major classifications of the study developed in this networking assignment, done in the best possible manner, which defined the network framework of the selected organization the Iconic (Online Fashion Retail Brand), along with conceptualizing the working and functional proceedings of the TCP/IP Stags with its potentials threats and vulnerable with adequate solutions.
Reference List
[1] L. Zhang et al., “Named data networking,” Comput. Commun. Rev., 2014, doi: 10.1145/2656877.2656887.
[2] M. Stojanovic and P. P. J. Beaujean, “Acoustic communication,” in Springer Handbook of Ocean Engineering, networking assignment 2016.
[3] P. W. Cardon and B. Marshall, “The hype and reality of social media use for work collaboration and team communication,” Int. J. Bus. Commun., 2015, doi: 10.1177/2329488414525446.
[4] M. S. Balaji, K. W. Khong, and A. Y. L. Chong, “Determinants of negative word-of-mouth communication using social networking sites,” Inf. Manag., 2016, doi: 10.1016/j.im.2015.12.002.
[5] T. Guelzim and M. S. Obaidat, Handbook of Green Information and Communication Systems. 2013.
[6] W. Xia, Y. Wen, C. H. Foh, D. Niyato, and H. Xie, “A Survey on Software-Defined Networking,” IEEE Communications Surveys and Tutorials. 2015, doi: 10.1109/COMST.2014.2330903.
[7] A. Mestres et al., “Knowledge-defined networking,” Comput. Commun. Rev., 2017, doi: 10.1145/3138808.3138810.
[8] G. Xylomenos et al., “A Survey of information-centric networking research,” IEEE Communications Surveys and Tutorials. 2014, doi: 10.1109/SURV.2013.070813.00063.
[9] Z. Qin, G. Denker, C. Giannelli, P. Bellavista, and N. Venkatasubramanian, “A software defined networking architecture for the internet-of-things,” in IEEE/IFIP NOMS 2014 - IEEE/IFIP Network Operations and Management Symposium: Management in a Software Defined World, 2014, doi: 10.1109/NOMS.2014.6838365.
[10] J. Lu and D. Churchill, “The effect of social interaction on learning engagement in a social networking environment,” Interact. Learn. Environ., 2014, doi: 10.1080/10494820.2012.680966.
[11] K. Benzekki, A. El Fergougui, and A. Elbelrhiti Elalaoui, “Software-defined networking (SDN): a survey,” Secur. Commun. Networks, 2016, doi: 10.1002/sec.1737.
[12] R. Knopf, “Collaboration and Technology,” in The Director as Collaborator, networking assignment 2018.
[13] L. J. Orchard, C. Fullwood, N. Galbraith, and N. Morris, “Individual differences as predictors of social networking,” J. Comput. Commun., 2014, doi: 10.1111/jcc4.12068.
[14] D. Saxena, V. Raychoudhury, N. Suri, C. Becker, and J. Cao, “Named Data Networking: A survey,” Computer Science Review. 2016, doi: 10.1016/j.cosrev.2016.01.001.
[15] O. Bello and S. Zeadally, “Intelligent Device-to-Device Communication in the Internet of Things,” IEEE Syst. J., 2016, doi: 10.1109/JSYST.2014.2298837.












