Information Security Assignment: Discussion on SQL Injection Attacks
Question
Task:
Information Security Assignment Instructions:
Students will be familiar with the tools used by hackers and crackers and be aware of ways of identifying and rectifying security breaches and they will be able to collect digital evidence and understand the rules of evidence gathering.
Custom projects should have clearly defined aims, objectives, and targets. If you seek to propose your own, you should draft a proposal. In doing so, projects can be evaluated so they can be achieved and meet suitable quality. Some security projects will be provided where you have the opportunity to collaborate with some Swinburne researchers. There will be a fixed set of projects, and these will require a high skill level and time to complete.
Part A
This question is compulsory. You need to prepare a documentation/specification to show how you implement the tool/tools. This part of the assignment requires you to know how to prepare a documentation/specification in applying a tool to real-world security problems.
In part A, you are required to include the following:
• Brief explanation on the method used (a couple of paragraphs) followed by details on what’s your assumption /expectations regarding the results of the method that you actually tested/chose.
• A detailed documentation/specification about how to use the tool. In other words, a complete, beginning to end, tutorial like presentation of the experiment, including screen shots, this could look like a manual or a journal.
• Any script code and images (screen dumps) showing the successful completion of the tasks in this part of the assignment.
Part B
You will provide a complete run through the activity; you will provide screenshots of how the tool was run and also an evaluation of the data you are using. In part B, you are required to include the following:
• Analyse either successful or unsuccessful experience.
• A theoretical description of the attack. If for example you decide to run a spear phishing attack, you will need to provide around 300-500 words describing the attack in detail.
• An evaluation of the data, in any given case.
• Provide a short evaluation and considerations of the attack, this can and should also include defence mechanisms which can be used to defend from such an attack. Please note, this should be done thoroughly and present various mechanisms and description of which you consider to be better and why. For example, for a DoS attack where the attacker has spoofed the IP address, there are a number of mechanisms to trace back the attacker, you should include most of them.
• Attack results or experimental results discussion. You will need to show what can you see from your experiments and are there any differences between the expectation and your findings, Why?
Answer
Introduction
As seen in this information security assignment, there are various vulnerabilities and threats that are associated with the web applications. One of the most significant out of these is the database injection threats. SQL injection attacks are common that involve the malicious queries to extract significant information. The occurrence of these attacks can result in the violation of security and privacy of the information present in the database. There is unauthorized access that the attackers can obtain over the database which can then be misused(Axinte, 2014).
Part A
SQL Based injection attacks
The SQL-based injection attacks are classified in different types and categories. These include classic attacks, blind attacks, database specific attacks, compound attacks, etc. as some of the types. There are several tools that have been developed to detect and control these attacks. BSQL Hacker is one of the automated detection tools that can be used against blind, time-based, deep blind and error-based attacks(Atoum and Qaralleh, 2014).
SQLMap is one of the open-source tools that provide support to a large number of servers, such as MySQL, MS Access, Microsoft SQL Server, and a lot more. The tool comes with a wide range of features.
There are different forms of SQL injection attacks that have been developed by the malicious entities. Error-based injection is one of the most common type in which a malicious query is injected in the database and it results in certain form of an error. The errors are quite generic which makes it difficult to identify the attacks. The use of comment line is often done in these attacks which results in ignoring the valid parts of the query.
Union-based SQL injection attacks are also launched by the attackers. The use of union command is done in these attacks which results in the execution of additional query. The use of malicious inputs is done to generate the malicious queries.
A popular form of SQL injection attacks is the blind injection attack. It is not known if the web application is exposed to these attacks or not. Hence, the term as blind injection attack is given to these SQL injection attacks. There are further classifications that are done under these injection attacks. Boolean attack is one of the types in which the wrong queries do not give any result. Another form of blind injection attack is the time-delay attack. There are conditions that are set up which are used to set up a specific time delay which is then used to execute the attack.
The classification of the attacks is also done on the basis of the input type that is provided. These are classified as string input and integer-based injection attacks. In the former, the outcomes of injection cannot be viewed in the real-time.
The different tools have been listed which can be used to prevent the SQL injection attacks. There are other mechanisms that can also be used to prevent the SQL-based injection attacks. The use of dynamic SQL shall not be done which can assist in the automatic reduction of the attack vector and the attack surface. The utilization of the sanitization protocol shall also be done to keep a track of the inputs provided by the user. The controlled inputs can also have a significant impact on the prevention of the SQL injection attacks. The use of an advanced and strong WAF protocol shall also be done. This will also result in the protection of the databases in general and the SQL injection attacks can also be avoided in this manner.
Scenario, testing plan and vulnerability detection of database
The testing plan for this case is simple. I will find a website using some search parameters that appears to be insecure and exploitable for SQL bases injection attacks. This website will also ideally not have https security. In order to prevent any actual damage and at the risk of causing privacy or legal issues, I will not be actually retrieving or exploiting the site. I will be using SQLMap to do the scanning of vulnerability and will describe my experience here. SQLMap will be on a Ubuntu 18.04 LTS based host. The reason to select this tool is because it’s a very simple as well as a very powerful tool that can actually detect and identify vulnerabilities on a live website and even exploit them(Cherry, 2015).
Tool overview
Installation
The installation of the tool is done after updating dependencies on the host system. The installation on Ubuntu for instance can be carried out using: sudo install apt-get sqlmap
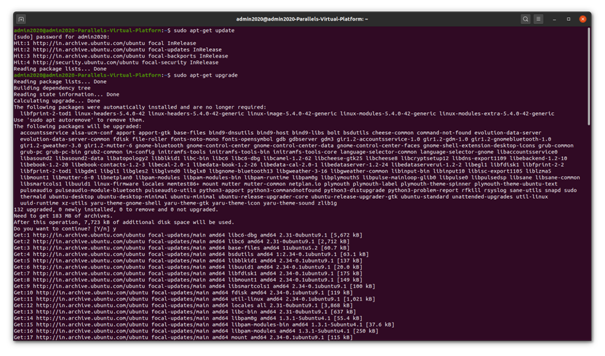
Figure 1 - Update Dependencies
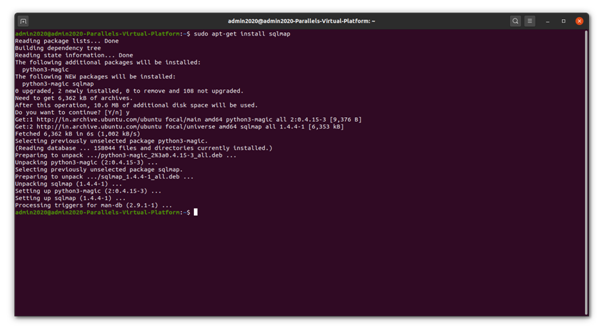
Figure 2 - SQLMap Installation
Execution
The tool can be executed using ‘sqlmap’ command and it shows the following help and documentation. It shows two level of helpful information, the below depicted is the level 1.
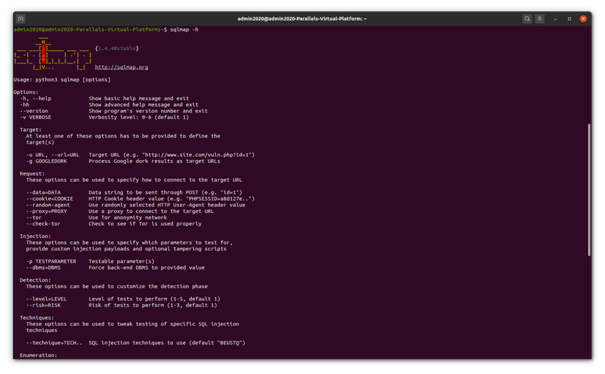
Figure 3 - SQLMap Help Command
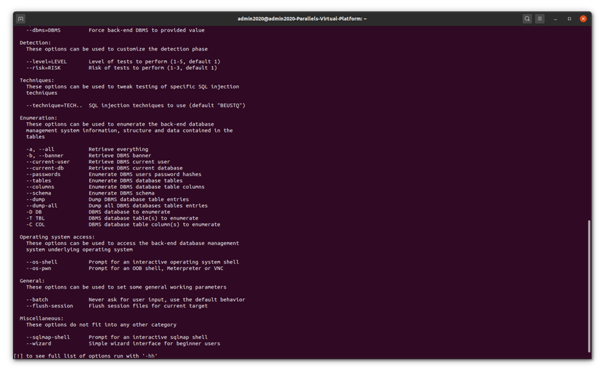
Figure 4 - SQLMap Help Command Contd
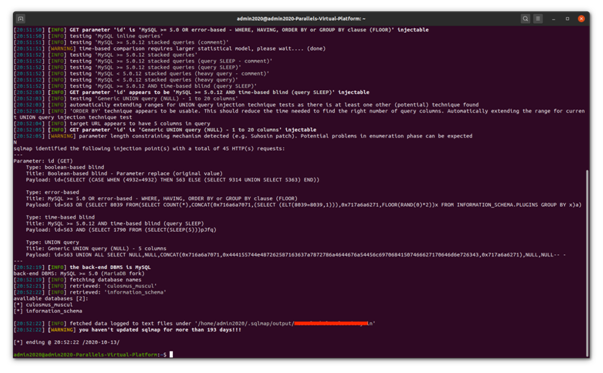
Part B Figure 5 - SQLMap Target Recon Figure 6 - SQLMap Target Recon Contd. The details enumeration is another feature of the tool that provides the mechanism to mention and include the details of the database system of the target system. The use of the command can be done to enumerate all the components of the database as tables, rows, and columns. The following are some of the commands that shall be included as: The database dumping/extraction are another feature that is one of the significant features of SQLMap. The use of the following commands can be done to dump the database. • sqlmap -u 10.10.10.10/ With the use of the above features and additional scanning, it could be determined that the Nginx web app server is involved with MySQL 5.0 as the database. The name of the database is also identified with use of the commands and features(Kusuma, 2018).
Figure 7 - SQLMap Vulnerability Identification This allows database dump and also the injection when exploited. Hacking the system Countermeasures Escaping Disable administrative rights Web application firewall Conclusion References Axinte, S.-D. (2014). SQL Injection Testing in Web Applications Using SQLmap. International Journal of Information Security and Cybercrime, 3(2), pp.61–68. Cherry, D. (2015). Securing SQL server?: protecting your database from attackers. Waltham, Ma: Elsevier/Syngress.
Ciampa, A., CorradoVisaggio and Massimiliano Di Penta (2016). A heuristic-based approach for detecting SQL-injection vulnerabilities in web applications.Information security assignmentAcm, 2 Penn Plaza, Suite 701, New York, Ny 1-, Usa 05-02. Dharam, R. and Shiva, S. (2014). Runtime Monitoring Framework for SQL Injection Attacks. International Journal of Engineering and Technology, 6(5), pp.392–401. Kroenke, D.M. and Auer, D.J. (2016). Database processing?: fundamentals, design, and implementation. Boston: Pearson.
Kusuma, G.H. (2018). Analysis of SQL Injection Attacks on Website Service. bit-Tech, 1(1), pp.26–33. Mahrouqi, A., Tobin, P., Abdalla, S. and Kechadi, T. (2016). Simulating SQL-Injection Cyber-Attacks Using GNS3. International Journal of Computer Theory and Engineering, 8(3), pp.213–217.
Evaluation
It is essential to determine the details of the target system while using SQLMap as the tool. The use of the ‘sqlmap -u 10.10.10.10/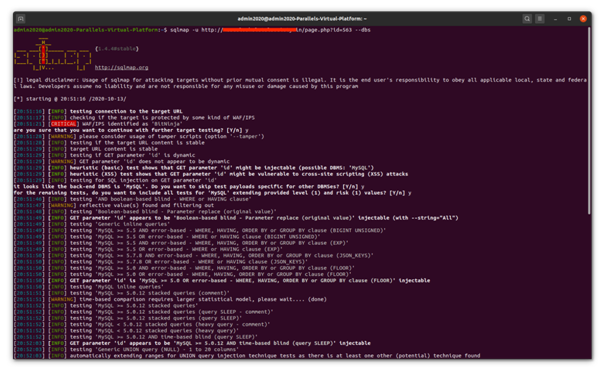
• sqlmap -u 10.10.10.10/
• sqlmap -u 10.10.10.10/
• sqlmap -u 10.10.10.10/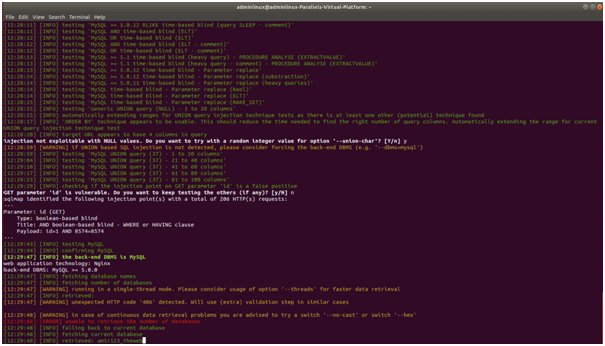
Once the vulnerability has been identified, SQLMap can be further used to exploit the vulnerability. Not only it can be used to extract valuable information but can also be used to exploit them. First and foremost, the number of tables present in the database system can be carried out. This is done by executing ‘sqlmap -u xxx.xxxxxxxx.xxx/xxxxx.php?id=1 -D xxxxx --tables’ command. The ‘D’ in the command chainsignifies the name of the database. The use of ‘sqlmap -u xxx.xxxxxxxx.xxx/xxxxx.php?id=1 -D xxxxx-T xxxxx –columns’ command can be done to return a column. The outcomes obtained will comprise of the user credentials that can then be utilized to log in to the database. Often, the passwords used on the database are encrypted. It is possible to decrypt these passwords with the use of the hashing techniques.
Input validation
The use of the authentication scheme is done to determine if the data involved and requested by the user is valid or invalid. The techniques provides the confirmation on the database length, size, type, and likewise. The values that pass the data authentication will be processed ahead.
The use of the character-escaping technique can be done for determining the user-furnished details. The inclusion of the technique is done to validate the system with the SQL statement used by the developer.
The application shall not be connected with the database through the root access profile. It shall be conducted only when it is necessary as the database access can be obtained by the malicious entities(Kusuma, 2018).
The determination of the SQL injection attacks can be done with the aid of the web application firewall, WAF. The use of the firewall shall be done so that it can be utilized with the web servers to determine the web traffic as it passes through the web server. The determination of the specific threat patterns will also be done. This will be installed between the network and the web application(Mahrouqi et al., 2016).
The database injection attacks can have the significant impacts on the security and privacy of the data sets. The use of the automated tools can be done to make sure that the significant handling and management of the attacks can be done so that the detection and prevention of these attacks is possible.
Atoum, J.O. and Qaralleh, A.J. (2014). A Hybrid Technique for SQL Injection Attacks Detection and Prevention. International Journal of Database Management Systems, 6(1), pp.21–28.












