Information Security Assignment: Identifying Security Handling Model of Astra Zeneca
Question
Task: Information Security Assignment Instructions: You are a newly appointed Chief Information Security Officer (CISO) in an organisation. In the light of the recent high profile of poorly-handled information security incidents, you have been asked to write a 3000-word report to senior management in your organisation (which could be a company or organisation in the public or third sector) which (a) research, proposes and evaluates a model for security incident handling, and (b) applies it to the organisation you have chosen.
You should develop an incident handling model from academic or credible professional sources. Illustrate and analyse the model using examples from current news stories (ideally from 2017 onwards). Assess its strengths and weaknesses, and the implications in the light of the increasing need to respect the privacy of the individuals whose data are stored in the systems.
Information Security events are now regularly in the news and well reported and you should have no problems finding examples to illustrate your report.
Answer
Introduction
Today's current industry is facing considerable difficulties in their work process because of software inaccuracies effectively. As the technology industry is changing rapidly and similarly, the conceptual traditional work process is also improving. Software malfunctions and technology threats are continuously effectively limiting the current operational and functional business process in the public sector. With all these impacts of technologies, the economy also gets highly affected, and the work process gets highly hampered. Common threats that most businesses are facing right now are the threats that come from both internal and external mannerisms effectively and compromise the organisation's accuracy. Here this report mainly aims to provide a proposal and evaluates a model for security incident handling significantly that will be the best fit for the chosen organisation Astra Zeneca for their better success planning effectively. By using an effective security model, the organisation safely operates the entire working process and provides good services to those people who are in desperate need of those services significantly. The primary purpose of this report is to identify the most suitable security handling model that will resolve all the security issues of Astra Zeneca that they are facing currently.
The reason behind the increased importance of incident response management in the Health sector For achieving the long-term success goals of the organisation, Astra Zeneca is highly essential to maintain the trust of employees and customers and maintain the brand image in the market industry. When all these factors are at stake due to external and internal risks influences over the company, the organisation must include an incident response management system to enhance the security process inside the company effectively (Shaked& Reich, 2021). no matter how effective the issue or breach was, it is vital to adopt an incident response plan to mitigate the risk likelihood and cyber-attacks for better organisational structure and culture enhancement. Being a large health organisation, many datasets are getting generated in a considerable margin. Safekeeping all the customer's information is essential for earning the trust and loyalty of every organisation's customer to avoid customer churns. With the help of an incident response plan, the entire business management team can significantly protect all the information datasets of the customers with utmost care. This will prevent the probability of any uncertain situation for the organisation, such as data exploitation, identity theft, system hacking, fishing, ransoms, and many other cybercrimes. Protecting company data sources and assets is not an easy job to perform due to the large size of datasets in the company. In this case, utilisation of an Incident response management plan is beneficial and impactful (Brethauer& SE, 2018). All these activities include backups plans for data security, Security alert system application, identity management for threats prevention and confidential information leaks. In this way, brand reputation and customers trust, along with business revenue, can be easily increased. As a result of all these characteristics, the importance of the incident response management plan is kept in advance in a huge margin. The organisation Astra Zeneca significantly tries to maintain compliance with local and national regulations and safety protocols to control the brand reputation effectively. That is why an incident response management plan is required for better business activities and security enhancement.
Identification, Selection and adaption of Security incident Handling Model – Threat Model for Astra Zeneca
As per Jøsang, Stray&Rygge (2020), threat modelling is considered the security incident modellingapproach, mainly used to identify, understand and communicate all possible threats and risk possibilities of the business organisation to mitigate by protecting organisation assets and customers trust and loyalty towards the company effectively. A threat mainly represents the different datasets and information s that may impact the company and significantly comprises the organisation's security. Threat modelling can be utilised in various organisation sectors such as Internet of things devices, networks, system applications and software. The working principles of threat models include a model description that will be utilised in the business process of Astra Zeneca effectively, processing assumptions that are going to be checked in future for better threat models changes for the betterment of the business process security process. The threat model mainly consists of core capabilities to identify the possible threats of the company, not in the current scenario. Still, it also determines threats in future that has a high chance of occurrence over the company. Along with that, this model effectively poses features that will effectively mitigate all hazards. This model includes the verification of all the courses of action taken for the betterment of the company.
Identification and selection of Critical elements of Threat Model
Determining all the possible threats, attacks, internal and external impacts over the business process, evaluation of all potential threats, and identifying which threats require immediate attention to resolve them as early as possible to reduce the company's losses. Threats models in the health sector consider being the application to defend any risk inside the organisation's business activities without compromising the organisational culture and employee satisfaction of the company (Skobalj, 2019). The main key element of threat modelling is to determine breaking analogy, prioritise which threats are needed to take care of first, map the countermeasures, solution implementation. Testing and innovate new methodology for better security enhancement. The primary technology approaches of threat modelling are attack trees, hTMM, Security Cards, CVSS, STRIDE and PASTA. All these different application types of Threats have numerous benefits that can be easily used in the health sector organisation such as Astra Zeneca. An effective encrypted algorithm should be used in threat modelling for better accuracy of the system application that can be utilised for better threat mitigation purposes effectively and efficiently.
Incident handling Threat Model Approachesmethodologies
As per Reski (2019), attacks can severely hamper the entire operational process of health sectors. In the case of Astra Zeneca, it was leaking highly confidential information of the business, such as vaccine-related information that can hamper the brand rapport and destroy health workers trust who is working in the organisation Astra Zeneca effectively. Business management can significantly reduce all the risk factors in the health sector to defend against threats by taking different advantages from the system application loopholes and flaws. Different threat modelling approaches have numerous beneficial characteristics for preventing threats. Some of the most widespread threats models than often considered as incident handling models for the company Astra Zeneca are described below,
Stride Threat Model
This modelling technique is considered the most mature model of threat prevention inside the business processes effectively. This model evolved has configured many specifications with the advancement of technologies in the current industry to identify all types of security-related incidents better. Over time this modelling approach has included three new tables and two new variables that is STRIDE per Element, and the other one is STRIDE per interaction. In the case of the STRIDE incident security threat modelling approach, this particular model firstly evaluates the entire design of the system application for understanding the working operational stages of that system effectively for determining threats that much earlier than any other model approach for the organisation (Abbas et al., 2021). In-place modelling is processed by STRIDE. By using the DFD's, that is, data flow diagrams, STRIDE utilises to significantly determine the events, system entities, and system boundaries. For example, big organisations like Microsoft use the access stride model for threat prevention in their business process to mitigate uncertain security incidents. Mainly STRIDE threat model tool applies mnemonic, which means known general threats inside the organisation.
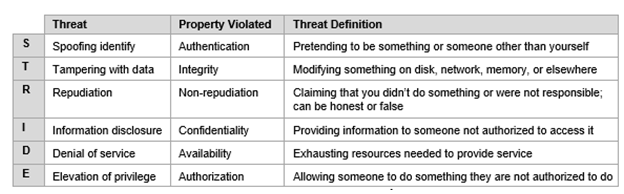
Figure 1: Categories of STRIDE Threats
(Source: Abbas et al. 2021)
Spoofing Tampering Repudiation Information Message Disclosure Denial of service and elevation of privilege is an effective threat prevention methodology for effectively enhancing quality services (Hossain,Salahuddin& Akbar, 2018). The primary purpose of stride threat modelling is to enable security properties of security and confidentiality such as integrity, availability and confidentiality of business processes vital information’s. This also focuses on authentication, non-repudiation and authorisation properties significantly. This modelling approach is very much well-structured and offered a large amount of security problem solutions effectively. However, this particular threat modelling is mainly focused on the system developers effectively. Stride threats operational process primarily focuses on six significant threats that can occur inside the organisation work process and limit the company's successful growth.
Advantages of using STRIDE Model
• Repudiation: This creates severe difficulties in the business process by making the process difficult to link up and work actions to the processor or system users extensively. This type of threat compromises the entire functionality of the system. The stride Threat model can resolve these threat possibilities from the business. Therefore, it will be most suitable for Astra Zeneca to opt for a better security process.
For example, USA election voting Repudiation.
• Information leaks: maintaining workers personal information, as well as customers' confidential information, is not only an essential thing to look at, but business-related documents and information's confidentiality is also needed to be maintained, such as research-related data, vaccine formulas of Astra Zeneca (Vallant et al., 2021). The stride model can effectively prevent this type of activity by providing a better security encryption process inside the system application—for example, Domino's Pizza information leaks of more than 150 million users.
• Data tampering: That is the most significant threat that can hamper the working accuracy of the entire business organisation and can further create huge problems to the organisations and enhance customer's churns, and business suffers loss. As per Yuva Kumar (2019), wrong datasets or comprised datasets can change the entire dynamics of the final result. In the health sector, any wrong information can cause an actual uncertain situation in the whole country. That is why this type of threat needed to be resolved as early as possible for preventing any health-related issues and mistreatments of any patients inside Astra Zeneca effectively. The Strider threat model has proven better accuracy in reducing the intensity of this type of data tampering like threat in the business process. For example, data tampering scandal in a Japanese subsidiary.
• Spoofing: Identify theft is currently one of the biggest threats the whole world business industry and everyday general citizens face. By making an entry on the private information about one person, identity theft is achieving enormously, and as a result of this theft, actual designated people are suffering enormous difficulties. In the false health identity, impersonating someone and making access to vital business information can become a massive threat for the company and the patients in the company effectively (Awojana ,2018). This stride modelling approach can reduce this type of threat once and for all by creating an effective security encryption process inside the business database management system significantly and, for example, spoofing scandal in the UK in the Indian embassy.
• Privilege elevation: Conducting unauthorised access to obtain some illegal activities is an effective threat inside the health care for availing healthcare services without having permission—for example, Microsoft scandal for elevation in privilege. Stride incident handling threat can significantly overcome these authorisation threats from the organisation and maintain a good structure organisation culture for employees to produce better work and serve customers with better services as promised. This will significantly level-ups Astra Zeneca's brand reputation in the health sector of the UK significantly.
TRIKE Threat Modeling
As per Ponsard et al. (2021), TRIKE threat modelling is considered a conceptual framework modelling approach that accompanies different open source technologies and tools for producing effective treat modelling to use under any system application for better quality and accuracy or work significantly. This threat modelling can process better risk assessment for the betterment of the company. This modelling approach provides a defensive process for combating numerous threats that occurs inside the organisation. By using this threat modelling approach, every system component can be resolved by CRUD that means. TRIKE threat modelling can create, update, read, and delete all the entities with the help of a data flow diagram. Each threat is taken under consideration of mainly two specific categories such as authorisation elevation and service denial. These two threats can be easily reduced by the TRIKE modelling approach very effectively. In the business organisation Astra Zeneca,unethical privilege activities can be overcome very easily without hampering the business operational work process.
Comparison Table
|
Features |
STRIDE Model Accuracy |
TRIKE Model Accuracy |
|
Repudiation |
This model able to control repudiation. |
Not able to control |
|
Privilege elevation |
Can control Privilege elevation |
Can control Privilege elevation |
|
Spoofing |
Model can reduce spoofing |
Model cannot reduce spoofing |
|
Data tampering |
Model can reduce Data tampering |
Model cannot reduce Data tampering |
|
Information leaks |
Highly accurate to reduce this threat |
Not enough accurate to reduce this types of threats |
Justification for choosing STRIDE Threat model
As discussed earlier, the stride threat modelling can significantly remove most of the risk possibilities and threats inside the work process of business organisation Astra Zeneca effectively. According to Fagade et al. (2017), the main advantage of the Stride model of thread prediction is that it effectively reduces threat activities in an accurate mannerism such as data tampering, unethical activities of internal employees inside the business organisation of Astra Zeneca, impersonating someone identity for any motive fulfillment, Vital and confidential documents of the business leaks, information inaccuracies, technology and applications malfunctions along with lack of backups in the work process significantly. These are the main key risk element that continuously hampers the entire activities of health sectors and significantly severely compromises the patient's health and well-being. Hoe ever the thread model of TRIKE only can reduce such activities as unauthorised activities inside the organisation and Service denial. The majority number of risk factors and treats cannot get removed with the help of the TRIKE model of threat prediction (Venkatasen& Mani 2018). That is why the most suitable incident security handling model for the organisation Astra Zeneca will be the STRIDE model of threat prevention, as it has all the essential characteristics to meet the security requirements of the business work process. As a result of this modelling approach, the entire business functional process can remain uncompromised, and all the customers, as well as employees inside the organisation, can stay satisfied with the services and treatments of Astra Zeneca effectively; hence the brand reputation of this company also gets enhances in a significant amount without having any influence of external and internal over the company working process.
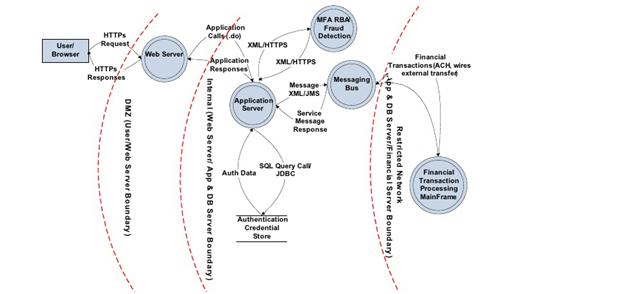
Figure 2: Data Flow Diagram
(Source: Venkatasen& Mani, 2018)
Implications and model practices to minimize risk impacts
As in the current industry, the rate of cyber-attacks is increasing and fighting back effectively for reducing all these cyber-attacks such as randomness, identity theft, data exploitation, and many more. As per Novokhrestov et al. (2020), to prevent these types of organisational attacks by hackers and any other threats during the work process. At the moment, the company knows that the privacy breach is happening in the work process. The breaching needed to be stopped by determining how this breach occurs: all entry and exit points must be monitored effectively to prevent these threats. Communicate with higher official parties is highly important as it helps to prevent or stop breaching as immediately as possible. Securing all the system applications in the business workplace is required for avoiding further data breaching activities significantly. Evaluation of each of the events needs to be processed to understand better the source of the data breach in the organisation. By following this process, the majority number of risk possibilities can be stopped.
Regulatory privacy and ethical implications of threat and Risk management
• Data privacy is thoroughly connected with the access of the data sources, collection of information and datasets, and these datasets' legal rights.
• Getting free access from unauthorised access to confidential and private datasets.
• They are misusing datasets.
• Accuracy in the process while collecting information.
• Data ownership and availability of the content of the information.
• Correcting and updating all the datasets.
• Following data privacy protocols such as international data privacy principles (IDPs).
Discussion and evaluation
Risk management
Highly experienced team management has also become possible with the help of a risk management approach inside the company Astra Zeneca. As opined by Schaad& Binder (2020), Risk management is the crucial function for the success of any business organisation as it reduces all possible risk factors inside the organisation for achieving success in future effectively. With the help of the risk management process, the organisation Astra Zeneca can easily spot troubles, and as a result, there will be fewer uncertain situations. This management process enhances the effective and quality decision making process for the company, improves good communication.
Role of audit for providing assurance
As per Nweke&Wolthusen (2020), the role of audit is significant in the process of providing assurance effectively. The auditing approach inside the company offers the ability to know related financial issues; company funds misuse frauds and any unethical activities. That is why this approach of auditing assures the company Astra Zeneca significantly.
Governance and compliance issues raised and the professional roles involved in threat management As per Nweke, Weldehawaryat&Wolthusen (2021), the most significant governance and compliance issues in the process of threat management are the issues related to rules and regulations of organisations, code of conduct, controlling employees behaviours and other regulatory norms generated from external sources effectively. Reasonable security standards can be processed within the organisation by the threat management process by handling this issue. Professional roles such as risk managers play essential roles in preventing threats, such as implementing risk policies inside the organisation for future prevention of Risks. In this way, organisations can accurately prevent threats with utmost efficiency.
Conclusion
The stride Threat model approach inside the business process is proven to be the most suitable approach for Astra Zeneca in reducing threats possibilities for the business and enhancing the working process effectively. However, with the rapid growth of technologies, different new security models such as Bell- LaPadula model and Clark Wilson model should be used if the risk and threats get too severe and started hampering the brand reputation significantly. All data sources' legal rights need to be adopted to prevent any unethical access of company confidential data sets and privacy data breaching process. The open communication process needs to be enhanced for establishing a better understanding of employees and customers. The most beneficial strength of the STRIDE threat model is that it can prevent all types of cyber-attacks in the business process, such as data tampering, fishing, system malfunctions, identity theft significantly. The most effective weakness of this model is that it is a very complex process to use because of the complex structure of the data flow diagram. Also, this model is very time consuming and requires highly skilled employees to handle this model with utmost accuracy. In this case, it is predicted that using the STRIDE model Astra Zeneca for a few years can maintain high quality security.
Reference List
Abbas, S. G., Vaccari, I., Hussain, F., Zahid, S., Fayyaz, U.
U., Shah, G. A., ...&Cambiaso, E. (2021). Identifying and Mitigating Phishing Attack Threats in IoT Use Cases Using a Threat Modelling Approach. Sensors, 21(14), 4816.https://www.mdpi.com/1424-8220/21/14/4816/pdf Awojana, T. B. (2018). Threat Modelling and Analysis of Web Application Attacks.https://thescholarship.ecu.edu/bitstream/handle/10342/7049/AWOJANA-MASTERSTHESIS-2018.pdf?sequence=1&isAllowed=y
Brethauer, R., & SE, S. (2018). Threat Modelling alsAusgangspunktfürsichere SW-Entwicklung.https://entwicklertag.de/karlsruhe/2018/sites/entwicklertag.de.karlsruhe.2018/ files/folien/3.%20ThreatModelling__2018_KA-ET_Publish.pdf
Fagade, T., Spyridopoulos, T., Albishry, N., &Tryfonas, T. (2017, July). System dynamics approach to malicious insider cyber-threat modelling and analysis. In International Conference on Human Aspects of Information Security, Privacy, and Trust (pp. 309-321).Springer, Cham.https://link.springer.com/chapter/10.1007/978-3-319-58460-7_21
Hossain, A., Salahuddin, A. Z. M., & Akbar, M. S. (2018). Threat modelling on nuclear and radioactive materials based on intelligent approach. International Journal of Nuclear Energy Science and Technology, 12(1), 19-31.https://scholar.google.com/citations?user=nLOABvUAAAAJ&hl=en&oi=sra
Jøsang, A., Stray, V., &Rygge, H. (2020, September). Threat Poker: Gamification of Secure Agile. In IFIP World Conference on Information Security Education (pp. 142-155).Springer, Cham.https://www.ncbi.nlm.nih.gov/pmc/articles/pmc7980870/
Kazansky, B. (2021). ‘It depends on your threat model’: the anticipatory dimensions of resistance to data-driven surveillance. Big Data & Society, 8(1), 2053951720985557.https://journals.sagepub.com/doi/pdf/10.1177/2053951720985557
Novokhrestov, A., Konev, A., Shelupanov, A., &Buymov, A. (2020, March). Computer network threat modelling. In Journal of Physics: Conference Series (Vol. 1488, No. 1, p. 012002). IOP Publishing.https://iopscience.iop.org/article/10.1088/1742-6596/1488/1/012002/pdf
Nweke, L. O., &Wolthusen, S. (2020). A Review of asset-centric threat modelling approaches.https://ntnuopen.ntnu.no/ntnu-xmlui/bitstream/handle/11250/2647234/Nweke.pdf?sequence=4 Nweke, L. O., Weldehawaryat, G. K., &Wolthusen, S. D. (2021).Threat Modelling of Cyber–Physical Systems Using an Applied ?-Calculus. International Journal of Critical Infrastructure Protection, 35, 100466.https://www.sciencedirect.com/science/article/pii/S1874548221000536
Ponsard, C., Ramon, V., &Deprez, J. C. (2021).Goal and Threat Modelling for Driving Automotive Cybersecurity Risk Analysis Conforming to ISO/SAE 21434.https://www.scitepress.org/Papers/2021/106030/106030.pdf Reski, A. S. T. (2019). “Open Weakness and Vulnerability Modeler”(OVVL): An Updated Approach to Threat Modeling.https://www.researchgate.net/profile/Tobias-Reski/publication/335164474_Open_Weakness_and_Vulnerability_Modeler_OVVL_An_Updated_ Approach_to_Threat_Modeling/links/5d569ccc299bf151bad77063/Open-Weakness-and- Vulnerability-Modeler-OVVL-An-Updated-Approach-to-Threat-Modeling.pdf
Schaad, A., & Binder, D. (2020, June). Ml-supported identification and prioritization of threats in the ovvl threat modelling tool. Information security assignmentIn IFIP Annual Conference on Data and Applications Security and Privacy (pp. 274-285).Springer, Cham.https://link.springer.com/chapter/10.1007/978-3-030-49669-2_16
Shaked, A., & Reich, Y. (2021).Model-based Threat and Risk Assessment for Systems Design.In ICISSP (pp. 331-338).https://www.scitepress.org/Papers/2021/101872/101872.pdf
Skobalj, N. (2019). Validating vehicleLang for Domain-specific Threat Modelling of In-vehicle Networks.https://www.diva-portal.org/smash/record.jsf?pid=diva2:1304913
Vallant, H., Stojanovi?, B., Boži?, J., & Hofer-Schmitz, K. (2021). Threat Modelling and Beyond-Novel Approaches to Cyber Secure the Smart Energy System. Applied Sciences, 11(11), 5149.https://www.mdpi.com/2076-3417/11/11/5149/pdf
Venkatasen, M., & Mani, P. (2018).A risk-centric defensive architecture for threat modelling in e-government application. Electronic Government, an International Journal, 14(1), 16-31.https://www.researchgate.net/profile/Maheshwari-Venkat/publication/320873035_A_risk-centric_defensive_architecture_for_threat_modeling_in_e-government_application/links/5c936e17a6fdccd4602eb31f/A-risk-centric-defensive-architecture-for-threat-modeling-in-e-government-application.pdf
Yuva Kumar, J. N. (2019). Behavioural Based Threat Modelling to Increase the Efficiency in Breach Identification and Notification (Doctoral dissertation, Dublin, National College of Ireland).http://norma.ncirl.ie/4176/1/joshuanevilrajyuvakumar.pdf












