Network Security Assignment: The UK NHS WannaCry incident
Question
Task
In 2017 the UK’s National Health Service (NHS) fell victim to the WannaCry ransomware worm. The incident had a significant impact and was reported on significantly, both in the media and in the UK parliament. The NHS WannaCry attack is a high-profile incident that has many intricacies and still has many questions unanswered. It was a cyberattack that appears simple at a first reading but has many complex underlying issues when investigated deeper.
In a network security assignment report consisting of 2500 – 3000 words you are to analyse the NHS WannaCry incident in three main sections.
Section 1: What happened?
In this section you should look at the events that occurred when the NHS was infected with the WannaCry worm. Some questions that would be useful to ask yourself when looking at this section could be:
- What is WannaCry?
- What devices did the worm affect?
- What was the impact the worm had on the NHS?
- What was the aftermath of the infection?
- What does the NHS incident demonstrate about the importance of Network and Cyber-Security?
Section 2: How did the infection happen?
In this section you will need to look at the situation that allowed the worm to infect the NHS. There were technical, social and political factors that contributed to creating the environment that created the vulnerability that would be exploited.
- What were the circumstances that contributed to enabling the worm to infect the NHS?
- Who was the threat actor? What evidence was there for this?
- What was the exploit used?
- What was/were the attack vector(s)?
- Why was the attack vector available?
Section 3: What should have been done?
Finally, what should have been done? From your analysis you should provide your insight and recommendations as to what should have been implemented to prevent or mitigate the events that occurred. Some points you may wish to consider could be:
- What should have been done, technically, socially or politically (including policy)? What are the lessons that can be learned from the NHS incident?
- What technical solutions should have been implemented and why? Why should the NHS have known to have implemented these?
- What action should have been taken to protect the NHS from infection?
- Were these actions already known?
- If so, why weren’t they taken? If not, why were they not foreseen?
- What needed to change? Could these changes have been made in 2017?
Answer
Section 1: What happened?
What is Wannacry?
It is stated in this network security assignment that the lethal chain WannaCry may be divided into three primary components:
The first part is the worm element used by WannaCry to propagate to other systems. This activity extends further than the local area network and then also tries to distribute the virus across the internet to random IP addresses. This is achieved by exploiting a Microsoft SMB communication vulnerability that Windows users commonly utilise to move data between machines. This feat, dubbed EternalBlue, is a pirated piece of property: A gang that dubbed itself the 'Shadow Brokers' obtained and subsequently disclosed the vulnerability purportedly born of the NSA (Adams, 2018).
The vulnerability enables WannaCry to automatically copy and execute on distant systems. Notably, 2 months before the assault, Microsoft published a fix for this vulnerability, however at the time the consumers had not upgraded their machines (Akbanov et al., 2019).
The next element is known as that of the "kill switch," a code-line that checks if a certain web domain address is online at the early phases of the assault. If the virus finds the web domain to be live, the assault stops dead.
At the moment of the first assault, this URL wasn't really registered, which ensured that WannaCry could still spread. On 12 May 2017, Marcus Hutchins as well as Jamie Hankins, two British threat analysts bought this domain and successfully ended the WannaCry assault (Coventry, 2018).
What happened
On 12 May 2017, amid a large attack spanning several nations on WannaCry ransomware (otherwise referred as Wana Decrypt0r, WCry, WannaCrypt, as well as WanaCrypt0r) was spotted [12]. Various security vendors data indicate that a total of 300,000 machines have been seriously affected in more than 150 countries. The attack harmed a broad range of industries, including public health, telecoms and gas/oil industry.The challenge in defending WannaCry derives from its capacity to propagate through the use of a worm component onto other systems. This function increases assaults and demands defence measures that can react rapidly and in real time. In addition, WannaCry contains a public-key cryptography-based encryption component. Specifically designed messages can be sent by adversaries to an SMB v1 server, connecting TCP ports 139 as well as 445 of unpatched Windows systems, to a remote script on the affected computers. This flaw particularly affects all unpatched Versions of windows from Windows Xp 8.1, with the exception of Windows 10 (Ghafur et al., 2019).
Devices
WannaCry has brought down a wide variety of medical systems. Several of the larger equipment are using Windows OS — X-ray, cat-scan, MRI as well. However, the pieces that operate the heavy gear generating the scans are typically not controlled by Windows PCs. Many pharmacy systems that supply medicines also use Windows computers which are possibly susceptible (Kim, 2021).
Impact on the NHS and the consequences of the worm?
On 12 May, 45 NHS organisations were originally discovered in England, including 37 trusts affected by the Ransomware attacks (although NHS England initially identified 37 trusts as being infected, three of these were mis-categorised and later re-categorised as not being infected but experiencing disruption). Additional organisations reported being impacted in the days following. In all, 80 among 236 trusts had been impacted throughout England (Martin et al., 2018).
- 34 devices infected and locked (25 were acute trusts);
- 46 never infected but disrupted reporting. For instance, these trusts turned their e-mail as well as other services down as a precautionary and by themselves
Thousands of appointments as well as surgeries have been cancelled and patients must continue to go to accidents and emergencies in five locations. NHS England recognised 6 912 cancelled consultations and projected that a total of more than 19,000 were cancelled depending on the standard rate of first-appointment follow-up visits.
Costs include: cancellation of appointments; additional IT help from local NHS organisations or IT advisors; or costs of restoration of attack-affected data and systems. During the weekend of 13-14 May, locally and nationally NHS employees tried to fix difficulties, including preventing the fresh wave of institutions impacted by WannaCry Monday 15 May.
Importance of Protection
Effective network security strategy is designed to identify security concerns, possible attackers, required levels of protection, and network vulnerabilities. The measures to be taken throughout this study project are to understand the makeup of a secure network, Web or otherwise (Mayor, 2018).
There are numerous products available to reduce the computer's susceptibility to the network. These technologies include encryption, security mechanisms, penetration testing, firewall security administration. Companies across the world use a mix of these tools.
"Intranets" are also both linked to and sufficiently secured against the internet. The architecture of the Internet itself contributes to network vulnerabilities. Addressing the security problems of the Internet substantially contributes to the development of new security technology and network techniques with internet as well as internet security.
- Builds confidence - Safety for huge systems is security for everybody. Network security increases customer confidence and protects your organisation from the reputational and legal consequences of an infringement of security.
- Risk mitigation - The appropriate network security services help the organisation to remain in compliance with the laws of the company and government and minimises the business and financial effect of a breach.
- Protects details about ownership - To secure company's sensitive information, business customers rely upon the business. The company also depends on the same protection. The security of the network assures the safety of network-wide information and data exchanged.
- Improves operation - A cleaner and much more simplified network seems to be more productive, effective and easier to operate.
- Improves compliance - Most organizations now have some kind of regulatory organisation that sets cybersecurity regulations and standards. Improving the security of your network increases your compliance efforts (Pieters-James, 2017).
- Minimizes disaster data events - It is reiterated that a strong network security system with several methods from day one is excellent practise.
Section 2: How did the infection happen?
Circumstances
Although this WannaCry cyber strike did not directly target the NHS, it revealed weaknesses in England's NHS. It highlighted the need to enhance throughout the NHS, including enhanced cyber security discipline as well as accountability at senior level and on board levels, the significance of quick and efficient system patching when additional security notifications are published, and historic network security underfunding and up-to-date software. WannaCry's ransomware component has already been detected but many endpoint (anti-virus) companies had not been protected owing to its small volume. In addition, neither of the 80 NHS institutions impacted by WannaCry had implemented the NHS Digital Care CERT bulletin's updated patch recommended by Microsoft on April 25, 2017 after the receiving of intelligence first from BT on April 24, 2017 of something like a specific danger. It was indeed a Microsoft Windows exploit that did not attack outdated software. Most of the affected NHS devices run the authorized but unsecure Microsoft Windows 7 OS. Unsubstantiated devices (XP devices) have been in the fraction of infected devices and in the previous 18 months, the number of infected machines fell from 18 percent in January 2018 to 1.8 percent (Pieters-James, 2017). Wikileaks published in April 2017 this cache collection tools and vulnerabilities, after exchanging them among organisations like Apple and Microsoft, so that they can build patches for these vulnerabilities. Microsoft published a fix in March of 2017 to end this vulnerability, however only a tiny proportion of Windows customers keep their computers updated with the most recent updates owing to pirates and low level of awareness. This absence of best practises on safety is the primary reason of the attack's fast spread and deadly consequences, as seen below (Pieters-James, 2017).
Origin
The attack was carried out using Eternalblue, the term given to Ms Windows OS security flaw, using Microsoft Server Message Block (or SMB) 1.0. A network file sharing protocol would be the Server Message Block (SMB). It 'allows computer programmes to read as well as write files and obtain support' on the very same network. Paradoxically, it was supposedly designed by the US National Security Agency like a cyber offensive operation. Even though they have learned of the weaknesses in the programme, the NSA has not brought it to the attention of Microsoft till the hacker organisation, Shadow Brokers, released EternalBlue onto a dark web website. Another study of the attack by businesses including Symantec identified ties with the Lazarus gang, which in turn were linked to N. Korea while the attack did not carry the characteristics of the nation-state operation (Pieters-James, 2017).
Exploit
The vulnerability (Eternal Blue) aims at the server message block (or SMB) as stated earlier which allows an attacker to run their malware on a machine remotely. This has two major ways, both of which use computer ports, in this instance TCP 445, which enable computers to interact. Without diving into technology, the initial vector of invasion is connected to the internet through an open port 445. It is common to shut all SMB ports facing the internet externally, as they generally include internal networking. A machine is infected to find random IP addresses in the port to identify the SMB vulnerability. If detected, it will try to exploit and spread.
Vector
WannaCry exploit weaknesses in the Windows SMB to allow spread following a presence in an environment. This dissemination technique can propagate the virus both over the affected network as well as the public internet. This exploit is called "EternalBlue" as well as the Shadow Brokers has disclosed it. Microsoft MS17-010 has fixed the exploited bug (Ghafur et al., 2019).
The virus generates two threads based on the gathered data. The very first thread lists the network interfaces and decides on which subnet the machine is located. The virus then produces a thread on the network for each IP. Each thread attempts to link to the IP over TCP port 445 then tries to use the system if it was successful. The following figure shows an example of an effort to abuse a remote server.
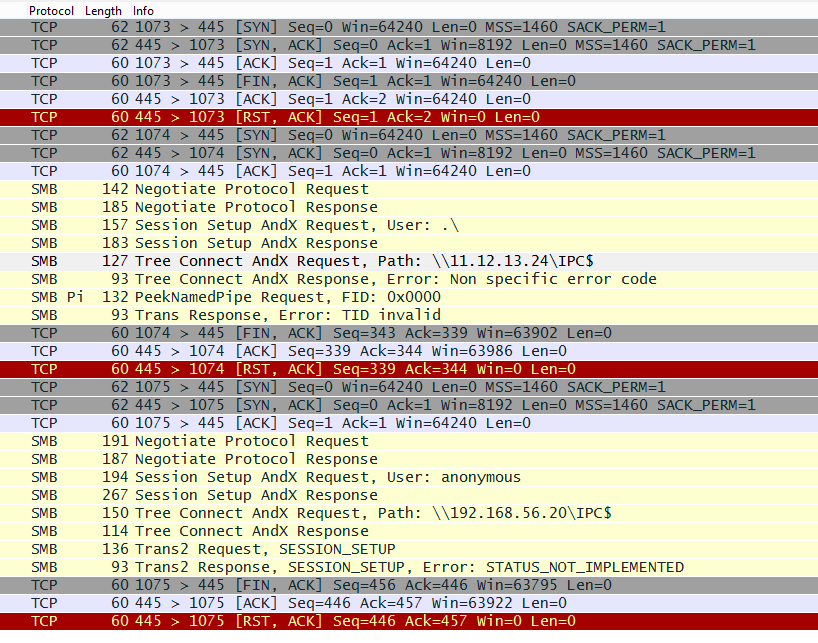
Why vulnerability exists
The SMB is the transportation protocol used mostly by Windows PCs for a broad range of functions, including file sharing, able to share of printers as well as access to distant Windows services. TCP ports 139 and 445 are operated by SMB. MB supports what is known as SMB interactions. With SMB transactions, simultaneous reading and writing here between SMB server and the client is possible. If the messaging request is larger than the SMB MaxBufferSize, then rest of the data are transmitted as secondary Trans2 queries. This issue affected the kernel driver srv2.sys and is caused by incorrect Secondary Trans2 requests (Ghafur et al., 2019).
Section 3: What should have been done?
Wannacry methods for prevention and mitigation
Changes in policy level (Political and Social)
- Download backups: The most efficient way of thwarting ransomware is to back up data files on a regular basis and monitor network restoration operations.
- Education of users on the network: Like other viruses, ransomware frequently infects a machine through e-mail contents, transfers or web surfing cross-scripts.
- Traffic network monitoring and inspection: This phase will help to discover anomalous traffic linked with ransomware behaviour.
- Using threat intelligence of data feeds: This very technique can help discover threats more quickly (Trautman & Ormerod, 2018).
- Restrict payload execution: Ransomware frequently runs under well-known directories of the operating system. If those same folders cannot be reached by ransomware because of access control, harmful data encryption risks can be stopped.
- Restrict administrative as well as system access: Certain ransomware variants are intended to run default accounts. This form of ransomware can offer further security by renaming basic user profiles and deactivating any unneeded, privileged and unprivileged accounts.
- Terminate local administrative rights: avoid ransomware functioning on the local system as well as stop spreading it on the basis of administrative powers. Deleting local administrator rights also prevents access to vital system resources and data which ransomware encryption attacks.
- Additional procedures linked to permission: Consider reducing user-write privileges, prohibiting user directory execution, identifying programmes and restricting network storage or sharing access. Certain ransomware demands written permission to install or operate particular file locations. Limiting written access to a restricted number of folders may interrupt some Ransomware versions (for instance, My Documents as well as My Downloads). The deletion of execution permissions from such folders can also block Ransomware executable code. Many businesses employ a restricted number of business apps. Non-whitelisted apps, including wannacry, can be prevented by establishing a whitelist only program policy. Another practise of authorization is to log in to resource sharing such as networked folders (Trautman & Ormerod, 2018).
- Maintaining and updating software: The maintenance and upgrading of software, in specific operating system patches, security as well as anti-malware, is yet another essential guideline in guarding against malware.
Malware Protection (Technical)
Security Automation
Organizations should consider utilising OS and application configuration control lists to help administrators secure hosts consistently and effectively. Security Automation techniques can utilise checklists to implement default security configuration settings and to monitor the hosts' settings continually to ensure that they still comply with the checklist settings. Organizations must also consider utilising OS and app patching security automation technologies—detecting, acquiring, distributing and installing security-related updates to reduce patching vulnerabilities. Organizations must apply sound host hardening concepts in terms of security settings. For instance, companies should adopt the idea of less privilege, which refers to the establishment of hosts to provide the users, processes and hosts the minimum needed permissions (Ghafur et al., 2019). The less privilege can be useful in reducing malware problems, because malware frequently requires administrator rights to properly exploit vulnerabilities. If such an incident happens, it might reduce the amount of harm the virus can do previous application of less privilege. Organizations also must take other system hardening steps to further decrease the risk of malware occurrences.
Host Hardening
Host hardening must also encompass programmes that are commonly targeted by malware such as email services, internet browsers and word processing. Organizations must deactivate the unnecessary features and capabilities of these apps, especially those often used by malware, to reduce potential malware attack vectors. One would be the use of macro language groups by word processing software and tablet pcs; most common macro-safe applications provide macro security mechanisms that only allow macro-specific places or notify the user to approve or refuse every macro endeavour and thus reduce the likelihood of macro-related malware infection. Another instance is to restrict the installation of software within internet browsers by setting browsers so that plug-ins are prohibited or that users can promptly accept the installation of every plug-in.
Threat Mitigation
Organizations should mitigate the risk of detecting and stopping malware until it can harm their objectives.
Although nearly all vulnerabilities on something like a host have indeed been mitigated, mitigating threats is still crucial—for example, in blocking instances of infection that do not take use of vulnerable vulnerabilities, including such social engineering assaults to lure people in harmful files. Threat mitigation is especially crucial when an organisation is expected to be attacked by a large new threat soon and the business doesn't even have an acceptable alternative to reduce exposure. For example, a fix for a new threat may not be available.
Specific Prevention Measures against WannaCry
- Patch and upgrade existing systems or take a virtualized patching solution into account.
- Activate the intrusion detection / prevention tools along with local firewalls.
- Analyze and verify traffic from and into the network proactively.
- Implement security procedures that may be used by other entry points adversaries, including such email as well as websites.
- Deploy app security to stop malicious activities from being executed over the behavioural monitoring system, which might also prevent undesirable system changes.
- Use classification of data and network separation to prevent additional exposure as well as data loss.
- Disable SMB (v1) for susceptible devices either using GPO or Microsoft guidelines.
- Ensure that almost all the newest patches (if feasible by utilising a Virtual Patching method) are deployed to the computer systems concerned, in particular those relating to MS17-010.
Other prevention measures
- Major email providers feature a component called "rules," where users or the administrator may filter and limit questionable correspondence.
- Require authentication methods (MFA) or another robust user authentication methods for accessing websites and apps. The layered protection helps to guard against numerous dangers.
- Patch. Keeping software for their latest versions is nothing new, but software in the production system continues to be obsolete and often outdated for years. It is vital to also have a full program to evaluate any outdated or insecure system software and also have a validated method to correct any results.
- It is important to implement an effective Web Application Firewall ( commonly known as WAF) to check HTTP traffic regardless of the type of the company's website.
- The multi - layer security approach will also be enhanced by establishing an IDS and hardware firewall.
User privileges –
The reality is that most malware requires admin credentials just to launch. If users lower an user's privilege to normal users, ransomware trying to install a firm foothold is typically dealt with since there are no permissions to download files, programs, or perhaps even touch the registries, except if it uses a vulnerability to increase privileges (Ghafur et al., 2019). This is a solid mitigation technique for the overwhelming bulk of malware that has a mechanism to infect files.
Summary
During the analysis, significant traits and behaviour of WannaCry were uncovered. We detected in particular Tor Addresses, TCP and DNS links observed, SMB samples as well as activities relating to persistence and obstruction of WannaCry.
The WannaCry worm component has been armed with a feature to exploit and spread through Microsoft's MS17-010 targeting unpatched computers by sending SMB testing sessions on port 445. In conjunction to the modular structure of WannaCry, RSA keys for decrypting the infected DLL necessary for the encryption component had also been included. The results of the investigation might be utilised to develop effective mitigation techniques for WannaCry as well as other ransomware groups with similar behaviour. Sdn is a new customizable network architecture that disconnects data and control planes. SDN controllers keep an eye on the whole network and take policy choices. On the other hand, every device on the data plane has one or maybe more flow tables in which the rules for packet processing are recorded. This alters the way connections are designed and operated and allows new security mechanisms based on SDNs.
References
Adams, C. (2018). Learning the lessons of WannaCry. Computer Fraud & Security, 2018(9), 6–9. https://doi.org/10.1016/s1361-3723(18)30084-8
Akbanov, M., Vassilakis, V. G., &Logothetis, M. D. (2019). WannaCry Ransomware: Analysis of Infection, Persistence, Recovery Prevention and Propagation Mechanisms. Journal of Telecommunications and Information Technology, 1, 113–124. https://doi.org/10.26636/jtit.2019.130218
Coventry, L. (2018). One year after WannaCry: assessing the aftermath. Network Security, 2018(5), 1–2. https://doi.org/10.1016/s1353-4858(18)30037-0
Ghafur, S., Kristensen, S., Honeyford, K., Martin, G., Darzi, A., & Aylin, P. (2019). A retrospective impact analysis of the WannaCry cyberattack on the NHS. Npj Digital Medicine, 2(1). https://doi.org/10.1038/s41746-019-0161-6
Kim, S. H. (2021). U.S. Cybersecurity Governance and North Korea Coping with the WannaCry. Network security assignment East and West Studies, 33(2), 191–217. https://doi.org/10.29274/ews.2021.33.2.191
Martin, G., Ghafur, S., Kinross, J., Hankin, C., & Darzi, A. (2018). WannaCry—a year on. BMJ, k2381. https://doi.org/10.1136/bmj.k2381
Mayor, S. (2018). Sixty seconds on . . . the WannaCry cyberattack. BMJ, k1750. https://doi.org/10.1136/bmj.k1750
Pieters-James, L. (2017). Does your Cyber Security make you WannaCry? Journal of Forensic Sciences & Criminal Investigation, 5(3). https://doi.org/10.19080/jfsci.2017.05.555663
Popli, N. K., & Girdhar, A. (2017). WannaCry Malware Analysis. MERI-Journal of Management & IT, 10(2). https://doi.org/10.25089/meri/2017/v10/i2/151167
Trautman, L. J., & Ormerod, P. (2018). Wannacry, Ransomware, and the Emerging Threat to Corporations. SSRN Electronic Journal. https://doi.org/10.2139/ssrn.3238293












