Information Security Assignment On E-FAIL & KRACK Attacks
Question
Task: This assessment asks you to apply what you have learnt on the module to two recently discovered, very high-profile vulnerabilities, are commonly referred to as E-FAIL (original paper here: https://www.usenix.org/conference/usenixsecurity18/presentation/poddebniak) and KRACK (original paper here: https://papers.mathyvanhoef.com/ccs2017.pdf). Answer the following questions in part a for E-FAIL, and part b for KRACK. I expect answers to be between 4 and 8 pages in total.
Question 1:
Research each attack and explain the cryptographic weaknesses that make the attack possible, and explain how the attack is performed.
Question 2:
Explain what can be done with the E-FAIL and KRACK attacks? What do each of them allow an attacker to do, and what kind of access does the attacker need?
Question 3:
Assume you have been asked by a business to assess the risks these attacks pose to them. Write some advice for the business. Can the business know if the attacks were used against them? State what the impact of the attacks might have been and what the business should do.
Complete your assignment from here (heading styles have been set up to assist you in this work) (Delete the instructions before you save and submit your work):
Answer
1. Introduction
Information security or infosec is an important part that must be a concern in every business culture. To answer this question mentioned in the information security assignment, we only concern in two crucial parts that is E-FAIL data and KRACK data. The major purpose of the report is to determine risk factors leading cyber-crimes and threats in the compiting devices and review E-FAIL and KRACK attacks. These two-part have been answered well according to a given question as described below within this information security assignment.
1.1 Cryptography and Data Security
2. Question 1.
Research each attack and explain the cryptographic weaknesses that make the attack possible, and explain how the attack is performed.
3. Answer for Question 1.
Cryptography is a method to protect and securely send the data to the receiver. It protects the data secure online transactions by using the codes so that only the receiver can understand or encrypt for communication between two systems. Crypt means "hidden," and graphic stands for "writing". It is found herein information security assignment that cryptography include public keys which are easily accessible by the hackers using malicious codes. Moreover, the attackers transfer unauthorized activities that cannot be maintained by the cryptography systems and provide a way where hackers can perform data breach and hacking related activities.
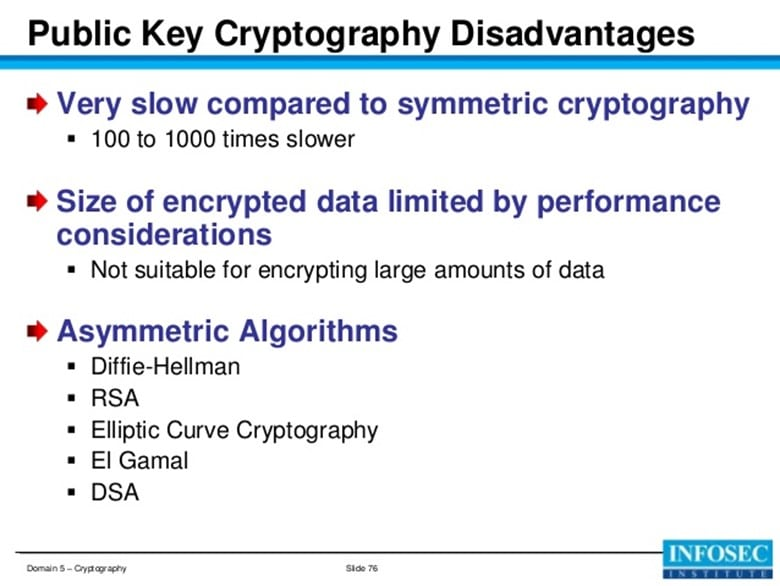
Figure: Disadvantages of cryptography (INFOSEC, 2018)
3.1 E-Fail Attack.
Acording to the research on information security assignment, E-Fail is an attack that targets the encrypted emails, and this can be done by changing or formatting the encrypted standards or by specific vulnerable clients.
It is a Security hole present in the emails. Most of them use the HTML or JavaScript, so it is easy for the attacker to attack the content of the email. The encrypted form transmits the content. Mostly affect Gmail, Microsoft Outlook, and Apple mails.
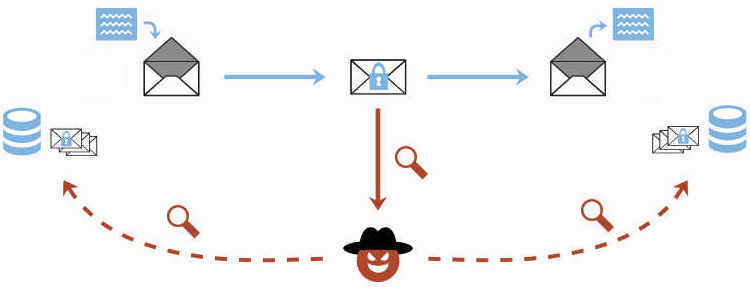
Figure: E-FAIL attack process (E-FAIL, 2018)
E-Fail mostly attacks the breakable OpenPGP and S/MIME standards to display the encrypted emails which have plaintext. (Nikiforakis el-al,2019).
In an email, an attacker needs access to the message which is present in the email, which is in encrypted form and ability to send the email to at least one of its regular recipients of the original mail.
The attack is performed in two ways as illustrated below within the information security assignment:
a. Direct Filtration: To access the decrypted content of the encrypted mail, the attacker modifies the message in a particular way or a specific way and then sends the changed email to the recipients. It is stated herein information security assignment that to create the MIME, the attacker adds the additional part before and after the encrypted text of the encrypted mail as a parameter value of the HTML tag.
Here, the attacker creates three multiple body parts:
(1) First is IMG tag this tag the link is open with quotes but not closed.
(2) The second part is s/MIME Ciphertext.
(3) The third part contains the body HTML, which closes the img tag of the first part.
Now, the recipient receives it in some different format. In an email, all the non-printable are written in %20, which is whitespace and requests it from the img tag, which contains plaintext. Thus, it is seen herein information security assignment that the attacker receives the plaintext from the victim's client.
b.CBC/CFB Attack
This attack examined in the information security assignment exfilters the plaintext using the CBC/CFB gadgets. In CBC mode, if the attacker knows the plaintext, it can modify plaintext blocks. It is used in S/MIME, and CFB is used in Open PGP, which is very similar to CBC properties. In this attack, the attacker already knows the first block. Then she tries for other blocks by injecting the img tag in the encrypted plaintext. (Poddebniak and Dresen, 2018).
The weakness of the attack is mentioned below within the information security assignment:
(1) PGP/S-MIME using the end – to –end encryption for the emails.
(2) The attacker already has information about the encrypted messages.
(3) The victim is at risk, and it processes the encrypted email messages and renter HTML.
3.2 KRACK Attack.
Depending upon the configuration of the network, it is possible to inject the data and manipulate it in some code language. An example attacker can inject the websites by adding different types of malware activities.
Krack stands for Key reinstallation Attack. According to the investigation on information security assignment, it is responsible for stealing the data which is transmitted over the network, which uses Wi-Fi's WPA security protocol. The data which is very sensitive like login credentials, credit card details, private chats, or any kind of data which victim transmit over the web. It includes man-in-the-middle attacks to hack the website or inject any kind of code on the website.
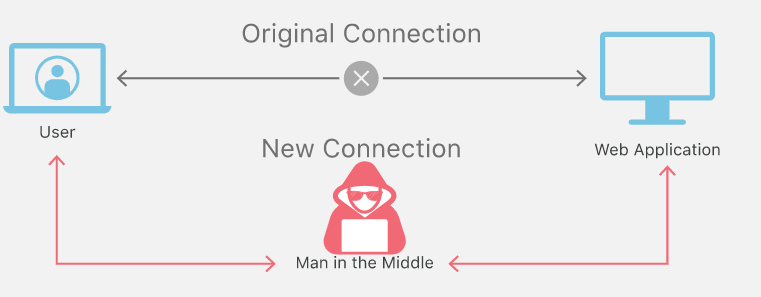
Figure: KRACK attack (Cloud Flare, 2018).
Method:
- The encrypted WPA, which is secure encryption used to protect the communication of a user's device and the device, which is providing Wi-Fi, so the WPA uses a four-way handshake sequence. However, it is clear on this information security assignment that for retransmission, only the third part of the four-way handshake is required. When the victim reconnects to the already used Wi-Fi network, it resends them the third part of the handshake sequence, and the key can send and times in the third part of the handshake sequence. If the attacker makes a count on it and revises all the retransmissions, then the encryption can be broken.
- Each time the victim sends the request over the Wi-Fi for re-connection, the attacker tries to resend the third part of the handshake to the victim's device, once the victim accepted the request, and then the decryption is started. (Chacos and Simon, 2017).
- Now the victim is in the loophole of the attacker, and now the attacker has all the track of information passing over the network within the same range.
- The condition for attacking is that both should be connected to the same Wi-Fi network.
The weakness of the process illustrated in this information security assignment are:
- Not using the standard HTTPS security for protection.
- Antivirus software is not updated on computers.
- Use of the same encryption key for protection, which is already being used in the past.
- The problem in WIFI standards.
4. Question 2 of information security assignment.
Explain what can be done with the E-FAIL and KRACK attacks? What do each of them allow an attacker to do, and what kind of access does the attacker need?
5. Answer for Question 2.
5.1 E-Fail Attack.
There are two types of ways to avoid this attack as discussed in the next section of information security assignment:
1.Short term:
- Switch off HTML rendering, and mostly the attack has been made in img tag, styles, so switching off the display of HTML tags or forms in the mail can reduce the risk of the attack.
- Any URL in the decrypted form now appears as text, now there will be a button so to toggle that, and if nothing is wrong that it will open and can read the email safely.
2.Long term:
- The use of decryption in the email client should not be done. The best way to avoid the attack is to decrypt email MIME or PGP in another app, which is outside of the email client. Remove the MIME or PGP secret keys from the client's email, then open the encrypted email, paste the ciphertext into another app which done the decryption. It will prevent the exfiltration channels of email clients.
- As mentioned herein information security assignment, the attacker needs access to the emails which use S/MIME, but condition here is it should be sent over an HTTP connection or a compromised email server, then only this attack can be possible. After knowing the encrypted email, the attacker can add the extra attributes in the tags, which is received by the victim's client.
Figure: Protecting methods against Krack (Cloud Flare, 2018)
5.2 KRACK Attack:
If the attacker has access over the Wi-Fi, then it can steal all the private information, sensitive data, credit card details, or anything which is transferred over the network.
The findings obtained in the information security assignment illustrates that an attacker within the Wi-Fi range captures the secret key, and force the victim to connect to the network which the attacker has created. Once the victim accepts that, then attacker know can encrypt its security related to any of the credentials.
An attacker can intercept between the traffic of the device and the router through which information is exchanged, but if traffic is encrypted by https, then the attacker cannot look into the traffic. By this attacker does not have access to the WIFI password, but it can make changes in the traffic, which is unencrypted. With some help of tools, it can inject some packets which can be harmful to the device. (Vanhoef el al.,2017)
a.Example:
(1) If anyone is using IoT devices, then the KRACK attack is a significant concern for them. If they have installed a connected security camera is in their house, which does not encrypt traffic when connected to the same WIFI network, an attacker can snoop on raw video footage of the house, which is very risky.
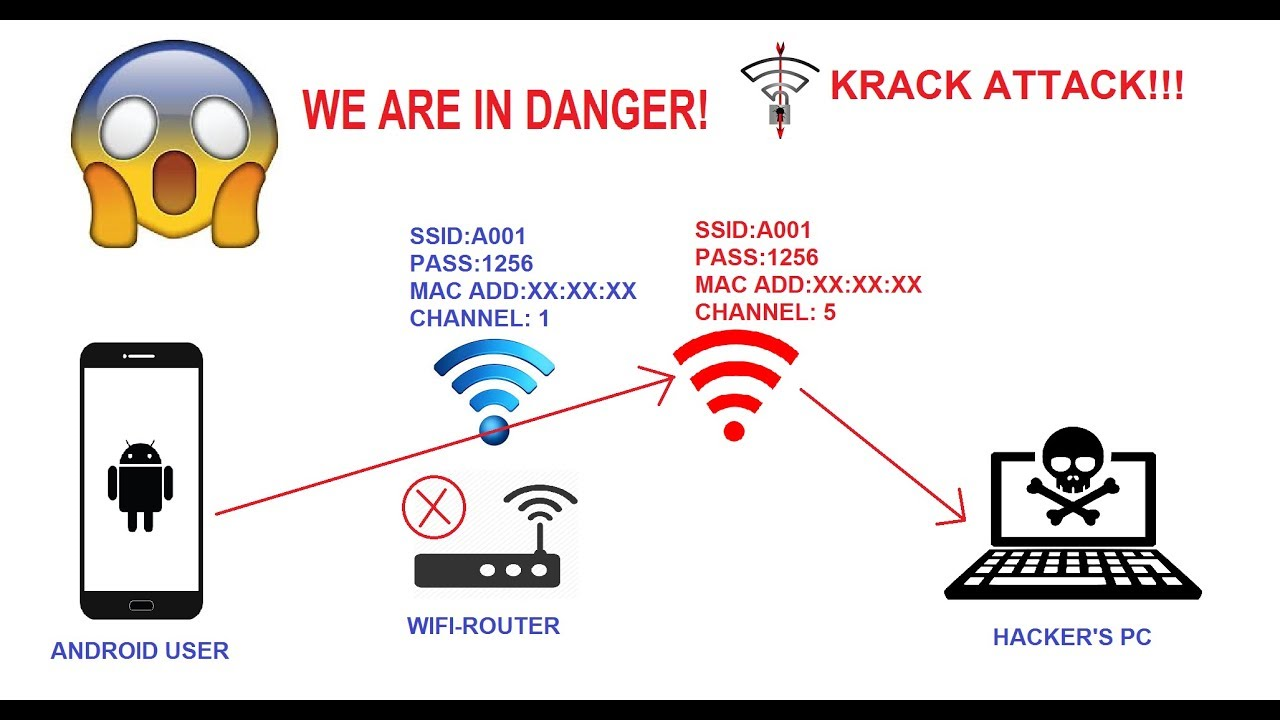
Figure: KRACK wifi attack (Cloud Flare, 2018)
b. Best ways to avoid the attack is outlined below within the information security assignment:
(1) Do not use public hotspots even if they are password-protected at the coffee shop or airport.
(2) Do not use the same secret key over and over again, makes changes in the secret key.
(3) Try to use Encrypted traffic solutions like HTTPS.
(4) Update all WIFI devices and routers with the latest security patches.
6.0 Question 3 of information security assignment
Assume you have been asked by a business to assess the risks these attacks pose to them. Write some advice about the business. Can the business know if the attacks were used against them? State what the impact of the attacks might have been and what the business should do.
7.0 Answer for Question 3
7.1 E-Fail Attack:
A real estate company was worried about the attacks going all around. He has heard about the issue of the hijack of email or data manipulation in the emails.
So his business can get attack by this as:
- His email can get attack by the E-fail. As he sends emails regarding the location of the building to the client every time. He is even not using or does not know anything about the attack. So explained the scenario if he gets attacked, then what will be the risks attached to it.
- The server that he was using was not at all protected and was using HTTP, not the https network. So he can easily get attacked by the attacker. Every time he can lose one client as a client can receive the wrong address in an email or can get an error while opening the image, by this client will get lose interest in his property.
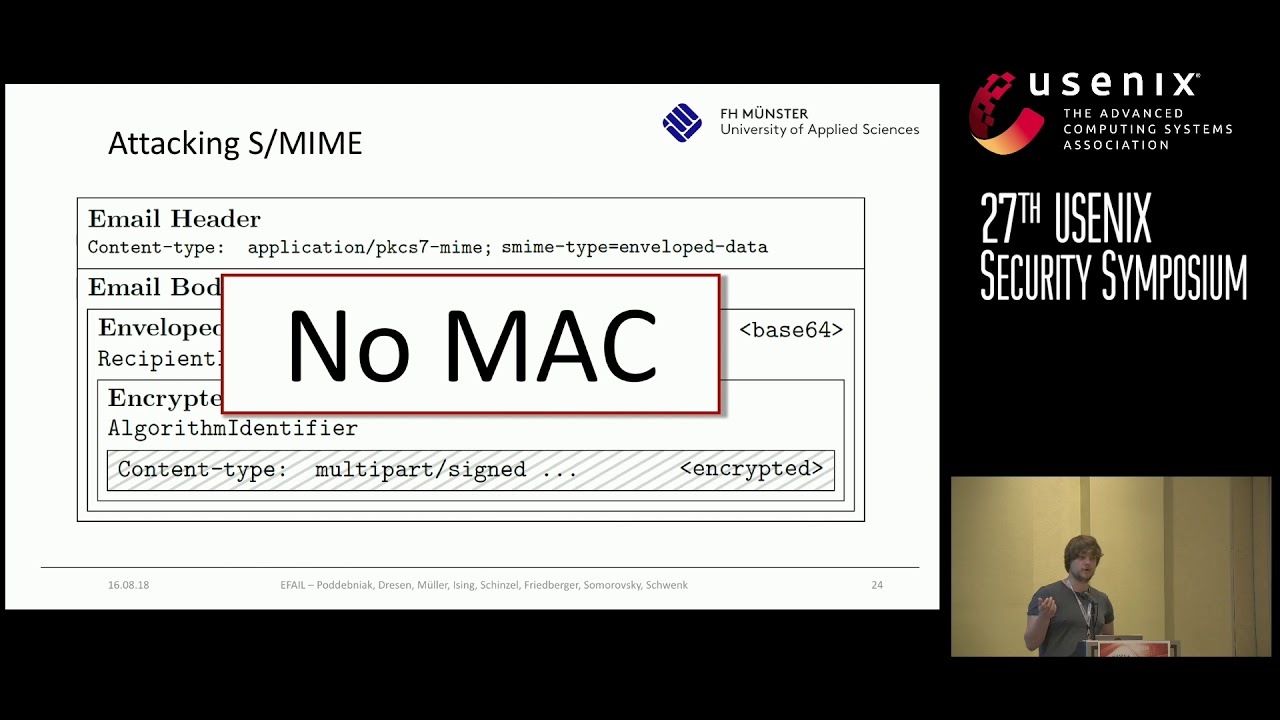
Figure: E-fail attack example (E-FAIL, 2018)
Advice for the business:
- The business should use the https network.
- Disable all its Html rendering as the attacker can use img tag to send the wrong output to the victim's client.
- It should arrange for more secure end to end channel such as temporarily
should stop sending encrypted emails, especially PGP encrypted one.
Attacker advantages:
- He can send his address in place victim's address. He can steal his customers for the benefit of his own.
- He can access the encrypted mails of the victim, so he has a track of his all private conversation done via mail.
- He can misguide all the customer's victims has via mail.
7.2 Krack Attack:
The readings considered to prepare this information security assignment signifies that a client who has a Business of real state can get suffer from the Krack attack as the victim has started his new business and created a portal for all the customers to visit the website and register to get bonus points and put referral codes for the customers.
The client travels most of the time for a business meeting, and he also connects his laptop to any kind of WIFI, as an example the airport Free WIFI hotspot; he never takes care of any kind of messages prompts up when connecting to the network.
The risk his business can face is
- If the attacker took him into his loop whole while connecting to Wi-Fi at the time of the airport, then the attacker will have all the details of login credentials.
- An attacker can get access to all his credit card details if they are save in the browser.
- An attacker can attack the portal can damage the things in seconds.
Advice for the protection of his business:
- Whenever he login to a website, make sure the connection which he is using is encrypted.
- Also, make sure the connection which he is using stays encrypted for the protection of all the secret keys.
- To encrypt web browsing, make sure to use a virtual private network.
Impact on the business of this attack can cause a loss in the clients, and all his private data can steal, which results in downfall for the business.
8.Summary
From above evaluation on information security assignment, it can be summerized that the presence of unauthorized activities and malicious programs lead security concerns in the cryptography systems. This report reviewed the weaknesses of cryptography and also analysed major two attacks including E-FAIL and KRACK attacks. It is found that E-FAIL is a leading cyber-attack where the attackers obtain data from the e-mials through fraud and spam signals. This research provided a way to enhance skills about information security and also highlighted the key vulnerabilities and threats asocoaited with the computing networks and systems. So, based on the readings developed within this information security assignment it is suggested based that companies must include effective security systems and tools and protect data using cryptography systems in order to address security vulnerabilities and attacks.
9. References
Chacos, B. and Simon, M. (2017). KRACK Wi-Fi attack threatens all networks: How to stay safe and what you need to know. [online] PCWorld. Available at: https://www.pcworld.com/article/3233308/krack-wi-fi-security-flaw-faq-tips.html.
Johns, M., Nikiforakis, N., Volkamer, M., & Wilander, J. (2019). Web Application Security (Dagstuhl Seminar 18321). Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik.
Jose, T. T. Tomy, V. Karunakaran, Anjali Krishna V, A. Varkey and Nisha C.A., "Securing passwords from dictionary attack with character-tree," 2016 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, 2016, pp. 2301-2307.
Poddebniak, D. and Dresen, C. (2018). [online] Usenix.org. Available at: https://www.usenix.org/system/files/conference/usenixsecurity18/sec18-poddebniak.pdf.
Rehman, I. (2018). information security assignment What Is A Brute Force Attack?. [online] The Official Cloudways Blog. Available at: https://www.cloudways.com/blog/what-is-brute-force-attack/
Vanhoef, M. and Piessens, F., 2017, October. Key reinstallation attacks: Forcing nonce reuse in WPA2. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security (pp. 1313-1328).
INFOSEC, (2018) A Review of Asymmetric Cryptography. [online]. Avialable at: https://resources.infosecinstitute.com/review-asymmetric-cryptography/#gref [Accessed 25/06/20].
E-FAIL, (2018) EFAIL. [online]. Avialable at: https://efail.de/ [Accessed 25/06/20].
Cloud Flare, (2018) What is a KRACK Attack? | How to Protect Against KRACK Attacks. [online]. Avialable at: https://www.cloudflare.com/learning/security/what-is-a-krack-attack/ [Accessed 25/06/20].












