Cyber Security Assignment: Function & Structure Of SHA-1
Question
Task:
Write a scientific report on cyber security assignment on the Content Protection Technologies “SHA-1”.
Answer
Abstract
According to the research on cyber security assignment, it is stated that the cryptographic operation is a hash function that can convert input message into variable length to get a fixed output known as the message digest or message hash. Mostly, the hash function is found in data integrity mechanisms, authentication schemes, digital signatures, and the random number of generations. To get an initial message, the hash value is computed through a modern cryptographic hash function. While there is a collision in finding two different messages, the property of the hash function is much difficult due to which the function is widely used in security protocols that are popular namely the Internet Protocol Security or Transport Layer Security.
1. Introduction
In 1995, the SHA-1 function is widely used by NIST standard cryptographic hash function. It is deprecated officially by NIST in the year 2011. There was a weakness in the fundamental security that demonstrated some theoretical attacks and analyses. Apart from such deprecation, in 2017, SHA-1 was used widely for document and signature certificates of TLS. Along with more software of GIT versioning system that has a purpose for back up and integrity. This report describes the function of SHA-1 and its structure with certain advantages and limitations.
2. Description
The SHA-1 is a cryptographic hash function that stands for Secure Hash Algorithm-1. For the algorithm, it is the first iteration. When there is an input with a hash value it will produce 160-bits for 20-byte (Leurent and Peyrin, 2019). As it is known that SHA-1 is also named as a message digest, it renders the hexadecimal number whose length would be around 40 digits. It is a very important design introduced by the National Security Agency of the United State. Unfortunately, since 2005, SHA-1 was insecure for large industries. By the time of 2017, no browsers like Google, Mozilla, Microsoft accepted SHA-1 SSL certificates.
Even in the Java language, the MessageDigest Class will be used for calculating the hash value of cryptographic that also within the java.security package. While SHA-1 is generated with other algorithms with a static method call as getInstance() method. In the final selection of the algorithm, the calculation is done for the message digest value to get the result as a byte array (Al-Odat, Ali and Khan, 2018). This byte array will further get converted by using BigIntegerand get signum representation. Then further it gets converted to hexadecimal format and the Message Digest as expected.
3. SHA-1 Structure
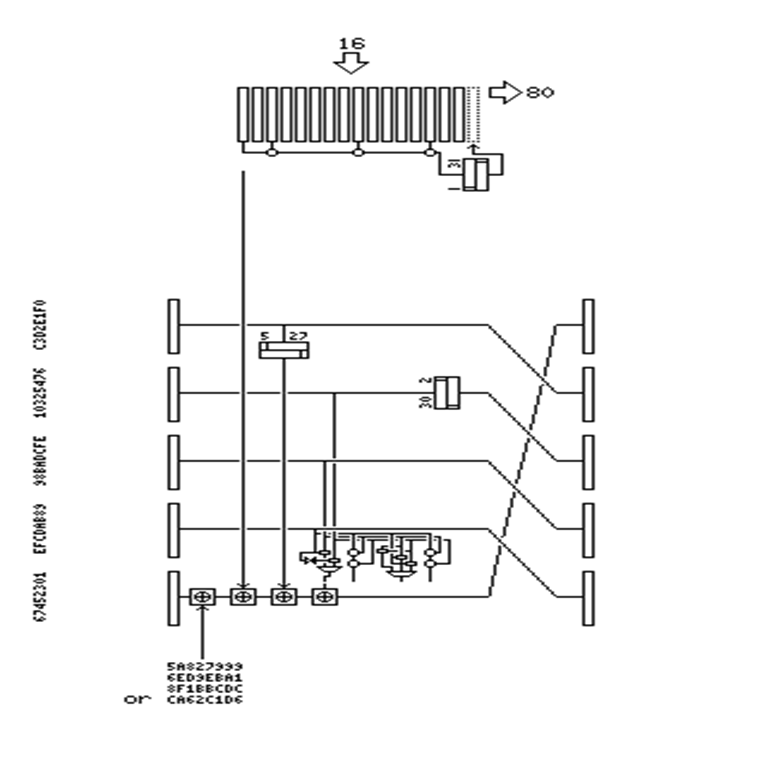
The SHA-1 converts messages to a unique representation whose length is multiple of 512 bits where the information is not a loss for the original length. Further, multiple zeros are added to reach the target (Chaves et al., 2016). To reach the length of 64 bits with a multiple of 512 bits. Block 512 expands each time when it is used with 32-bit subkeys. The initial 16 subkeys are blocks. Other subkeys are N-3, N-8, N-14, and N-16 where N is exclusive which is subjected to left shift by one place. With hexadecimal, the value starts with a 160-bit block namely EFCDB89 C3D2E1F0 67452301 98BADCFE 10325476 with the process input of block 512-bit whose message is modified (Makkad and Sahu, 2016). The beginning of the value enciphers with the use of 80 subkeys that has the block with the current message.
The SHA enciphers a 160-bit block having 80 times 32-bit subkeys with 80 rounds (Júnior, Torquato, and Fernandes, 2018). The series is similar to Feistel rounds having two halves of the block divided with a piece of five. Of the five pieces, four are calculated as F-function with XOR function having three pieces along with fourth left shift and having one piece that is XORed to the current round's constant and subkeys. With 20 rounds each group has the same constant. With left shift circulating the blocks that rotate 160-bit blocks. In every 20 rounds, there is a change in the constant and the F-function (Suhaili and Watanabe, 2016). There is a block of 160-bit, that has five pieces to encrypt a, b, c, d, and e, which rounds the SHA “block cipher”
- While adding the current constant, change is for a in hexadecimal:
- For rounds 1 to 20: 5A827999
- For rounds 21 to 40: 6ED9EBA1
- For rounds 41 to 60: 8F1BBCDC
- For rounds 41 to 60: 8F1BBCDC
- For rounds 61 to 80: CA62C1D6
- While adding an appropriate subkey, change is for a to have a round.
- While adding e in the change, the 5 places are circular left-shift.
- While adding a change b, c, and d to the main F-function, which is calculated in the following way:
- For round 1 to 20, there will be (b AND c) OR (NOT b) AND d).
- For round 21 to 40, there will be b XOR c XOR d.
- For round 41 to 60, there will be (b AND c) OR (b AND d) OR (c AND d).
- For round 61 to 80, there will be b XOR c XOR d.
- While d will be changed, there would be a circular right shift having 2 positions. Otherwise, to have consistency there would be a circular left shift to 30 places.
- After all this, the pieces will be a swap, where every piece moves to the next one that is earlier apart from the value that is moved to e.
The illustration is given in the diagram below:
Figure: Secure Hash Algorithm (Long, 2019)
4. Advantages
The advantages of SHA-1 arediscussed below:
- SHA-1 has a widespread use while entering a password into the website's login page. It actually works in the background (Slimane, Bouallegue, and Machhout, 2017). The benefits that the website get is, it uses a method that verifies securely and get an authentic password. It is infeasible and it work computationally with corresponding message digest.
- The second benefit with the SHA-1 cryptographic hash function is that, the password gets a turn to a checksum which gets stored on the website with the current password (Michailet al., 2016). When both get match, the access is granted and if not, then the password is incorrect.
- The SHA-1 function is also used for verification of the file. There will be a file to which SHA-1 checksum is provided by the websites to the downloaded page (Stevens et al., 2017). This allows to check the checksum while the file is downloaded which is thus intended to download.
- SHA-1 can ensure that there will be no change in the data. No users can easily break SHA-1 even though it is used for a consistency check. The SHA-1 cryptographer manages the repositories of the code, browser security and detects the duplicate files that are in the storage. Large data get compress to a small message digest.
- The SHA-1 function uses the alphanumeric string to represent the cryptography of a piece of data or a file. It means it can serve as a digital signature and is unique and non-reversible. The benefit here is that sometimes the user might want to download the same version from another website. In that case, the file can be compared with the genuine checksum from the downloaded page of the developer. If it is found different than there could be malware hidden in the file.
5. Limitations
There are certain limitations in the SHA-1 hash function and are discussed below:
- The collision attack for the SHA-1 hash function is limited in the real-world. It was found the SHA-1 hash function produces two different files having the same SHA-1 signature, which means the function is cryptographically broken (Mezher and Ibrahim, 2019). It generates a digital fingerprint that is forged and cannot be trusted. Hence, SHA-1 is vulnerable to theoretical attack due to which it is no longer being used by any browsers.
- There is a weakness in SHA-1 due to which many web browsers are no more accepting the SSL certificate that is signed. SHA-1 functions are secure however creating a document to match the hash function is calculated from the given function.
- When anyone creates two different files using the same hash function, there is a possibility to sign one digitally and later that get replace through malicious one which the electronic audit unable to identify.
- There is a hash derived from all the blocks. SHA-1 is done in 80 rounds where the first attack breaks in 80 rounds (Stevens, Karpman, and Peyrin, 2016). In that case the attack has a stronger collision.
- The limitation to the SHA-1 has a problem with password hashing. Where it is allowed to have a brute-force attack where the password space is iterated. Since SHA-1 is very fast, it helps in hashing millions in a second.
- On GPUs, it is parallelizable, where if any copy is acquired of the password, then it can be easily crack through the database within a short period of time.
- For password hashing, SHA-1 requires limited computing power which helps in improving the application performance.
- SHA-1 is mostly used for internal purposes only. There is an impact in optimizing the code. The attack is sensitive based on the quality of implementation. Thus making it is easy to implement the SHA-1 function.
6. Conclusion
Thus, from the report, it can be concluded that SHA-1 is the most popular one. The message digest that SHA-1 produces has a fixed-length output. It is then inputted to a digital signature algorithm through which a signature is generated for the message. Unfortunately, the SHA-1 hash function to some extend is found to be unsafe for most of the browsers for which they have banned the services. However, in many of the websites, it is still used internally as a secure service and mainly for internal purposes only. As there are some advantages to the SHA-1 function and also some limitations.
References
Al-Odat, Z., Ali, M., and Khan, S.U., 2018, December. Mitigation and improving sha-1 standard using collision detection approach. In 2018 International Conference on Frontiers of Information Technology (FIT) (pp. 333-338). IEEE.
Chaves, R., Sousa, L., Sklavos, N., Fournaris, A.P., Kalogeridou, G., Kitsos, P., and Sheikh, F., 2016. Secure hashing: SHA-1, SHA-2, and SHA-3. Circuits and Systems for Security and Privacy; Taylor & Francis Group: Abingdon, UK, pp.105-132.
Júnior, C.E., Torquato, M.F. and Fernandes, M.A., 2018. Application-Specific System Processor for the SHA-1 Hash Algorithm. arXiv preprint arXiv:1901.04989.
Leurent, G. and Peyrin, T., 2019, May. From collisions to chosen-prefix collisions application to full SHA-1. In Annual International Conference on the Theory and Applications of Cryptographic Techniques (pp. 527-555). Springer, Cham.
Long, S., 2019, October. A Comparative Analysis of the Application of Hashing Encryption Algorithms for MD5, SHA-1, and SHA-512. Cyber security assignment In Journal of Physics: Conference Series (Vol. 1314, No. 1, p. 012210). IOP Publishing.
Makkad, R.K. and Sahu, A.K., 2016, May. Novel design of fast and compact SHA-1 algorithm for security applications. In 2016 IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT) (pp. 921-925). IEEE.
Mezher, M. and Ibrahim, A., 2019, February. Introducing practical sha-1 collisions to the classroom. In Proceedings of the 50th ACM Technical Symposium on Computer Science Education (pp. 879-884).
Michail, H.E., Athanasiou, G.S., Theodoridis, G., Gregoriades, A. and Goutis, C.E., 2016. Design and implementation of totally-self checking SHA-1 and SHA-256 hash functions’ architectures. Microprocessors and Microsystems, 45, pp.227-240.
Slimane, N.B., Bouallegue, K. and Machhout, M., 2017, January. A novel image encryption scheme using chaos, hyper-chaos systems and the secure Hash algorithm SHA-1. In 2017 International Conference on Control, Automation and Diagnosis (ICCAD) (pp. 141-145). IEEE.
Stevens, M., Bursztein, E., Karpman, P., Albertini, A. and Markov, Y., 2017, August. The first collision for full SHA-1. In Annual International Cryptology Conference (pp. 570-596). Springer, Cham.
Stevens, M., Karpman, P. and Peyrin, T., 2016, May. Freestart collision for full SHA-1. In Annual International Conference on the Theory and Applications of Cryptographic Techniques (pp. 459-483). Springer, Berlin, Heidelberg.
Suhaili, S. and Watanabe, T., 2016. High throughput evaluation of SHA-1 implementation using unfolding transformation. ARPN Journal of Engineering and Applied Sciences, 11(5), pp.3350-3355.












