Data Management Assignment On Medical Data Security
Question
Task: Write a data management assignment critically evaluating the cloud computing and IoT with respect to medical data security.
Answer
1. Introduction
1.1. Research background of data management assignment
As stated in the data management assignment, modern businesses currently focus on cloud computing methodologies due to deduced cost and infrastructure requirements. Processing of big data to facilitate the modern business processes are in practice globally where efficient data management and security are the major factor to eliminate disruptive functionality. Security measures in case of cloud computing is based on traditional security management processes which could be controlled and monitored from data centers irrespective of location. Medical section globally uses big data in order to support patient data management process and global sharing. Prominent global medical institutions started shifting traditional data management processes to cloud computing methodologies due to less infrastructural requirement and cost. There is a big contribution of traditional data security such as data masking, data integrity checking and inscription etcetera. Incorporating data security in case of medical data is an essential approach to order to secure personal information, medical history and medical processes.
The usage of IoT in functional sectors is exponentially increasing where connected devices are used to increase productivity. The global medical sectors are currently adopting IoT or devices to monitor patients and store patient’s data at different locations. With the increase of usage of IoT, there need to data security in order to secure patient’s personal data, medical history and medical procedures. Modern medical facilities currently preferring shared information through IoT to facilitate faster treatment process and to increase productivity. There are various IoT security frameworks in use across industries to secure data and to prevent data breaches or risks.
Global health care sectors are adopting modern technologies such as IoT and cloud computing methodologies that contributes to the efficient data management and globally shared information. The heath care sector utilizing the big data through centralized data centers in order to facilitate medical research and treatment plan. It is evident in the data management assignment that adoption to modern technology brings forth the necessity of data security to avoid data breaches and risks associated with data management or analysis. Cloud computing facilitates efficient data management and computing processes for the medical data which needs traditional data security approach associated with cloud computing and IoT. There is a big significance associated with security measures that could be incorporated by traditional security methodologies such as encryption, masking and secure deletion etcetera.
1.2. Rationale
There are various factors that have been forming the basis of current research approach used herein data management assignment. Modern medical institutions are adopting trending technologies in order to facilitate the medical research process, patient management and data sharing. Cloud computing has been contributing to virtual IT infrastructure that incurs less cost less traditional IT infrastructure measures. Virtual IT infrastructure enables organizations to compute efficiently and could be associated with big data. Adaptation of cloud computing is associated with data security measures in order to eliminate data security issues and risks associated with global data sharing. Traditional data security measures could be adopted for the cloud computing methodologies in case of medical data management and computing techniques. The current research approach also focuses on security parameters associated with shared information in medical IoT devices. The efficiency of medical data management could be facilitated with data security framework for cloud computing and IoT which needs significant analyses and research to contribute future technologies adaptations and risks associated with technological transformation in order to reduce the functional disruption and data breaching risks.
1.3. Problem statement
The utilization of cloud computing and IoT in medical data management needs simultaneous data security measures based on traditional data security and applied data security frameworks. Medical data is consisting of patient’s personal data, medical history, transaction history and treatment plan etcetera. The big data associated with medical sector has been utilized in order to facilitate data computing and data sharing. The research on data management assignment analyses methodologies associated with data security in case of adoption of cloud computing and IoT. The factors associated with medical data security need to be analyzed for the understanding of the suitability in case of modern technological adoption and facilitation.
1.4. Aim
The aim of the research on data management assignment is to investigate the security aspects of adaptation of cloud computing and IoT in case of medical data management and security.
1.5. Research questions
- What is the security parameters associated with medical data management?
- What are the impacts of cloud computing in medical data security?
- What are the impacts of IoT security framework in medical data security management?
1.6. Statement of hypothesis
“Traditional cloud computing techniques and IoT security frameworks contributing to medical data management and security”
1.7. Ethical considerations
There are various issues and challenges associated with secondary data research on data management assignment. The primary issue is associated with harming consent and identification. De-identification of data needs to be done in order to facilitate consent associated with research approach. Obtaining consent or proper referring of data need to be done whereas reidentification of resources need to be done to maintain ethical consideration in case of secondary research.
1.8. Overview of the methodology
Deductive approach: deductive approach considered in the data management assignment helps researcher to develop hypothesis on basis on secondary data collected from reliable resources. Deductive approach has been adopted in the current research approach.
Positivism philosophy: positivism philosophy has been adopted in the current context of data management assignment that derives positive and logical information in the current research approach.
Secondary qualitative: data would be referred from secondary resources available in the form of articles, research papers and online resources.
2. Literature Review
2.1. Concept map
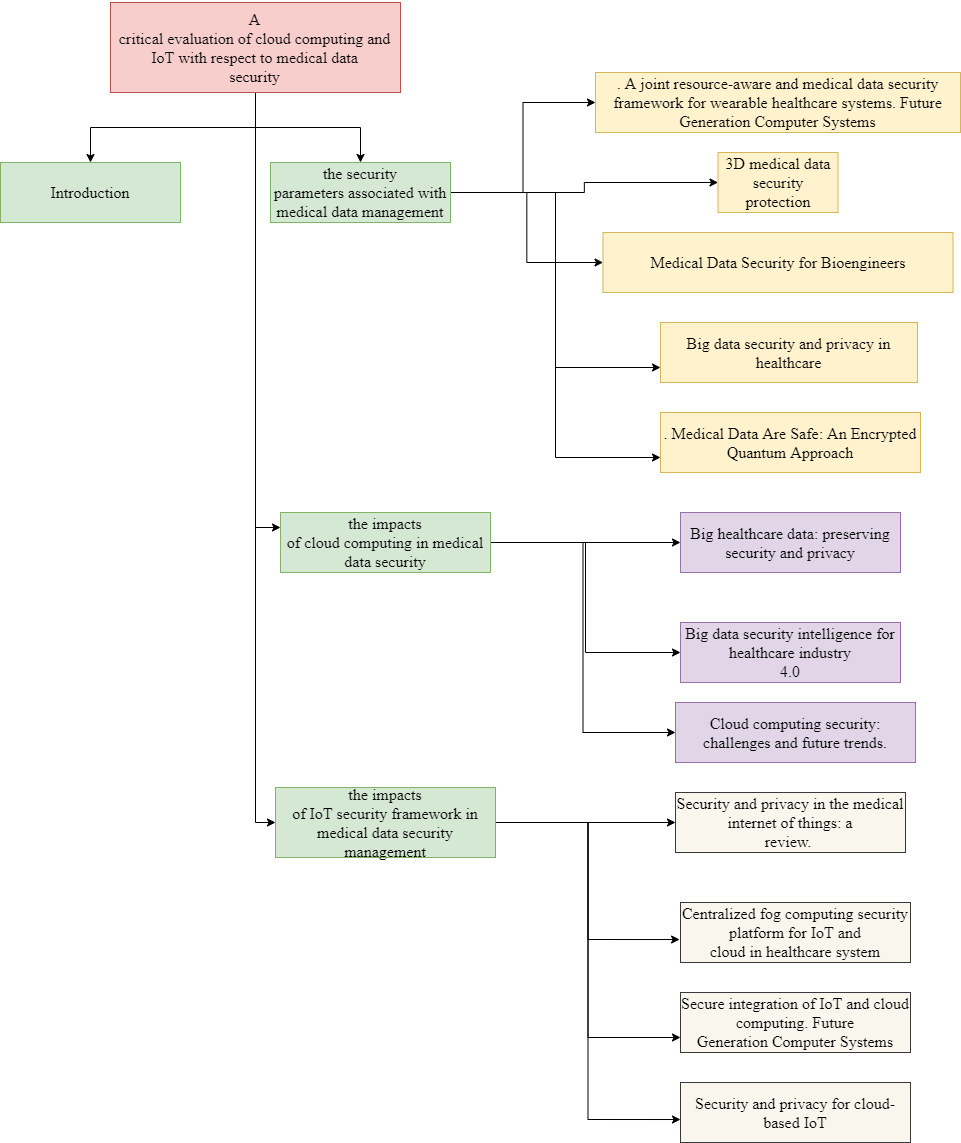
2.2. Introduction
This part of the current research on data management assignment discusses on the different existing literatures that have been taken to conduct the research process. There are three objectives of the literature review. The first part focuses on the security parameters for the healthcare data management. The second objective is to focus on the impacts of cloud computing in the healthcare system. The third part emphasizes the security management in the healthcare systems. Cloud computing is a necessary element of healthcare system in the recent times. The gaps within the technology need to be resolved for the betterment of the healthcare systems. It Wil also help in preventing the cyber-attacks.
2.3. Objective 1
The current referred paper talks about a security framework based on biometrics. The framework aims to monitor and regulate the wearable health of the constrained resources which extracts heartbeats from ECG signals [1]. In recent times securing the medical data has become crucial. The current trend in technology enhances that the cloud computing in medical sector proposes a framework that helps both the social and economic significance of the data. This paper on data management assignment intends to give an idea of secure image and communication archiving technology in the healthcare institutes. In most of the cases, due to the lack of encryption, various personal data including the images are exploited by malicious users. The mentioned article talks of a certain technology that prevents these kinds of activities [2]. It focuses on the cloud computing in healthcare system and aims to identify the security technology. The aim of this current referred article is to analyze the existing methods, equipment and systems used for data security in the healthcare institutes. The medical data could either be the medical signals or images.
The privacy preservation is necessary for this information. The different features, characteristics and functions of these tools are discussed in the article [3]. The motive of this research paper illustrated within this data management assignment is to identify the security technologies to prevent the cyber-attacks. In the present scenario, the world is changing with the speed of internet. Exchanging data and information has become easier. These easier communication systems also help in collaborative tele-diagnosis or tele-surgery in the medical sector. At the same time, preservation of the privacy of these data needs to be secured [5]. The mentioned article proposes an encryption system which is quantum-assisted. This article serves the purpose of the current research paper on data management assignment as it aims to understand the different technologies to secure sensitive medical data. In the diagram mentioned below, it shows the significance of cloud computing among the doctors, authority, pharmacist, physicist, and the patients with their families. The cloud computing technology also helps in providing facilities through wireless machines, such as blood pressure monitor, or glucose measuring meters [4].
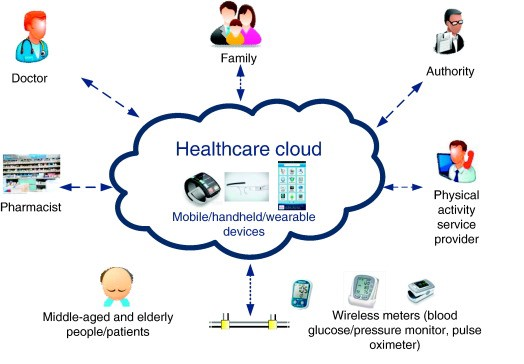
Figure 1: cloud computing in Health care [4]
2.4. Objective 2
In recent era, the rate of cyber-attacks is growing with time. The up rise of the different security technology is helping to secure threatened and sensitive medical data. The mentioned article utilized in this data management assignment discusses on a cryptographic block-chain method which makes it hard to get access of the sensitive and threatened data [7]. The new technologies are impacting in a positive manner on the healthcare system. The proposed approach mentioned in this article of data management assignment is making the process easy to prevent such criminal activities. Sensor is a crucial element in all kinds of applications nowadays. It is even important in the healthcare systems [8]. The medical devices gather enormous data which is called the Big Data. Processing the big data is quite a difficult job and lack of security may lead to massive loss. The mentioned article discusses on the Industrial Internet Things architecture which aims to store the big data with much security and safety.
The current referred article explored in the data management assignment states that a minor loss in creating and updating in medical data security could be fatal to both patients and the medical professionals. It mentions that in Poland, the data are mostly stored manually and are not updated since the past ten years [9]. This has led to utter problems of cyber-attacks. The EU regulation approach is an adequate method of securing the personal and medical documents of the healthcare systems. Big Data is a very essential element in the healthcare systems. It helps to provide with potential for the betterment of patient outcomes, healthcare delivery and the quality of life. It also helps in preventing epidemic and other diseases [4]. It is also helpful in preserving the information. The mentioned article provided within this data management assignment states that no matter how useful it is the facilities of high security in preserving the data should be there. The article discusses on the methods of anonymization and encryption to ensure safety of the healthcare data. The diagram that mentioned below within this data management assignment explains that the significance of IoT in healthcare sector is related to the patient, their health condition, medical care facilities, and interactive session with the doctors and medical staffs [17].
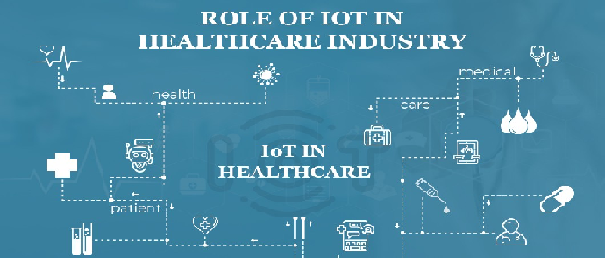
Figure 2: IoT in healthcare
2.5. Objective 3
The MIoT is a very helpful and important tool to improve the safety of the healthcare systems. It enables the facilities of tele-diagnosis as well as tele-surgery and helps the patients to access any kind of medical support from anywhere [10]. Preserving the highly sensitive data has become easier due to the usage of MIoT. The preservation of this data on the cloud is still unresolved. The mentioned article aims to discuss the various security and privacy requirements for those data [21]. The mentioned article discusses within this data management assignment is an efficient centralized secure architecture containing end to end encryption for the healthcare data. It helps to transfer the data to near edge devices and further store it to the cloud. The medical professionals can access these data from the cloud [17]. The access of the data needs security and the article mentions some methods of mobile tracking or other devices tracking to prevent the misuse of these sensitive data.
Herein data management assignment, the data security has become the most crucial element in the healthcare systems. Certain architecture of the efficient centralized data management has been proposed in this article. The proposed architecture helps to store the data and information in the cloud which is accessible by the professionals and yet need more security [17]. The various methods of securing the data such as device tracking and tracking the deployment and connection to existing systems have been discussed in the mentioned article. The significance of securing the healthcare data is becoming more necessary by the time. The privacy issues mentioned in this data management assignment are growing as well [18]. The Cloud Computing of the Big Data is a sustainable and helpful option in this matter. But CC is a comparatively new tool and has many gaps within the system. The current article mentions the gaps and discusses the methods to rectify them. Developing the CC may help in preserving and deciding the medical data more accurately and effectively.
3. Methodology
The current paper on data management assignment focuses on the impact of cloud computing and IoT on the health care data security. Modern heath care industry efficiently using big data for effective health care management. There is a common trend among contemporary health care system across the globe where they are focusing on shifting patient data into online health care management system. There is a major security concern associated with big data management in health care system due to vulnerabilities related to cloud computing and IoT [27]. The focus of the current research paper is to explore the impact of security concerns on health care data management and associated impact on cloud computing and usage of IoT in healthcare [19]. The current research on data management assignment has been continued with primary search where surveys have been taking place in order to achieve primary data to facilitate the current research.
The transcripts from the interactive session from the primary research on data management assignment will be conduct qualitative research to identify the trend associated with modern health care data management security vulnerabilities which are integrated with cloud computing platforms and IoT [26]. Modern health care systems extensively use online data management and computing system which are associated with threats like malware, data theft or data hijack etcetera. Addressing the data vulnerabilities are major challenge for the efficient data management system and patient data security [22]. The current research on data management assignment helps to show direction in order to address challenges and issues with security concern associated with data management system and computing. The outcome enables modern health care organizations to deploy data security measures into their cloud computing methodologies and IoT devices [20].
3.1. What are the research questions based on the data management assignment?
- What is the security parameters associated with medical data management?
- What are the impacts of cloud computing in medical data security?
- What are the impacts of IoT security framework in medical data security management?
3.2. Qualitative /Quantitative method
The research on data management assignment deals with the critical evaluation of cloud computing in terms of IOT implementation in medical security management of data. The qualitative method of research deals with an understanding of human behavior from the perspective of the informant for assuming a negotiated and dynamic reality [32]. The data are collected by the participants through interviews and observational procedures. Whereas, on the other side of the story, the quantitative research on data management assignment is concerned with the invention of facts regarding the social phenomena for assuming a measurable and fixed reality [23]. In this method, the data are collected through comparisons of statistical and numerical inferences. In the qualitative research, data are reported in terms of the informant’s language [28]. But in quantitative research on data management assignment, the data are reported through analytical representation of statistical techniques and methods.
In this research, the qualitative method has been used to collect both the theoretical and practical concepts of the topic. IoT is an emerging field in the IT industry [29]. The applications of IoT have been used in all sectors to extract their effectiveness in a particular industry [30]. In the medical industry, lots of data needs to be handled, and securing them is also a tough task. Implementing applications of IoT in the medical industry helps to secure the data effectively. Collecting data through the qualitative method has a significant effect on analyzing the data for research. The research on data management assignment has been conducted in an authentic manner keeping the ethical considerations in mind. It helps to retrieve data effectively for the research. The research thus will help to provide a sustainable result on real grounds.
3.3. Method used in current research on data management assignment
The research dealing with the critical evaluation of cloud computing in terms of IOT implementation in medical security management of data is mainly concerned with the qualitative approach of methodological analysis [33]. It is focused on the social interactions in terms of a micro-level composition involving day-to-day life structure among the sample population. The qualitative research methods include immersion and observation, interviews, surveys that are open-ended, focus groups, oral histories, and analysis of content in terms of textual and visual materials [25]. The data are reported in terms of the informant’s language and are collected by the participants through interviews and observational procedures.
3.4. Application and Importance of method
The research on data management assignment regarding critical evaluation of cloud computing in terms of IOT implementation in medical security management of data deals with useful identification of relationships among variables [34]. It is designed for revealing the meaningful information in terms of action courses. It deals with the outcomes which are specifically considered to be measurements regarding investigation of various interpretations. The qualitative research methods include immersion and observation, interviews, surveys that are open-ended, focus groups, oral histories, and analysis of content in terms of textual and visual materials. It introduces a descriptive data in interpreting the rigorous methods of systematic revelations in transcribing themes.
The qualitative method has involved relevant sources to retrieve the themes based on the study. The research on evaluating cloud computing for IoT implementation has discussed the themes based on the sources of cloud computing and IoT applications [34]. The themes have provided relevant knowledge to the researchers based on the study. The researchers can thus, draw a fruitful conclusion for the study and provide effective ideas to the medical industry for securing their data. The oral histories from the experts help to obtain the effectiveness of the research on real grounds [24]. Involving participants for the interviews have been done by maintaining all the norms of ethical considerations. It has helped to collect the relevant data for the research and provided authenticity to the study.
3.5. Problem of the method
The research on data management assignment on evaluating of cloud computing in terms of IOT implementation in medical security management of data involves the qualitative approach of methodology. It includes various problems through misunderstanding of investigations in science [31]. Qualitative research methods follow a strict set of protocols which is a very problematic issue. It involves various sorts of biases based on the communicational aspects [35]. Its main obligation involves unambiguousness for clarifying the steps that were followed from the investigation techniques. It fails to identify the research typologies and establish the research objectives. The researcher’s persuasion rises to the extent of advocacies for any particular position.
The method should also involve the quantitative method so that the numeric value for measuring the effectiveness of cloud computing can be evaluated. It will help the researchers to get practical knowledge of the study. As the study involves applications related to the IT industry, thus the data should be retrieved from IT analysts also. The problem of the method is the process of retrieving data is completely depends on secondary sources. No primary research on data management assignment has been used to collect relevant data from participants. Involving participants for the research will help to retrieve practical data on the study.
3.6. Data collection method
The research process related to the primary method requires thorough understanding of the interview sessions with the participants. It will be a qualitative analysis with the answers as the questions are open ended. It is required to understand the practical understanding of the implementation of cloud computing and IoT at the medical sector. It is not a new area to research. However, the recent concern due to the security and safety reasons of the valuable data. The implementation of these advanced technologies is required to make the operation processes in the medical sector, such as patient enrolment process, documentation of health and treatment related information, transaction process and acquiring medical history of regular patients. It will also help the medical sector in acquiring valuable information related to the treatment process of any particular disease. The survey process during the primary research will help the research process in evaluating the current trends and issues regarding the usage of IoT and cloud computing facilities.
The secondary research process based on the data management assignment will be observed with the relevant existing research articles and journals to understand the background and evolution of these technologies in the medical field. The research on data management assignment on evaluating of cloud computing in terms of IOT implementation in medical security management of data includes the secondary data collection in qualitative research procedures. The secondary analysis of data includes various secondary sources of information from several journals, newspapers, books, articles, government censuses and etcetera. It deals with the concept of providing databases that are of high quality for considering essential analysis. It is mainly concerned with capturing past experiences for interpreting various future estimations [36]. It is less useful in marketing research processes for its inaccuracy of data that are gathered from already existing researches on a particular topic. However, the effective analyzation process with the contents from the selected research paper can establish transparent and accurate data for conducting further research process.
Secondary research on data management assignment mainly involves collecting data from relevant journals, articles, books, and etcetera. It gives a piece of authentic information to the research. The journals that have been used in the research are the relevant sources and have an efficient impact on the research. Knowledge has been gathered on the topic through these sources. The sources help the researchers to retrieve authentic data that can improve the quality of the research on data management assignment. Thus, the researchers have researched with the help of relevant sources on IoT. The medical industry has little application of IoT and thus, the research will help to give the knowledge about IoT on medical data. The application of cloud computing and IoT will help to connect the applications of the IT industry with the medical industry. In this way, the medical industry will get an effective change in securing the data regarding various medical components.
4. References
[1] Pirbhulal, S., Samuel, O.W., Wu, W., Sangaiah, A.K. and Li, G., 2019. A joint resource-aware and medical data security framework for wearable healthcare systems. Data management assignment Future Generation Computer Systems, 95, pp.382-391.
[2] del Rey, A.M., Pastora, J.H. and Sánchez, G.R., 2016. 3D medical data security protection. Expert Systems with Applications, 54, pp.379-386.
[3] Singh, B., Saini, B.S., Singh, D. and Pandey, A. eds., 2019. Medical Data Security for Bioengineers. Medical Information Science Reference.
[4] Abouelmehdi, K., Beni-Hssane, A., Khaloufi, H. and Saadi, M., 2017. Big data security and privacy in healthcare: A Review. Procedia Computer Science, 113, pp.73-80.
[5] Praveenkumar, P., Santhiyadevi, R. and Amirtharajan, R., 2019. Medical Data Are Safe: An Encrypted Quantum Approach. In Medical Data Security for Bioengineers (pp. 142-165). IGI Global.
[6] Tiwari, A., Tripathi, R.P. and Bhatia, D., 2019. Advancements in data security and privacy techniques used in IoT-based hospital applications. In Medical Data Security for Bioengineers (pp. 185-207). IGI Global.
[7] Abouelmehdi, K., Beni-Hessane, A. and Khaloufi, H., 2018. Big healthcare data: preserving security and privacy. Journal of Big Data, 5(1), p.1.
[8] Manogaran, G., Thota, C., Lopez, D. and Sundarasekar, R., 2017. Big data security intelligence for healthcare industry 4.0. In Cybersecurity for Industry 4.0 (pp. 103-126). Springer, Cham.
[9] Sus?o, R., Trnka, J. and Drobnik, J., 2017. Current threats to medical data security in family doctors’ practices. Family Medicine & Primary Care Review, (3), pp.313-318.
[10] Sun, W., Cai, Z., Li, Y., Liu, F., Fang, S. and Wang, G., 2018. Security and privacy in the medical internet of things: a review. Security and Communication Networks, 2018.
[11] Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H. and Zhao, W., 2017. A survey on internet of things: Architecture, enabling technologies, security and privacy, and applications. IEEE Internet of Things
[12] Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security problem. arXiv preprint arXiv:1609.01107.
[13] Singh, S., Jeong, Y.S. and Park, J.H., 2016. A survey on cloud computing security: Issues, threats, and solutions. Data management assignment Journal of Network and Computer Applications, 75, pp.200-222.
[14] Khan, S., Parkinson, S. and Qin, Y., 2017. Fog computing security: a review of current applications and security solutions. Journal of Cloud Computing, 6(1), p.19.
[15] Pancholi, V.R. and Patel, B.P., 2016. Enhancement of cloud computing security with secure data storage using AES. International Journal for Innovative Research in Science and Technology, 2(9), pp.18-21.
[16] Radwan, T., Azer, M.A. and Abdelbaki, N., 2017. Cloud computing security: challenges and future trends. International Journal of Computer Applications in Technology, 55(2), pp.158-172.
[17] Thota, C., Sundarasekar, R., Manogaran, G., Varatharajan, R. and Priyan, M.K., 2018. Centralized fog computing security platform for IoT and cloud in healthcare system. In Fog Computing: Breakthroughs in Research and Practice (pp. 365-378). IGI global.
[18] Stergiou, C., Psannis, K.E., Kim, B.G. and Gupta, B., 2018. Secure integration of IoT and cloud computing. Future Generation Computer Systems, 78, pp.964-975.
[19] Zhou, J., Cao, Z., Dong, X. and Vasilakos, A.V., 2017. Security and privacy for cloud-based IoT: Challenges. IEEE Communications Magazine, 55(1), pp.26-33.
[20]Stergiou, C., Psannis, K.E., Gupta, B.B. and Ishibashi, Y., 2018. Security, privacy & efficiency of sustainable cloud computing for big data & IoT. Sustainable Computing: Informatics and Systems, 19, pp.174-184. Journal, 4(5), pp.1125-1142.
[21] Sharma, S., Chen, K. and Sheth, A., 2018. Toward practical privacy-preserving analytics for IoT and cloud-based healthcare systems. IEEE Internet Computing, 22(2), pp.42-51.
[22] Mahmud, R., Koch, F.L. and Buyya, R., 2018, January. Cloud-fog interoperability in IoT-enabled healthcare solutions. In Proceedings of the 19th international conference on distributed computing and networking (pp. 1-10).
[23] Babu, R. and Jayashree, K., 2016. Prominence of IoT and Cloud in health care. International data management assignment Journal of Advanced Research in Computer Engineering & Technology (IJARCET), 5(2).
[24] Mutlag, A.A., Ghani, M.K.A., Arunkumar, N.A., Mohammed, M.A. and Mohd, O., 2019. Enabling technologies for fog computing in healthcare IoT systems. Future Generation Computer Systems, 90, pp.62-78.
[25] Iyengar, A., Kundu, A. and Pallis, G., 2018. Healthcare informatics and privacy. IEEE Internet Computing, 22(2), pp.29-31.
[26] Ida, I.B., Jemai, A. and Loukil, A., 2016, December. A survey on security of IoT in the context of eHealth and clouds. In 2016 11th International Design & Test Symposium (IDT) (pp. 25-30). IEEE.
[27] Farahani, B., Firouzi, F. and Chakrabarty, K., 2020. Healthcare iot. In Intelligent Internet of Things (pp. 515-545). Springer, Cham.
[28] Ahmed, A., Latif, R., Latif, S., Abbas, H. and Khan, F.A., 2018. Malicious insiders attack in IoT based multi-cloud e-healthcare environment: a systematic literature review. Multimedia Tools and Applications, 77(17), pp.21947-21965.
[29] Neagu, G., Preda, ?., Stanciu, A. and Florian, V., 2017, June. A Cloud-IoT based sensing service for health monitoring. In 2017 E-Health and Bioengineering Conference (EHB) (pp. 53-56). IEEE.
[30] Kumar, P. and Silambarasan, K., 2019. Enhancing the Performance of Healthcare Service in IoT and Cloud Using Optimized Techniques. IETE Journal of Research, pp.1-10.
[31] Chavan, P., More, P., Thorat, N., Yewale, S. and Dhade, P., 2016. ECG-Remote patient monitoring using cloud computing. Imperial Journal of Interdisciplinary Research, 2(2), pp.368-372.
[32] Brennen, B. S., 2017. Qualitative research methods for media studies. s.l.:Taylor & Francis. [33] Hammarberg, K., Kirkman, M. & de Lacey, S., 2016. Qualitative research methods: when to use them and how to judge them. Human reproduction, 31(3), pp. 498-501.
[34] Hennink, M., Hutter, I. & Bailey, A., 2020. Qualitative research methods. s.l.:SAGE Publications Limited.
[35] Lune, H. & Berg, B. L., 2016. Qualitative research methods for the social sciences. s.l.:Pearson Higher Ed.
[36] Tracy, S. J., 2019. Qualitative research methods: Collecting evidence, crafting analysis, communicating impact. s.l.: data management assignment John Wiley & Sons.












