Information Technology Assignment: Designing A Secure Blockchain-Based Access Control For IoT Enabled Drones
Question
Task:
Write a project proposal on information technology assignment on the topic “Designing a secure blockchain based access control for IoT enabled drones”.
Answer
Abstract
As evident herein information technology assignment, in recent times usage of drones have become more popular from civilian to military usage and these drones and these UAVs communicate with each other and generate crucial information which is connected to ground station servers which is the central authority to control all the drones and these drones can be easily hacked since the drones communicate through open channels. So, there is a need arises for designing an access control scheme for securing the communication among drones and between drones and ground station server. So, in This paper I would like introduce a Block chain-based access control scheme for IoT enables Drones by cloud server connected with GSS which secures the data gathered by GSS.
introduction
The recent times has seen a technological advancement in the field of internet of things (IoT). The field mainly deals with the process of interconnecting various devices among one another with the help of internet connectivity [1]. The 2nd part in the use of such devices is the collection of various types of data from the different devices and analysing them to create meaningful insight which can later be used by individuals or my any organisation. The IoT devices are categorised into two broad groups where one consists of physical objects such as vehicles, smartphones, drones, etc. and the second group consists of virtual objects like e-wallets and e-tickets [2]. The advantage of using such IoT devices is in the advance data collection process that they hold which does not require any form of human interaction. This research has been targeted for the understanding and preliminary development of an IoT enabled drone which will be able to work with a secure block chain based access. The system would be able to provide mutual authentication between neighbouring drones. The data is then collected and shared.
The research project has been outlined in this paper to provide a clear understanding of the project that is to be done [3]. At the time of writing this proposal, several weeks has already been spent on collection of information from various sources to understand the working of the different parts of the research topic. The information collected has been briefly discussed in the following sections. The paper further discusses about the type of research that is to be conducted for the completion of the project and the research plan that is to be followed in order to complete the project on time.
Background
Recent development in the research domain of IoT devices has sparked the use of internet of drones (IOD) which has been a huge impact in various industry both for the civilian use as well as military applications. A drone is defined as an “unmanned aerial vehicle” (UAV) which can be both human controlled through radio signals or can navigate freely with the help of computer chipset on-board [4]. A drone is fitted with a number of different IoT devices such as radio detection and ranging controller, sonar pulse distance sensor, time of flight sensor, thermal sensors, etc. Even when the drone is being used to complete some other task the data from these sensors are collected and shared with the control centre in order to determine the flight route and style for future drones [5].
Research has shown that security and privacy issues are the most essential issues in Internet of Drones (IoD) environment. In order to secure an IoD environment different techniques has been proposed. Recent research shows that there is a probable combination of block chain and other cryptographic techniques has been found to provide higher security protection against all forms of passive attacks [6]. Addition of new drones in the previous network is essential to be implemented with the help of block chain-based access control. An access control can be made with the inclusion of a certificate as well as with the exclusion of a certificate for an IoT environment. This proposal discusses about the process of combining block chain algorithm in order to provide access control to an IoD environment.
Some of the most notable application of such a drone-based system are in the civilian use as well as in military. Many organisations are currently working in developing prototypes which would be able to complete a number of different tasks so that human interactions can be minimized. Amazon are currently developing drone-based package delivery service which would be able to deliver a product purchased from their website to the consumer’s doorstep with the help of a drone. The current scenario is under research in order to perfect the system and also safeguard the drones from malicious attacks and other attacks from outside. With the rise in home delivery of foods it has been found that faster delivery is always preferred by the consumer. The similar drone system can be used to deliver food from the restaurant to the consumer’s doorstep faster than the delivery service by avoiding huge traffic. In the field of military development of a country the drones are being used to perform unmanned surveillance of enemy ground before launching an attack. The current drones are human controlled which pick up images from the enemy territory to be shared with the military base in real time. The drones once developed can be used to launch remote attacks on the enemy as well as help in diffusing bomb and land mines easily. This would in reduction of loss of human lives.
Problem statement
The use of block chain-based authentication process would be able to eradicate the issues pertaining to security and authentication of drones and other IoT devices into a wireless network environment. This can be helpful in controlling a swarm of drones with the help of a single wireless network which would be able to complete any form or work in the field of civilian or military.
This research proposal is targeted for the development of a block chain based access control for an IoT enabled drone. The main research is to target the use of a new block chain based access control mechanism which would be able to control the drone. The basic idea would be control one drone and simultaneously add a series of drones to the system which would allow the final result to be a swarm of drones being controlled from a single central node with proper authenticating security.
Literature Review
This section is primarily concerned with the discussion about different theories and literature which has been found across the internet. The basic literature which has been collected pertains to the security protocols of the use of block chain-based connectivity. Authentication and access control have been found to be the topmost security protocol in the IoD environment. This literature study has been completed based on the preliminary papers collected for the completion of the research. A detailed literature review will be shared upon the completion of research.
A simple certificate-based authentication method had been proposed by Zhou et al. [7] which can be used in a wireless sensor network. The approach makes use of ECC technique and the certificates used for the process is issued by trusted authorities. The researchers had then applied the theory of bootstrapping time in order to protect other malicious nodes to join into the network after the deployment of the network.
Huang [8] proposed another access control method with the help of Schnorr signature [9]. This method makes used of expiration time of a connected node to the network. However, Chatterjee et al. [10] was able to discredit this approach by stating that the approach was insecure against the use of man-in-the-middle attack on the network. They then proposed a new algorithm with the help of one-way hash function along with ECC technique which was able to resist most of the malicious attacks on the network as well as man-in-the-middle attack.
Huang and Liu [11] later proposed a certificate deficit control mechanism which was able to work irrespective of a hash chain being present. Kim and Lee [12] later worked on the same algorithm which failed to resist the replay attack method [13]. Moreover, the same scheme was unable to provide support for the process of recreating a finished has chain. Based on these drawbacks Kim and Lee worked in designing a new access control method by the name enhanced access control scheme (EACS). The EACS was able to provide the user with hash chain renewal method. However, in this process Zeng et al. [14] was able to identify that the scheme had two major issues. The first issue was that a new smart device would be able to easily masquerade itself into the network and the second issue was that an already authorized device would be able to launch a masquerade attack on the network.
Li et al. [15] proposed a new access control scheme which was designed with the help of heterogeneous signcryption. Since the use of bilinear pairings and identity based cryptographic technique which makes it heavy computation in term of cost. Luo et al. [16] had also suggested the use of access control approach for wireless network which made use of the same technique like Li et al. [15]. Similarly, there has been numerous other researchers who had proposed the same methodology for the access control method [15 – 17]. In recent years Malani et al. [18] proposed a new approach which makes use of both certificates as well as signature. They were able to deploy the system in an IoT environment.
Wazid et al. [19] in their research discussed about various other techniques and issues related to the security protocol of an IoD environment. They were able to provide a complete taxonomy of the various security protocols which were needed in order to understand security in an IoD environment. Tian et al. [20] was able to design a new privacy preserving authentication mechanism in the IoD environment. Their system was designed on certificate-based signatures and was able to provide four procedures, namely system initialization, IoD join, authentication communication and key and pseudonym update. The join is made in two levels which distinguished drones which share information with the same network from the other drones which do not. The authentication communication helps in establishing mobile edge communication device which helps in maintaining the public key broadcast list. However, the process may seem secure it become computationally heavy due to the implementation of RSA based digital signature authentication approach.
Wazid et al. [21] were able to design a lighter version of user authentication process for the IoD environment. The approach enables the user to access real time data of a designated drone. There is a mutual authentication process which enables the user to access the drone. Srinivas et al. [22] were able to design a new “temporal credential based anonymous lightweight user authentication”.
Based on the study of the above papers it shows that there are various schemes designed for wireless sensor networks and internet of things / drone’s environment to be implemented which will be able to provide the required support for the block chain-based access control mechanism.
Research Questions
In order to complete a research, it is important for the researcher to set forward a set of objectives or questions which would help the researcher to guide them through the research. This also helps in keeping track of the progress of the research as well as provide timely milestones in order to achieve their intended target. The main research questions which can be set forward for the completion of the research are as follows:
- How a block chain-based access control works?
- How to connect a hoard of drones to one another wirelessly?
- How to manage them in a swarm with the help of block chain-based access control?
- D.-R. Berte, “Defining the IoT,” Proc. Int. Conf. Bus. Excell., 2018.
- A. Soia, O. Konnikova, and E. Konnikov, “The internet of things,” in Proceedings of the 33rd International Business Information Management Association Conference, IBIMA 2019: Education Excellence and Innovation Management through Vision 2020, 2019.
- F. Piccialli and G. Jeon, “Special issue on toward the Internet of Things of year 2020: Applications and future trends,” Concurrency and Computation: Practice and Experience. 2021.
- P. Gope, T. Hwang, A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks, IEEE Trans. Ind. Electron. 63 (11) (2016) 7124–7132.
- P. Gope, B. Sikdar, Lightweight and privacy-friendly spatial data aggregation for secure power supply and demand management in smart grids, IEEE Trans. Inf. Forensics Secur. 14 (6) (2019) 1554–1566.
- P. Gope, B. Sikdar, Lightweight and privacy-preserving two-factor authentication scheme for IoT devices, IEEE Internet Things J. 6 (1) (2019) 580–589.
- Y. Zhou, Y. Zhang, Y. Fang, Access control in wireless sensor networks, Ad Hoc Netw. 5 (2007) 3–13.
- H.F. Huang, A new design of access control in wireless sensor networks, Int. J. Distrib. Sens. Netw. 2011 (2011) 7, http://dx.doi.org/10.1155/2011/412146, Article ID 412146.
- C.P. Schnorr, Efficient signature generation by smart cards, J. Cryptol. 4 (3) (1991) 161–174.
- S. Chatterjee, A.K. Das, J.K. Sing, An enhanced access control scheme in wireless sensor networks, Ad Hoc Sens. Wirel. Netw. 21 (1–2) (2014) 121–149.
- H.F. Huang, K.C. Liu, A new dynamic access control in wireless sensor networks, in: IEEE Asia-Pacific Services Computing Conference, APSCC’08, Yilan, Taiwan, 2008, pp. 901–906.
- H.S. Kim, S.W. Lee, Enhanced novel access control protocol over wireless sensor networks, IEEE Trans. Consum. Electron. 55 (2) (2009) 492–498.
- H.F. Huang, A novel access control protocol for secure sensor networks, Comput. Stand. Interfaces 31 (2009) 272–276.
- P. Zeng, K.-K.R. Choo, D.-Z. Sun, On the security of an enhanced novel access control protocol for wireless sensor networks, IEEE Trans. Information technology assignment Consum. Electron. 56 (2) (2010) 566–569.
- F. Li, Y. Han, C. Jin, Practical access control for sensor networks in the context of the Internet of Things, Comput. Commun. 89–90 (2016) 154–164.
- M. Luo, Y. Luo, Y. Wan, Z. Wang, Secure and efficient access control scheme for wireless sensor networks in the cross-domain context of the IoT, Secur. Commun. Netw. 2018 (2018) 1–10.
- A. Braeken, P. Porambage, M. Stojmenovic, L. Lambrinos, eDAAAS: Efficient distributed anonymous authentication and access in smart homes, Int. J. Distrib. Sens. Netw. 12 (12) (2016) 1–11.
- S. Malani, J. Srinivas, A.K. Das, K. Srinathan, M. Jo, Certificate-based anonymous device access control scheme for IoT environment, IEEE Internet Things J. 6 (6) (2019) 9762–9773.
- M. Wazid, A.K. Das, J.H. Lee, Authentication protocols for the internet of drones: taxonomy, analysis and future directions, J. Ambient Intell. Humaniz. Comput. (2018).
- Y. Tian, J. Yuan, H. Song, Efficient privacy-preserving authentication framework for edge-assisted Internet of Drones, J. Inf. Secur. Appl. 48 (2019) 102354.
- M. Wazid, A.K. Das, N. Kumar, A.V. Vasilakos, J.J.P.C. Rodrigues, Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment, IEEE Internet Things J. 6 (2) (2019) 3572–3584.
- J. Srinivas, A.K. Das, N. Kumar, J.J.P.C. Rodrigues, Tcalas: Temporal credential based anonymous lightweight authentication scheme for internet of drones environment, IEEE Trans. Veh. Technol. 68 (7) (2019) 6903–6916.
All these questions were first set forward after conducting the literature review of the topic. The above questions can be considered to be primary objective for the completion of this research which would be completed in the future.
Figure SEQ Figure\* ARABIC 1: Literature map of the research
Proposed Methodology
In order to conduct a research a methodology needs to be followed which would guide the researcher through the process of completing their research. A research can be completed by two ways: primary research and secondary research. Primary research follows the process of development of the project which has been proposed and execute the same in order to collect data which are then analysed and published. The primary research data is authentic in nature which helps in making proper conclusion based on the research. In secondary research the researcher collects data from different sources such as journals, conference articles, websites, etc. which are then studied and an overview of the project topic is reached. This form of research helps the future generation of researchers to understand the work that has been done in a certain domain. However, the conclusion which can be drawn from such a research is often vague and can vary from one researcher to another.
A. Study design
In order to complete the research the use of secondary research has been selected. This process of secondary research works by collecting data from various sources and then compiling them to understand the working of the topic.
B. Roles distribution
During the course of this research the main roles were of researcher and research supervisor. The research supervisor was responsible for providing proper guidance to the researcher during the course of this research study. For this research (name of supervisor), acted as the research supervisor.
C. Data collection methods
In this case the main broad topic to be considered were IoT drones and block chain. So all information related to the two topics were collected separately and then researches were found where the two topics were merged and worked on. The information primarily collected were research papers and journals. The information gathered now needs to be studied and the theoretical analysis would help in paving the path for future working on the same topic. The research papers collected were organised and sorted into different categories on the basis of different labels which helped in the process of making compact literature study in the long run for the research. The papers were then read and the basic theory, working model, algorithm, accuracy and efficiency of the algorithm was collected and noted down. This process helped us in making an overview scenario of the research domain.
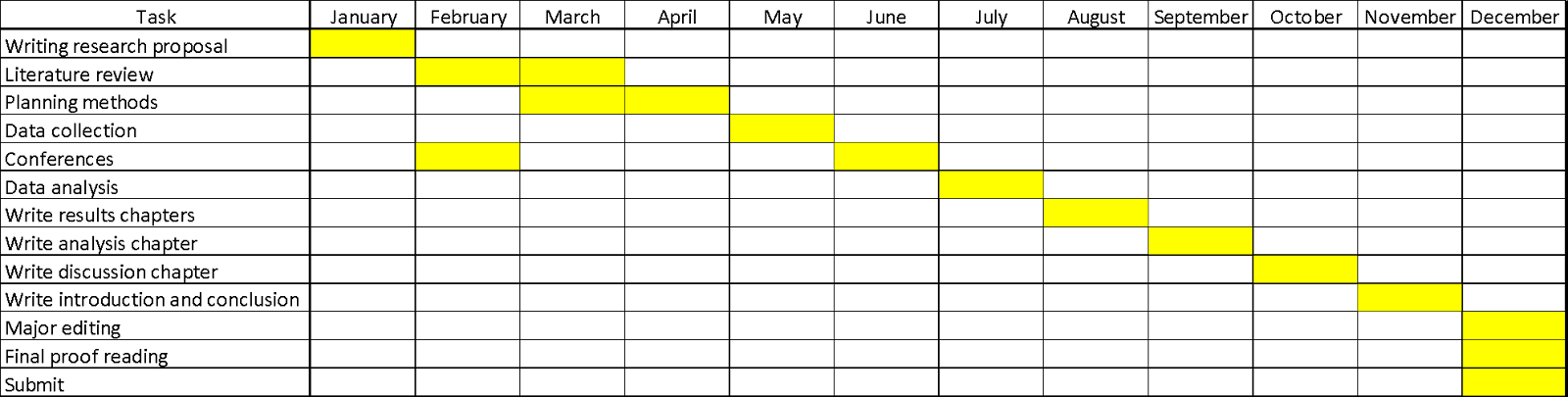
Figure SEQ Figure\* ARABIC 2: Timeline for the completion of the project
D. Quality of data
The data that has been collected and used for the analytics have been sources from reliable publication houses on the internet. All papers have been submitted to reputed journals with high impact factor and conferences. The quality of the data was given the highest priority as this would be the base of our research in the upcoming days. Being the primary source of information and data care was taken while collecting all the papers from the internet.
E. Ethical issues
In order to collect and share the research conducted all forms of ethical considerations were taken into account and all sources has been referenced correctly. However, since the work being compiled for this research is in the form of secondary research there is minimal requirement for the maintenance of ethical standard for the data being collected.
Research Plan
In order to complete the project within a stipulated time the following plan has been set forward which would help in keeping with the flow of the work. The limited knowledge of such project topics renders the researcher to lag behind on the work progress if they do not adhere to a fixed schedule with proper milestones for the project. The timeline for the completion of the project has been shown in figure 2.
References












