Information System Assignment: Developing Biometric-Based Secure Attendance System
Question
Task:
To prepare this research paper on information system assignment, select an area that interests you in the area of Advanced Database Development that you are going to research.
You must describe your proposed research goal so that it can be understood by the reader as to what it is and why it is valuable.
Detail how you are going to approach the research: an analysis of the topic that describes the concept, evolution, future, ideas behind it, importance, strengths, weaknesses and so on.
Answer
1. Introduction
The attendance recording system of students has also changed a lot over the years. It used to be recorded manually in the past. However, with technological development, the attendance recording system has also gone through some revolutionary changes. It has become troublesome for the professors to manage the attendance during the class. Additionally, the error is also caused due to manual computation and it takes a lot of time as well. For this stated reason, an efficient biometric attendance management system will be designed so that attendance can be registered electronically without any error. The biometric system registers attendance with the tip of a fingerprint and records it in the database. Attendance is marked only after the student verification. This research paper will present the concept of applying biometric technology to identify students and record their attendance in a very smooth manner. This research paper will also theoretically evaluate the biometric concept and present the software development life cycle of the biometric registration.
A. Background
Biometric refers to human Identification by their personal physiological traits. Biometric is also capable of identifying an individual from a group of people. It is a distinctive measurable trait that can describe people by measuring the physiological characteristics of the body (BELLO et al., 2017). Many teachers must have experienced a situation where the students give attendance to their friends who are not present in the class. To stop this forgery and to reduce error in the computation of attendance percentage biometric system is the only and the most ideal option since physical traits like fingerprint shapes, Iris is something impossible to copy. Hence this medium of registering attendance is used here.
B. Problem Statement
The traditional method of registering the attendance of the students hasn't been very efficient. However, with the advancement of technology, the traditional method has struck to become obsolete. There are a lot of issues associated with it. For example, with the increase in student numbers, names on the sheet increase. Keeping these registers for a long period is not easy as flood or termites or fire can easily destroy these sheets (Unal and Tecim, 2018). Forgery or impersonation in the attendance sheet is another key problem with the traditional system. Sometimes the attendance sheet gets lost or misplaced. These are the issues associated with the traditional system.
C. Aims and Objectives
The aim of this research paper is to develop a biometric-based secure attendance system.
Objectives
The Objectives of this research work are:
- To provide an errorless biometric attendance system for students
- To theoretically discuss the software development life cycle models of the biometric system
- To provide a suitable methodology
D. Research Questions
This research paper will answer some of the key research questions that are as follows:
- What is a biometric system
- What are the different stages of implementation
- What are the pros and cons of a biometric system
- What is the accuracy rate of the biometric-based Identification system
- How can it help the educational sector
E. Significance of the Study
The proposed system will be of immense importance as it can lead to the lesser time taken for attendance. Implementing the biometric attendance system has a number of benefits like 0 wastages of time for roll call, 0 risks of loss of attendance sheet and reduced threat of forging.
I. LITERATURE REVIEW
It is important to have robust design models to develop quality software. Currently, according to the works of the Osman et al. (2018), there are a number of software development life cycle models like an object-centric model, waterfall model, and incremental model. Tolosana et al. (2017) describes the SDLC models and it is found that each model has its own merits and demerits. The paper focuses on the software model designing to develop the Biometric Examiner Personal Verification System. There are mainly two phases of the biometric system that are Enrolment phase and the recognition phase. The enrolment phase is the first phase where the biometric information of the examiners is recorded and stored in the database. It's a one-time process where the information is measured very precisely. Then comes the 2nd phase which is the recognition phase. In this stage, the system detects the users based on the data stored in the first phase of the biometric system. This phase has to be quick and accurate since delay in identifying an individual can cause delay for others waiting in the queue.
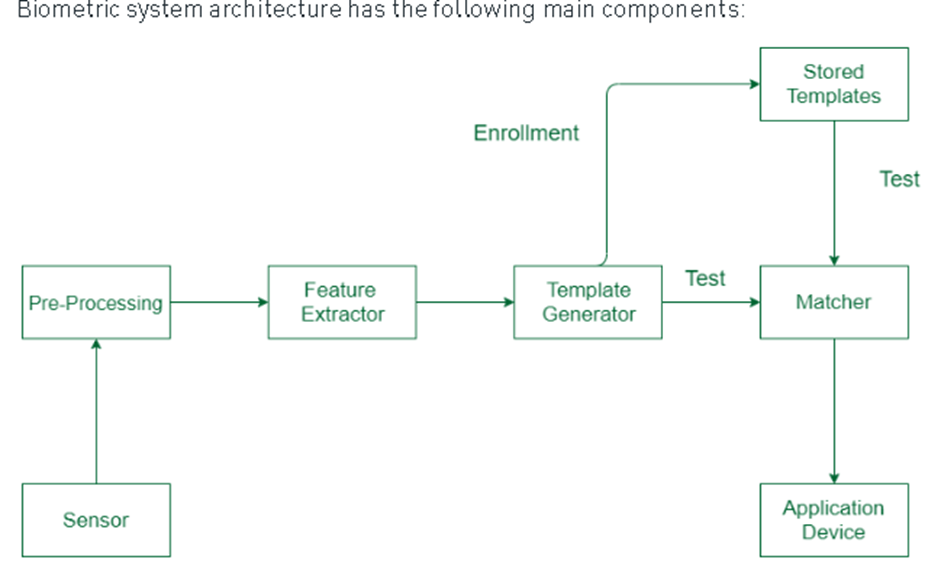
Figure1: Biometric system architecture
(Source: Merone et al., 2017)
Merone et al. (2017) describes the biometric system architecture is mainly developed based on the following blocks such as sensors, pre-processing, feature extractor, Template generator, Matcher, Application Device. The sensor is the first block of the system that collects all important information for processing. The sensor is mainly an image acquisition system but it largely relies on the characteristics needed that it needs to be replaced with. Pre-processing is the second stage which conducts everything related to pre-processing. The main function of the pre-processing stage is to enhance the inputs and thereby eliminate the artefacts from sensors, background noises etc. This pre-processing stage performs some type of normalisation. Feature extractor is the third stage and by far the most important stage in the entire biometric processing system. Extraction of characteristics is needed to be done so that they can be identified at a later stage. The key objective of the feature extractor is to feature an object which is to be recognised by the measurements. The template generator is the next stage that is used to generate the templates. These templates are further used for authentication.
F. Types Of Biometric System
Security, data integrity, fault tolerance, and system recovery are all characteristics of biometrics that may be tracked. Unique and unchangeable traits are recognised as a solid option for preserving identity and rights. Biometrics is utilised in two ways:
Identification: It is the process of determining a person's identification only via biometric measures (Sabhanayagam, Venkatesan and Senthamaraikannan, 2018). The comparator uses a 1: N matching algorithm to compare the acquired biometric with those stored in the database bank for identification.
Verification: It entails verifying or rejecting the alleged identification of a person. A fundamental identification (e.g., an ID number) is acknowledged, and a biometric template of the subject is matched using a biometric template of the subject taken.
To validate the person's identification, a 1:1 matching method is used.
The accuracy of a biometric system can only be determined by counting the number of errors that occur, such as the chance of accepting an intruder, known as the False Accept Rate (FAR), and the probability of rejecting a genuine individual, known as the False Reject Rate (FRR), which can be harmful to any system.
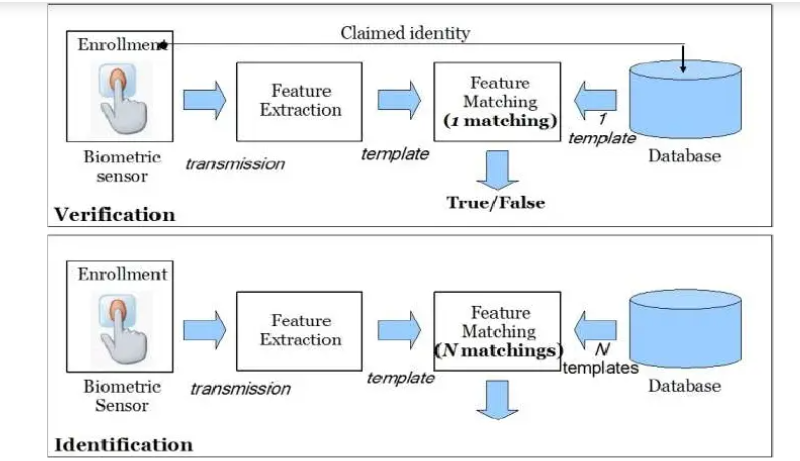
Figure2: Types of Biometric system
(Source: Sabhanayagam, Venkatesan and Senthamaraikannan, 2018)
Fingerprint Recognition
It requires photographing someone's fingers and noting characteristics such as whorls (ring-shaped ridges around a central point), arches (ridges that enter the finger from one side and climb to create an arc), and loops (the ridges enter from one side of a finger, form a curve, and then exiton that same side)
Fingerprint matching may also be accomplished in three ways by examining the patterns of ridges, furrows, and minutiae:
Minutiae-based matching preserves minutiae as a collection of points on a plane, which are subsequently matched against the template's minutiae (Obaidat, Traore and Woungang, 2019).
Correlation based matching is used to detect the correlation between corresponding pixels by superimposing two fingerprint images.
Due to the difficulty of collecting minutiae in low-quality fingerprint images, ridge feature-based matching is a more effective technique that captures ridges.
Nowadays, fingerprints are recorded using optical (CCD or CMOS image sensors) or capacitive sensors (thermal, electric field, and piezoelectric). These sensors send and receive acoustic pulses at the finger. Fingerprint scanning is a reliable method. It protects doors. Design Patterns Loop whorl door locks with computer network access are becoming more widespread. Recent ATM fingerprint readers are now available.
Face Recognition
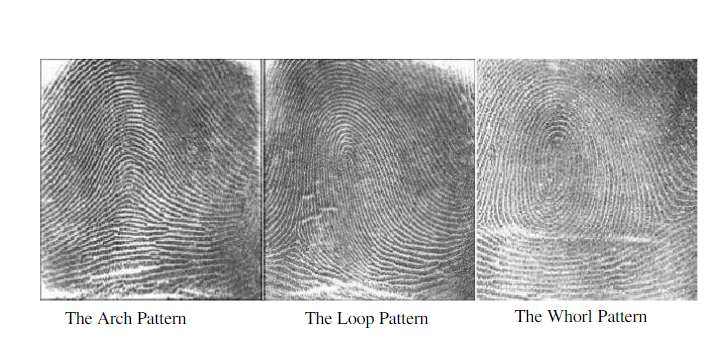
Figure3: picture of scanned fingerprint
(Source: Park et al., 2018)
The distance between the eyes, nose, mouth, and jaw are measured. These data are compared in a database.
Face recognition has two modes:
Uses of the face Face image Fourier processing into fundamental frequencies and Eigen face synthesis using covariance matrices of training photographs Face capture without oversensitivity to noise like lighting variations Eyes, mouth, nose, and chin are portrayed as faces with variable geometries (Park et al., 2018). This requires matching constellations.
Irradiance scans identify face characteristics. Non-intrusive, disguise-proof tech. Plastic surgery can't fix it. In this way, you save space while improving accuracy and speed. Many systems now need a human-like smile, blink, or other movement before verifying. In networks and automated bank tellers, this strategy is believed to prevent terrorism.
Voice Recognition
Authentication domain classification of voice recognition techniques. During registration, the speaker must utter a prepared word. To compute a word or phrase, the system asks the user to speak a word or phrase. No specific words or phrases are required in the text independent technique. As per the argument of Okokpujie et al. (2017), the system matches based on fundamental speech patterns in any language or text. Asking questions that only a real person would know or anticipate verifies the speaker's identity. The vocal-tract transfer function H is illustrated (z). The transfer function has poles and zeros. Only the voiced areas may be used in an all-pole model for H(z). To estimate the parameters of an all-pole model, linear prediction analysis may also be used. Its magnitude spectra are identical to the actual model's minimum-phase component. This method is inexpensive, reproducible, and sensitive to background noise (Chennattu et al., 2019). Affected by illness, hoarseness, or other common throat troubles, it is not always accurate.
Voice-activated computers, phone banking, mobile commerce, and audio and video
G. Importance of Biometric Systems
Individuality: The many biometrics systems have been created around the individual's unique traits. It's almost impossible for two persons to have the same biometric data.
It can't be shared: A biometric trait is exceedingly difficult to reproduce or distribute since it is an inherent property of a person (you can't give someone a copy of your face or hand!).
It can't be replicated: Biometric traits are almost hard to fabricate or spoof, particularly with emerging technology that ensure the biometric being detected is from a living individual [9].
Cannot be misplaced: Only a major accident may cause an individual's biometric property to be lost.
H. Database System Review
According to Dhanalakshmi, Kumar and Sai (2017), a database is a collection of data records, files, and other items. A database system is a phrase used to describe a data model, database. DBMS and database. A database management system (DBMS) is a collection of computer applications that manage databases. An information system's data is kept in files and databases. A database is a collection of interconnected files. The design is the process of creating physical database schemas. A database schema describes a database's structure in a formal language supported by the database management system (DBMS) (divided into database tables) [10]. A database system provides scalability, data sharing across user groups, standardisation, controlled redundancy, effective security, flexibility, and data reliance.
I. Database Language Review
It is possible to construct and manage a database on a computer using database languages. Oracle, MySQL, and MS Access are just a few of the many database languages available. DBase, FoxPro, etc. are examples of such programmes. DDL (data definition language) and DML (data manipulation language) are two types of SQL statements extensively used in Oracle and MS Access (DML). Database object creation, alteration, and destruction are all part of SQL's Data Definition Language (DDL). Data warehouse schemas and tables are only a few examples of the many types of database objects that exist. SQL's Data Manipulation Language (DML) lets you perform data manipulation and control operations on your data (Chandramohan et al., 2017). Structured Query Language (SQL) is a common data manipulation language used to obtain and modify data in a relational database.
II. ANALYSIS AND DESIGN
J. System analysis based on the requirements
Current system used
System with proper technological infrastructure is required for measuring and analysing the unique physical and behavioral characteristics of people. In educational institutes the biometric system is also used for taking attendance of students. The existing system still used in most of the educational institutes are traditional systems for taking attendance of students and it is quite time-consuming with wastage of a lot of time. In such a process, both the time of the lecturer and the student is wasted for managing the attendance system. The worst thing about the traditional attendance taking system is that the lecturer sometimes becomes frustrated due to damage to the attendance sheet by any kind of natural disasters such as flood or insect attack (Okokpujie et al., 2017). The entire thing also gets damaged if the attendance sheet is lost anyhow. Last but not the least, human errors can also make issues in the entire system of attendance taking of students in educational institutes.
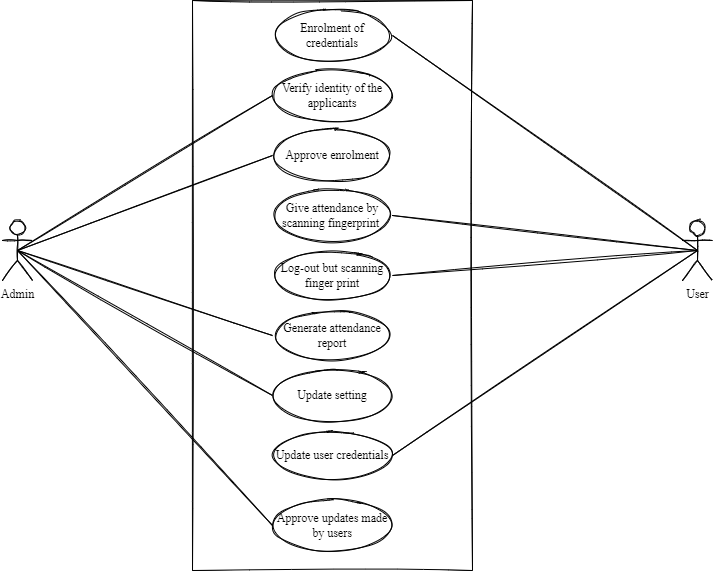
Figure 4: Use case diagram
(Source: Made by Author)
Proposed system
Biometric devices will be used for taking the attendance of the students in the proposed system by the educational institute. A proposed system fingerprint device has been suggested for better improvement of the attendance tracking system of the institution without wasting time of both the lecturer and the students. Wadhwa (2017) stated that the attendance taking using fingerprint devices is done mainly on the first day of the class or within one week. At first all the students are enrolled in the system and the fingerprints of the students are then scanned and recorded for future use. Besides the fingerprint the other information of the students is recorded so that the educational institute has almost all the important information about the students in their system. Whenever the student will be present in the lecture hall where the biometric system is being used, the student will be scanned for counting as present. No doubt the technological infrastructure will take a handsome expense but the overall cost effectiveness of the system will be helpful for the educational institute.
K. Requirement gathering and analysis
primary data will be collected for this research and the data will be collected from interviews. a questionnaire will be distributed among the respondents for getting their insights about biometric database system development life cycle especially in educational institutes (Adamu, 2019). For secondary data collection the existing literature on the chosen topic will be used.
Functional requirements
The following functional requirements are mainly used by the users -
1. Collection of data in the database with a proper backup.
2. Retrieval of data from the database will also be required in future.
3. It is also important to consider that attendance records are not used twice or duplication is done.
4. Registration of the students in the database according to their attendance (Olagunju, Adeniyi and Oladele, 2018).
5. Helping the students in updating their information whenever required.
The functional requirements mentioned above helps in describing what a software system should be able to do. The biometric system used for attendance in educational institutes will also need the functional requirements for better management of the records of the students.
Non-functional requirements
The non-functional requirements here will mainly be used for placing constraint on how the system will perform all the duties required -
Software Requirements for this are - Database Management System (DBMS)
Visual C#, Windows Operating systems (Windows XP, Windows 10, Vista and many more).
Hardware Required are - Fingerprint Scanner, 1 GB RAM, CPU with 2.2 GHz or more, 1024X864 Display are required for better maintenance of the biometric attendance. It will be better if the display used here is 1280X1080.
L. System Analysis of the database
Introduction to Design
During the software development phase, modelers create specifications and data models, as well as process models that are used to generate context diagrams, entity relationship diagrams, and data flow diagrams for a newly implemented system. Following the design phase, there needs to be a coding phase, testing and documenting the system. Testing will occur after the system's code has been written and executed by the tester (Park et al., 2018). After the coding and testing phase, it needs to be documented so that it can be understood by others.
3.2.2 Detail System
3.2.2.1 Data Flow Diagram
A data flow diagram is a graphic representation of the flow of data through an information system, which illustrates the process of data input and output. According to Osman et al. (2018), a data flow diagram shows where data is generated and where data is consumed, as well as where the data will be stored. Not only that Data flow diagrams will show how information travels through an information system, taking into account all aspects of its process. DFDs show what kinds of information will be input into the system and what type of output will be obtained from it, where the data will travel, and how it will be displayed. Flow diagrams convey information of how the data flows through a system, as opposed to technical documents, because they show timing and processes as well as a description of whether processes will run in sequence or in parallel. Data flow diagrams are the method of choice over technical description for conveying the information of how data moves through a system, based on these three principles
1. There is hardly any barrier to understanding DFDs for technical and non-technical audiences (Merone et al., 2017).
2. In addition to the boundaries and connections to other systems, DFDs also enable a high-level view of a system
3. Detailed representations of components can be obtained from DFDs
As part of the initial analysis phase, DFDs assist system designers and others by providing an overall picture of the current system or one that may be needed to meet future needs. System analysts prefer to work with DFDs especially when they need to understand the boundaries between the existing system and postulated system.
All entities outside the system, such as users, organisations or programs, which interact with it, but are not part of the system, are represented by this rectangular shape (Obaidat, Traore and Woungang, 2019).
There are a number of processes and procedures whose names and numbers indicate occurrence in the system flow. These processes and procedures are formed by taking data as input, processing it, then delivering a result.
There are two types of data flows: electrical and physical data. Arrows represent those flows.
The rectangles represent open-ended data stores, including electronic databases and XML files, as well as physical storage such as filing cabinets or stacks of paper.
Data flow diagram for attendance system of the students
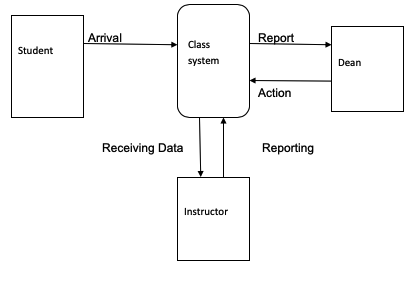
Figure 5: Data flow diagram for attendance system
(Source: Obaidat, Traore and Woungang, 2019)
3.2.2.2 Context Analysis Diagram
During software engineering and systems engineering, assistant contacts diagrams represent the external actors who may interact with the system. The diagram aims to represent the highest-level view of the system, similar to a block diagram, which represents the system as a whole with its inputs and output. By negotiating an agreement with the customers on the data flows, this context diagram limits the scope of the project to an agreed limit (Soniya et al., 2017). The context diagram emphasizes the relationship with external entities and identifies how information gets shared between the external entities and the system under review. Data exchange between the external entities and the business systems is within the scope of the project, but the external entities themselves are outside it.
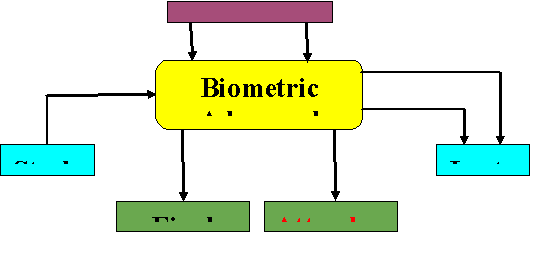
Figure 6: Context Analysis Diagram
(Source: Soniya et al., 2017)
3.2.3 Decision tree/ table
Decision trees define the relationship between each condition and its permissible actions. They don't take an object or situation as input and output as a yes or no. Decision trees also represent Boolean functions (Adamu, 2019). They allow relationships between one condition and its permissible actions to be laid out. This diagram represents a decision tree.
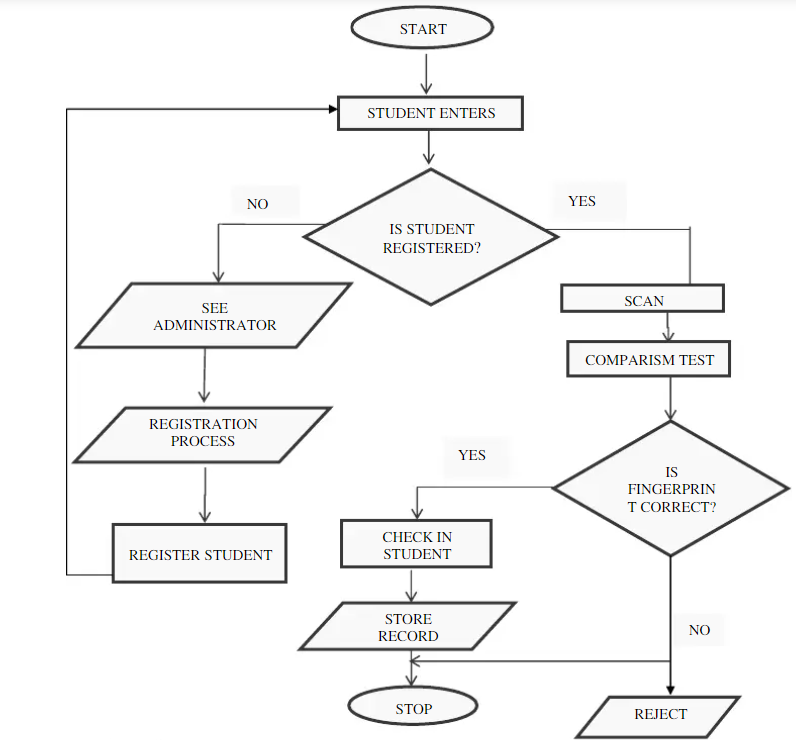
Figure 7: Decision tree for database system
(Source: Adamu, 2019)
3.2.4 Entity Relationship Diagram
To construct the ER diagram, a number of motivational conventions had to be utilized. The diagram was produced with the help of a smart drawing package, which offered easy-to-use functions that were helpful in facilitating consistency (Obaidat, Traore and Woungang, 2019). A rectangle represents a class, a diamond represents a relationship, and an oval represents every attribute of an entity.
In addition, entity relationship diagrams can be defined as diagrams that show the relationship between entities in the database. These diagrams are designed to provide a detailed, logical and graphical representation of information for a particular organisation or business area. Data flow diagrams are commonly used in the development of information systems so that a streamlined understanding of how data is organised can be achieved.
III. RECOMMENDATION
Based on the above discussion, some suggestions are given for better management of biometric database system development life cycle -
Performing research and analysis for determining the needs of the end users is required
A detailed research and analysis on the needs of the end users is also highly recommended before establishing the system. If the system is made according to the requirements of the users, the analysis stage of the biometric database system development cycle will be highly beneficial. All the required elements for the new system can be then easily gathered. Last but not the least, the usability of the system will also increase as a consequence.
Longer maintenance stages must be used for larger systems
In the maintenance stage of the development lifecycle the developers must be sure about the maintenance mode and the activities required for coping up with the issues that are reported by the end users. Any kind of changes required for the software can also be done in this stage and hence it is important to take care of the requirements for the maintenance stage. If larger systems are used in this project, it is also required to implement longer maintenance stages for better performance for a long-term period.
Programming Code based on the project requirements and specification must be used
Programming languages required for the implementation stage of the development life cycle of the biometric database can include various staples such as PHP, C++, Java and many more. Developers are required to follow any coding guideline for better management of the biometric system and it is important to choose the best required programming language for the entire project. It should also be made sure that coding is done properly to avoid any kind of technical issue in the coming future.
IV. CONCLUSION
In this era of technology, several systems have been introduced and implemented by many to save the most precious thing in the world that is time. Attendance taking system of any educational institution consumes a lot of time from both the lecturer and the students. Moreover, in this manual system errors are inevitable. Not only does it include errors but this system also includes lots of problematic situations while maintaining an everyday record of student attendance. With the space of time it becomes highly essential to implement something unique that will consume the least amount of time in comparison to the traditional method. In addition to this, an error free system and quick access will be an added advantage of this system. Biometric attendance systems will reduce the load of maintaining the huge records of each class along with the hassles of keeping it safe from external damage.
In this article the proper process of implementing the biometric attendance system has been described in full detail. Even every nook and corner of this system has also been highlighted to focus on those grounds which require utmost attention to make this system most beneficial to implement. Based on the findings above, it can be concluded that manual systems are bound to suffer from problems and errors due to common mistakes of humans when the amount of data increases as well as issues with impersonation. The only thing is that, this system will require proper software and hardware application to input the data of the students like photo Id, fingerprints etc that are needed to be updated within a certain interval of time therefore it requires highly technological advancement to maintain, which may be costly to some extent but it can definitely save a lot of time to be used in the other important ground. In a simple word, this system can lead to the attendance taking system process to the next level.
REFERENCES
BELLO, R.O., OLUGBEBI, M., BABATUNDE, A.O., BELLO, B.O. and BELLO, S.I., (2017). E-attendance system using waterfall software development life cycle simulation. https://uilspace.unilorin.edu.ng/bitstream/handle/20.500.12484/1292/11.%20E-ATTENDANCE.pdfsequence=1&isAllowed=y
Unal, C. and Tecim, V., (2018). The use of biometric technology for effective personnel management system in organization. KnE Social Sciences, pp.221-232. https://www.knepublishing.com/index.php/Kne-Social/article/view/3540/7425
Osman, M.N., Sedek, K.A., Maghribi, M. and Faisal, N.H.M., (2018). ANotify: A Fingerprint Biometric-Based and Attendance Web-Based Management System with SMS Notification for Industrial Sector. Journal of Computing Research and Innovation, 3(1), pp.36-45. https://crinn.conferencehunter.com/index.php/jcrinn/article/download/97/59
Tolosana, R., Vera-Rodriguez, R., Fierrez, J., Morales, A. and Ortega-Garcia, J., (2017). Benchmarking desktop and mobile handwriting across COTS devices: The e-BioSign biometric database. PloS one, 12(5), p.e0176792. https://journals.plos.org/plosone/articleid=10.1371/journal.pone.0176792
Merone, M., Soda, P., Sansone, M. and Sansone, C., (2017). ECG databases for biometric systems: A systematic review. Expert Systems with Applications, 67, pp.189-202. https://www.academia.edu/download/51508091/ECG_databases_for_biometric_systems__A_systematic_review.pdf
Sabhanayagam, T., Venkatesan, V.P. and Senthamaraikannan, K., (2018). A comprehensive survey on various biometric systems. International Journal of Applied Engineering Research, 13(5), pp.2276-2297. http://www.ripublication.com/ijaer18/ijaerv13n5_28.pdf
Obaidat, M.S., Traore, I. and Woungang, I. eds., (2019). Biometric-based physical and cybersecurity systems (pp. 1-10). Cham: Springer International Publishing. https://link.springer.com/content/pdf/10.1007/978-3-319-98734-7.pdf
Park, Y.R., Yoon, Y.J., Koo, H., Yoo, S., Choi, C.M., Beck, S.H. and Kim, T.W., (2018). Utilization of a clinical trial management system for the whole clinical trial process as an integrated database: system development. Journal of medical Internet research, 20(4), p.e9312. https://www.jmir.org/2018/4/e103/
Okokpujie, K.O., Noma-Osaghae, E., Okesola, O.J., John, S.N. and Robert, O., (2017, December). Design and implementation of a student attendance system using iris biometric recognition. In 2017 International Conference on Computational Science and Computational Intelligence (CSCI) (pp. 563-567). IEEE. http://eprints.covenantuniversity.edu.ng/10681/1/IEEE_An%20improved%20Bank%20Credit%20Scoring
%20Model%20%20A%20Na%C3%AFve%20Bayesian%20Approach.pdf
Chennattu, S., Kelkar, A., Anthony, A. and Nagdeote, S., (2019, November). Portable biometric attendance system using IoT. In 2019 4th International Conference on Information Systems and Computer Networks (ISCON) (pp. 245-249). IEEE. https://ieeexplore.ieee.org/abstract/document/9036275/
Dhanalakshmi, N., Kumar, S.G. and Sai, Y.P., (2017, January). Aadhaar based biometric attendance system using wireless fingerprint terminals. In 2017 IEEE 7th International Advance Computing Conference (IACC) (pp. 651-655). IEEE. https://ieeexplore.ieee.org/abstract/document/7976871/
Chandramohan, J., Nagarajan, R., Dineshkumar, T., Kannan, G. and Prakash, R., (2017). Attendance monitoring system of students based on biometric and gps tracking system. International Journal of Advanced engineering, Management and Science, 3(3), p.239799. https://www.researchgate.net/profile/Nagarajan-Ramalingam/publication/315659150_Attendance_Monitoring_System_of_Students_Based_on_
Biometric_and_GPS_Tracking_System/links/58db547245851578dff0b505/Attendance-Monitoring-System-of-Students-Based-on-Biometric-and-GPS-Tracking-System.pdf
Okokpujie, K., Noma-Osaghae, E., John, S., Grace, K.A. and Okokpujie, I., (2017, November). A face recognition attendance system with GSM notification. Information system assignment In 2017 IEEE 3rd international conference on electro-technology for national development (NIGERCON) (pp. 239-244). IEEE. http://eprints.covenantuniversity.edu.ng/9871/1/A%20Face%20Recognition%20Attendance%20System
%20with%20GSM%20Notification.pdf
Wadhwa, P., (2017). Attendance system using android integrated biometric fingerprint recognition. International Research Journal of Engineering and Technology (IRJET), 4(6), pp.1069-1073. https://www.academia.edu/download/53811811/IRJET-V4I6197.pdf
Adamu, A., (2019). Attendance management system using fingerprint and iris biometric. FUDMA J Sci (FJS), 3, pp.427-433. https://www.researchgate.net/profile/Abubakar-Adamu-12/publication/338536515_ATTENDANCE_MANAGEMENT_ATTENDANCE_MANAGEMENT_
SYSTEM_USING_FINGERPRINT_AND_IRIS_BIOMETRIC/links/5e1a3803a6fdcc28376ba20e/ATTENDANCE-MANAGEMENT-ATTENDANCE-MANAGEMENT-SYSTEM-USING-FINGERPRINT-AND-IRIS-BIOMETRIC.pdf
Olagunju, M., Adeniyi, A.E. and Oladele, T.O., (2018). Staff attendance monitoring system using fingerprint biometrics. International Journal of Computer Applications, 179(21), pp.8-15. http://eprints.lmu.edu.ng/1125/1/IJCA%20Accepted%20Paper.pdf
Soniya, V., Sri, R.S., Titty, K.S., Ramakrishnan, R. and Sivakumar, S., (2017, March). Attendance automation using face recognition biometric authentication. In 2017 International Conference on Power and Embedded Drive Control (ICPEDC) (pp. 122-127). IEEE. https://ieeexplore.ieee.org/abstract/document/8081072/












