Information Security Assignment: Threat Modelling Process Of Peters Excellent Packers
Question
Task:
Initial Case Scenario
Peters Excellent Packers (PEP) is a meat packing and delivery service located in Western Sydney. They are a small to medium enterprise, and last year their turnover was about $15 million. They employ a small number of staff and use their own software system, developed in-house in the late 90s. This system is used for all accounting and inventory purposes, as well as the bulk of their tax reporting, although they still employ one accountant, the CFO, KishwarChowdhary.
The business has a website which takes orders for their services and issues invoices. It is linked to their main transactional database. They are also contracted to pack and supply meat goods to large shopping centres. The firm has a small network on their premises. Currently, all IT related duties are performed by staff member, Elise Pulbrook.
The management of PEP has recently become aware of the attack on JBS Foods in early 2021. The company is concerned that attacks like the one on JBS Foods are on the rise. As part of your report, PEP want you to give a brief explanation and timeline on the attack on JBS Foods. (Note: PEP is fictional, but JBS Foods and the attack on JBS Foods is a real-world case, which also affected businesses in Australia. You must discuss the real-world attack, with references, including the Australian impact. You cannot “discover” fictional data about JBS Foods, although you are encouraged to do so for PEP.
PEP has called on you and your small team of cybersecurity consultants, to improve the security of their organisation. They want to protect against the same type of attack that hit JBS Foods, but they may also want mitigation against any threats or vulnerabilities you might find after investigating their organisation. This “investigation” is a part of A2.
In preliminary discussion with the CEO, Peter Campbell, it seems there is no system-wide intrusion detection and prevention and no network segmentation, although the CEO seemed quite vague on the topic.
In the first instance (for your assessment 2), PEP wants a report on threats and vulnerabilities in their organisation. (You should “discover” at least 10 threats and/or vulnerabilities and map these against the STRIDE categories.)
After this, they might commission you to design a project of mitigation with some recommendations of ongoing security management (this will be your assessment 3). In the mitigation scheme, as much as possible, they want you to match controls against threats and justify your controls in the case of the threat(s) related to the specific attack on JBS Foods.
You have negotiated with PEP to use STRIDE to perform an IT security risk analysis, to advise them on their overall cybersecurity but also report on their in-house system.
Peter Campbell has sent you an email with some helpful links to the JBS Foods attack that have raised the concern of PEP.
JBS Foods attack:
White House Warns Business Leaders To Increase Cybersecurity
Cyber attack shuts down global meat processing giant JBS
Task Summary
The goal of information security assignment is to identify threats/vulnerabilities in the case scenario. Not all threats/vulnerabilities you “discover” are in the initial case scenario. The scenario discusses some elements of the business that are needing mitigation, but you will need to also “discover” other threats/vulnerabilities.
DFD Requirements
The DFD must relate to the business described in the initial case scenario. Remember, the DFD is the first step in the risk analysis, but it is not the main output of the assessment. The main output is the categorised threats, see below.
For the DFD, you need at least a context diagram and a level-0 diagram. You can include further levels if you feel they are needed to show a threat boundary, but this is not necessary. The level-0 diagram (and further level diagrams, if needed) must not break the rules for proper DFD formation. And the DFDs (excluding the context diagram) must have labelled threat boundaries.
Threat Discovery The main output of A2 should be a set of no less than 10 threats or vulnerabilities that need mitigation in the organisation. You will discover these with the help of the DFD and the threat boundaries.
Answer
Introduction
Peters Excellent Packers (PEP) is an SME industry operating successfully with a good turnover. The system of the organisation functions with different operations from inventory management to accounting. The firm aims to strengthen its IT infrastructure in order to minimise the risk of cyber-attacks. Thus, PEP has hired a cybersecurity consultant team in order to identify significant threats that are possibly existing in their business system. This will lead them to plan the next step for recommending different solutions in order to resolve those risks and threats from the firm (Cyber security threats rising, 2021). The primary aim of the company is to protect their business operations from the similar type of attacks that JBS Foods has faced recently. This report outlines an investigation of the threats in this regard.
DFD
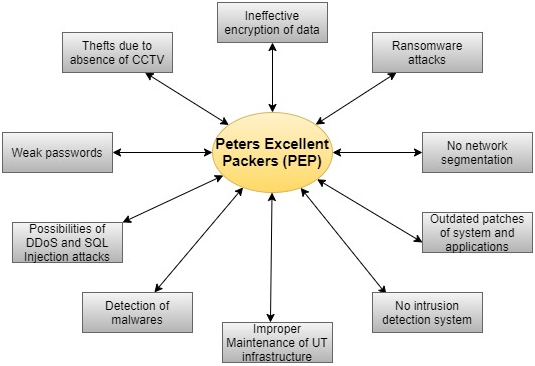
Figure 1: Context Level Diagram
(Source: Created by Author)
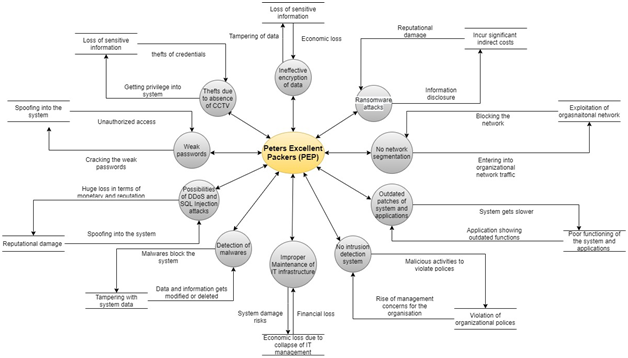
Figure 2: Level 0 DFD
(Source: Created by Author)
Threat Discovery
There are certain threats that are exhausting in the business of Peters Excellent Packers (PEP), which can pose potential threats to the organisation in the near future. As a result of that, the organisation needs to plan threat mitigation strategies after the discovery of threats. In this section, ten of the significant threats that have been identified for PEP in their business process should be mitigated immediately.
|
Identified Threats |
Description of the threats |
Impact |
|
Weak password in system devices |
The presence of simple and predictable passwords can be vulnerable to the overall system. The malicious cyber attackers can try to exploit them in their favour (Kopp, Kaffenberger& Wilson,2017). |
HIGH |
|
Technical thefts due to ineffective CCTV systems |
The incompetent CCTV and monitoring systems can be quite critical in terms of preventing physical thefts within the organisation (Kovacich, 2016). It will be essential that the organisation ensures the operational proficiency of this equipment at all times. |
MODERATE |
|
Absence of proper encryption of data |
The lack of proper data encryption can cost in issues like data breaches and security issues (Calder, 2020). In this process, the presence of the 256-bit AES encryption system will be quite essential. |
MODERATE TO HIGH |
|
Possibilities of Ransomware attacks |
The possibility of ransomware attacks upon the T infrastructure of the organisation is also quite high. In this process, the organisation may lose a lot of monetary resources and reputation in the market. |
HIGH |
|
Lack of network segmentation |
The presence of robust network integrity is essential to maintain the security of the overall IT infrastructure (Petrenko, 2018).. The lack of network integrity can result in the success of the cyber attackers in terms of breaching the security modules of the organisation's IT systems. |
HIGH |
|
Outdated patches of applications and operating system |
Cyber attackers are improving continuously with their enhanced level of digital attacks (Calder, 2020). For executing proper security applications, it is quite essential for the organisation to update the software and patches that are installed within the system (Colarik,Jang-Jaccard&Mathrani,2017). In the case of using outdated patches and system updates, essential elements like virus definition may not be competent enough to mitigate the newest threats of the cyber world. |
MODERATE TO HIGH |
|
Absence of intrusion detection system |
The absence of any intrusion detection system can result in an incompetent security module in the organisation's IT framework. |
HIGH |
|
Lack of maintenance of the IT infrastructure |
Without maintaining the IT infrastructure, the work efficiency of the system would not be proficient. |
MODERATE |
|
Detection of malware in the system since the systems are not upgraded regularly |
The malware detection system of the IT infrastructure will not be updated without a regular software upgrade (Wright, 2019). |
MODERATE |
|
Possibilities of DDoS or SQL injection attacks to target the firm’s sensitive information |
The possibility of DDoS and SQL injection attacks is always a high threat for any IT-based organisational system. |
MODERATE TO HIGH |
|
Identified Threats |
Probability Score (1-5) |
Impact Score (1-5) |
Severity= Probability * Impact |
|
Weak password in system devices |
4 |
4 |
16 |
|
Technical thefts due to ineffective CCTV systems |
3 |
2 |
6 |
|
Absence of proper encryption of data |
4 |
3 |
12 |
|
Possibilities of Ransomware attacks |
5 |
5 |
25 |
|
Lack of network segmentation |
5 |
4 |
20 |
|
Outdated patches of applications and operating system |
5 |
3 |
15 |
|
Absence of intrusion detection system |
3 |
4 |
12 |
|
Lack of maintenance of the IT infrastructure |
4 |
2 |
8 |
|
Detection of malware in the system since the systems are not upgraded regularly |
3 |
3 |
9 |
|
Possibilities of DDoS or SQL injection attacks to target the firm’s sensitive information |
2 |
3 |
6 |
|
THREATS |
Possible actions on the organisation |
Security properties |
|
Spoofing |
This can pose threats to the organisation due to unauthorised access to the system, which can lead to the loss of sensitive information (Petrenko, 2018). |
Authentication |
|
Tampering |
Data tampering can give the privilege to the cyber attackers to enter into the system and modify or delta information as per their wish (Dalziel, 2016). |
Integrity |
|
Repudiation |
Cyber attackers can possibly remove all such evidence from the system after the cyber-attack. |
Non-repudiation |
|
Information Disclosure |
Sensitive information can get disclosed due to the malicious activities of the cyber attackers, and this can pose potential loss to the company (Kovacich, 2016). |
Confidentiality |
|
Denial of Service |
If the cyber attackers have blocked the system, the users will lose the privilege of accessing data and information stored in the system (Dalziel, 2016). |
Availability |
|
Elevation of Privilege |
Cyber attackers can gain additional privileges to enter into the company's IT infrastructure without the knowledge of the users of the organisation. |
Authorisation |
|
Threat List |
STRIDE Categories |
Justification |
|
Weak password in system devices |
Spoofing |
Unauthorised access to the system |
|
Technical thefts due to ineffective CCTV systems |
Tampering |
Modification of data to steal important information |
|
Absence of proper encryption of data |
Information Disclosure |
Loss of sensitive information from network or devices |
|
Possibilities of Ransomware attacks |
Denial of Service |
Blocking the use of original users |
|
Lack of network segmentation |
Elevation of Privilege |
Entering into the network traffic of the organisation |
|
Outdated patches of applications and operating system |
Repudiation |
Removing the evidence of new updates leading to data loss |
|
Absence of intrusion detection system |
Tampering |
Violation through malicious activities by entering into the system (Hubbard&Seiersen, 2016). |
|
Lack of maintenance of the IT infrastructure |
Repudiation |
Gaining the privilege to use the system infrastructure without permission (Hubbard&Seiersen, 2016). |
|
Detection of malware in the system since the systems are not upgraded regularly |
Denial of Service |
Blocking the users from system applications and files |
|
Possibilities of DDoS or SQL injection attacks to target the firm’s sensitive information |
Tampering |
Disrupting the integrity and confidentiality of the organisational information (Kopp, Kaffenberger& Wilson,2017). |
Conclusion
There are significant threats existing in the business operations of Peters Excellent Packers (PEP). The overall analysis of ten threats can pose moderate to high impacts on the organisation. Thus, it is quite essential in this process to plan mitigation strategies against each of the threats defined for Peters Excellent Packers (PEP). Weak passwords of the system devices and theft through CCTV are some of the major concerns that have been posing potential threats for the organisation. As a result of that, the identification of these potential threats must lead to a systematic and proper planning system that can be beneficial for the organisation to resolve these threats. The firm needs to take certain steps against ransomware attacks and phishing emails which can cause potential harm to the organisation. Thus, Peters Excellent Packers (PEP) needs to prioritise cyber security concerns in order to eliminate the threats and ensure strong encryption for protecting the integrity and confidentiality of the technological system of the business.
Recommendations
Certain recommendations will be quite beneficial for the business of Peters Excellent Packers (PEP) to plan mitigation strategies against each of the threats existing in their business. In order to avoid potential cyber-attacks, the business can proceed with the following suggestions that will be beneficial for the organisation to organise mitigation plans for the future.
Integration of a real-time monitoring system that can track any kind of cyber security issues existing in the operations.
Planning of various worst-case scenarios that can handle the emergency incidents which can arise in the organisation and needs an urgent and effective response in the process.
There should be an efficient authentication process in the system devices of the organisation in order to eliminate the risks of thefts through weak passwords.
There should be robustness in the cyber security of the organisation in order to hinder any kind of users’ mistakes and plan appropriate mitigation in this case.
The outdated patches existing in the devices should be eliminated from the organisational IT infrastructure.
The network traffic should be monitored regularly in order to identify any kind of superpowers elements.
Good encryption schemes should be applied in order to protect sensitive information for the organisation.
Other than that, the code reviewing should be maintained consistently, and there should be frequent upgradation after any application development.
References
Calder, A. (2020). Cyber security: essential principles to secure your organisation. ITGP. Retrieved October 28, 2021 https://lesa.on.worldcat.org/v2/oclc/1153985158
Colarik, A. M., Jang-Jaccard, J., &Mathrani, A. (Eds.). (2017). Cyber security and policy : a substantive dialogue (Ser. Massey defence and security series). Massey University Press. Retrieved October 28, 2021 https://lesa.on.worldcat.org/v2/oclc/974591142
Cyber security threats rising. (2021). The Australian Financial Review, 2, 2–2. https://lesa.on.worldcat.org/v2/oclc/8974644253
Dalziel, H. (2016). How to define and build an effective cyber threat intelligence capability. Syngress, an imprint of Elsevier. https://lesa.on.worldcat.org/oclc/898422494
Hubbard, D. W., &Seiersen, R. (2016). How to measure anything in cybersecurity risk. Wiley. https://lesa.on.worldcat.org/oclc/953458699
Kopp, E., Kaffenberger, L., & Wilson, C. (2017). Cyber risk, market failures, and financial stability (Ser. Imf working paper, wp/17/185). Information security assignment International Monetary Fund. https://lesa.on.worldcat.org/v2/oclc/1001379511
Kovacich, G. L. (2016). The information systems security officer's guide : establishing and managing a cybersecurity program (Third). Butterworth-Heinemann. https://lesa.on.worldcat.org/oclc/935112540
Petrenko, S. (2018). Cyber security innovation for the digital economy : a case study of the russian federation (Ser. River publishers series in security and digital forensics). River. Retrieved October 28, 2021 https://lesa.on.worldcat.org/v2/oclc/1078998071
Wright, C. (2019). How cybersecurity can protect your business : a guide for all stakeholders. IT Governance. https://lesa.on.worldcat.org/oclc/1128417557












