Computer Security Assignment: Cyber Threats & Encryption
Question
Task:
Your computer security assignment must address the following points:
1. Based on your personal experiences or those of someone you know (you may have to interview other students or a friend), write a paragraph regarding a computer attack that occurred.
- When did it happen and what was the attack?
- What type of damage did it inflict?
- List the reason or reasons you think that the attack was successful.
- How was the computer fixed after the attack?
- What could have prevented it?
1. Describe onion router and its purposes. Download onion router and using wireshark capture packets coming out of onion router when you visit a website. What path are the packets taking to go out of the network?
2. Download “smb3-aes-128-ccm.pcap” from the following link https://wiki.wireshark.org/SampleCaptures#SMB3_encryption. Analyse the pcap file using wireshark and list down all information you can read from the packets.
3. Download PGP (freeware or paid) and try to encrypt an email using someone's public key. Describe other functions that you can do with PGP
4. Download any steganography software and demonstrate hiding a 500kB document in the software–
5. Password cracking : Create a digest on a password and then crack it with an online cracking website to demonstrate the speed of cracking passwords. You can create 10 different passwords and see how those passwords could be cracked.
Note : The first step is to use a hash algorithm to create a password digest. Use your web browser to go towww.fileformat.info/tool/hash.htm. You can use https://crackstation.net/ to check the password cracking time.
6. QR code has different vulnerabilities and it could easily exploit. With the help of www.qrstuff.com explain how an attacker could use a QR code to direct a victim to a malicious website?
Answer
Computer Attack – Malware Attack
My computer was infected with a malware/spyware after I downloaded an unsolicited email and executed the attachment. It installed malicious addons and malwares in my PC. Every time, I would try to load a site, it would redirect me to some random site.
Could’ve simply been prevented by:
a) Not downloading the attachment from the unsolicited email (Bahtiyar, 2016). This would have made sure that the malware was not downloaded on my system.
b) Executing the attachment in a Sandbox environment: such as a Virtual Machine. The malware would have been identified and the alerts would have been issued to maintain the security.
c) Should have kept my Antivirus as well as my Browser updated to the latest versions. This would have led to the effective avoidance of the issue.
Onion Router and its Purpose
Onion Router, also referred as the Tor Browser is the software as well as the network that makes sure that the anonymity of the user is maintained on the Internet. The onion routing programs are developed on the basis of the extensive research and development of the anonymous communication protocols(Pei and Oida, 2020). The primary focus has been kept on the low-latency network systems and channels that can avoid the network security issues, such as eavesdropping and other forms of man in the middle attacks.
The primary purpose is to maintain and promote the security of the network and the information sets. The logical and physical location of the service is kept hidden that leads to the resistance from the denial of service, distributed denial of service, and other network security attacks(Dhankani et al., 2015).
I downloaded the default Tor Browser for Windows from the Torproject.org and also installed and configured Wireshark on my computer. Thereafter, I opened the Torbrowser and visited Google.com and captured and filtered the following traffic as displayed below in the screenshot.
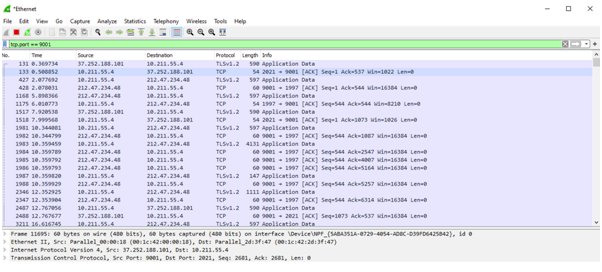
Since there is a lot of traffic coming back and forth on my computer, I had to filter the port on Wireshark so as to focus only on the WireShark. In order to identify exactly, I also ran regular browser to verify, if it indeed the traffic was from Onion Router. So, the traffic was coming through and from via 9001 port. As can be seen in the screenshot the handshake exchanges happen through TLS1.2 protocol which is an encrypted protocol. This ensures that the data being exchanged from the client is encrypted end-to-end.
SMB Packet Capture Analysis
SMB or Server Message Block is a Microsoft Windows’ file sharing protocol. SMB2 is the latest version of the protocol for Windows 10. From the WireShark Capture file, I was able to read the following information:
- There’s a Handshake Protocol going on in the Wireshark Capture file.
- This is between a Client and a Server(Bhatt and Shabaz, 2019).
- The Client’s IP address is 10.160.64.139 and the Server’s IP address is 10.160.65.202.
- The exchange is happening over SMB2 Protocol.
- In the first there’s a request to identify the dialect that client could work with.
- In the subsequent message, there’s a session being setup to authenticate the user so that they can login in.
- There’s an error at first, which indicates authentication failure.
- Finally, there’s in the Tree connect request, the client successfully connects with the Share. First, a WS2016 directory is accessed and subsequently another directory is accessed. The exchange remains encrypted over SMB3.
PGP Public Key Encryption
For the free PGP Encryption, I am using the MailvelopeAddon for Chrome which can be used to directly encrypt Gmail, GMX, Yahoo and Outlook emails. I installed, the Mailvelopeaddon from the official chrome repository and configured it for my browser(Kanwal and Singh, 2015).
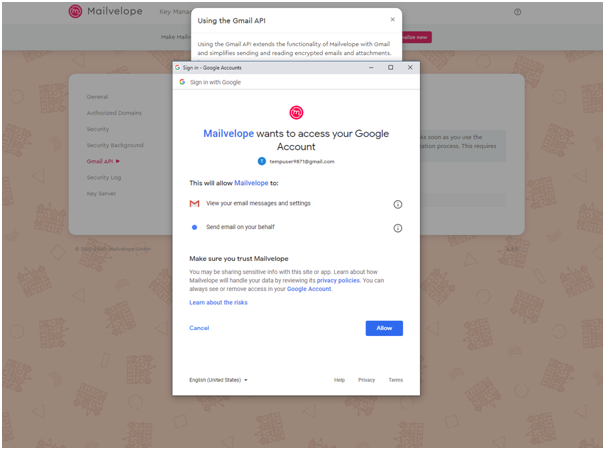
Thereafter, I headed to http://pitt.edu/~poole/PGP.htm and used one of the public keys available.
I imported the key in Mailvelope which can be seen below and configured it in the Mailvelope application(Braun and Oostveen, 2019).
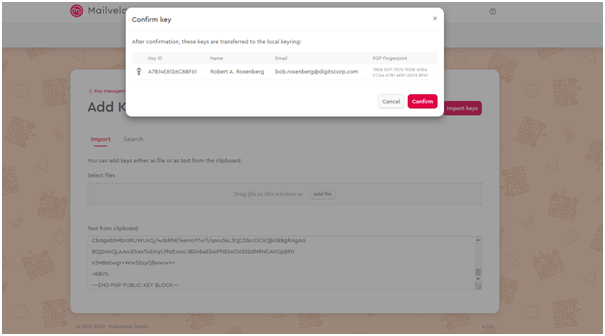
It can be seen that the Key has been imported.
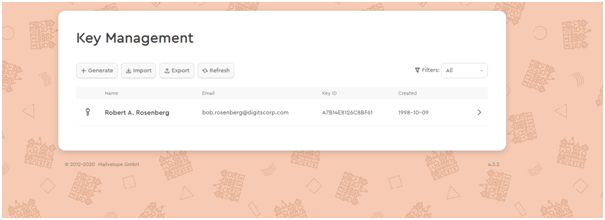
Upon clicking on the key, it reveals further details. It can be seen that the Key which was issued in 1998 is still valid and active.
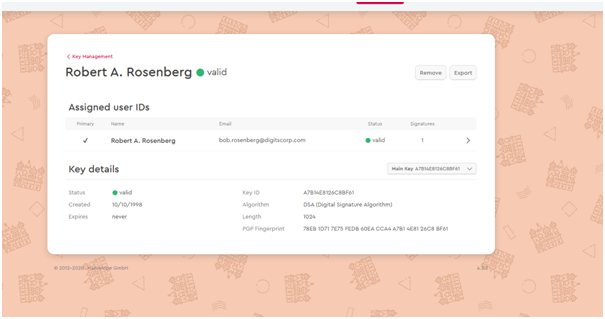
Thereafter, I can mail Mr. Rosenberg at his mail ID bob.rosenberg@digitscorp.com using his public key to send him an encrypted email which can be unlocked using the key.
Steganography
I used OpenStego to hide the Word document of 500 KBs in a BMP image file(Kolakalur, Kagalidis and Vuksanovic, 2016). The configuration for the same was as follows:
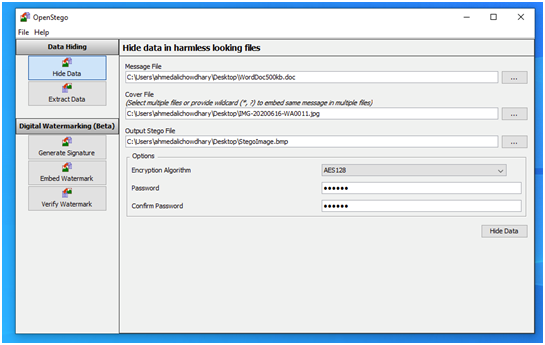
The BMP image file was as follows:

The Word document was embedded in the Bitmap file as shown below.

The resulting image showed no visual differences or degradation. However, the size of the file had increased from 70 KB to 3.5 MB (Shahi, 2020).
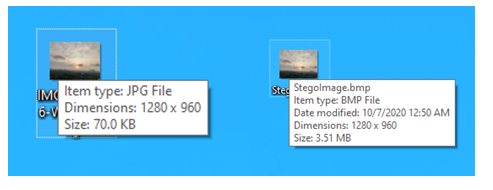
Password Cracking
The following passwords, were Hashed in MD5 using the Fileformat.info/tool/hash.htm tool.
|
Passwords |
MD5 Hash of the Password |
|
123456 |
e10adc3949ba59abbe56e057f20f883e |
|
password |
5f4dcc3b5aa765d61d8327deb882cf99 |
|
difficultpassword |
c6b4b58e9ee926ae1797e3bbbe023e99 |
|
password2020 |
b16f6d16492a220641286257b01b6f4a |
|
p@ssword |
90f2c9c53f66540e67349e0ab83d8cd0 |
|
p@ssw0rd |
0f359740bd1cda994f8b55330c86d845 |
|
p@ssw0rd2020 |
8b746e98bd40292b7218ed4c5b20374f |
|
P@ssW0rd |
5ca33d221fd09f16c1ecba9c1aadc3eb |
|
@P@ssW0rd2020 |
ed50250158e478d88bf8bc62ad971238 |
|
@P@ssW0rd2020#! |
5d19227bbf3de9c7f931098faf3745ac |
|
e10adc3949ba59abbe56e057f20f883e |
md5 |
123456 |
|
5f4dcc3b5aa765d61d8327deb882cf99 |
md5 |
password |
|
c6b4b58e9ee926ae1797e3bbbe023e99 |
Unknown |
Not found. |
|
b16f6d16492a220641286257b01b6f4a |
md5 |
password2020 |
|
90f2c9c53f66540e67349e0ab83d8cd0 |
md5 |
p@ssword |
|
0f359740bd1cda994f8b55330c86d845 |
md5 |
p@ssw0rd |
|
8b746e98bd40292b7218ed4c5b20374f |
Unknown |
Not found. |
|
5ca33d221fd09f16c1ecba9c1aadc3eb |
md5 |
P@ssW0rd |
|
ed50250158e478d88bf8bc62ad971238 |
Unknown |
Not found. |
|
5d19227bbf3de9c7f931098faf3745ac |
Unknown |
Not found. |
While, some of the passwords were cracked instantaneously, some passwords could not simply be cracked. It was interesting to note that the phrase ‘difficultpassword’ could not be cracked even though it contained no special characters or symbols.
QR Codes and associated Vulnerabilities
QR Codes or the Quick Response codes are the barcodes that are included in the two-dimensional matrix. The use of these QR codes is done for the encoding of the information.The website www.qrstuff.com can be used to allow the users to generate various QR codes for numerous different applications. Also, the use of the website can be done for QR scanners.
There are several security issues and attacks that can be executed using the QR codes developed using the website. For example, the site allows the QR code to be developed to access the email message. The inclusion of the malicious codes can be done on the developed QR code which can redirect the user to a malicious site and a malware may be downloaded on the system being used by the user(Krombholz et al., 2014). Similarly, for the payment gateways, the QR code developed using the site can be used to access the information being entered by the user in an unauthorized manner. The payment information is extremely critical and sensitive. If the malicious entities succeed in gaining access to the information then the violation of the security and privacy will be done.
The use of the site can also be done to generate the QR codes for advertising agencies or marketing agencies. The QR codes that are generated may access and capture the location of the user by accessing the information from the device being used. This can lead to the major security gaps as the location details can be misused to carry out additional security attacks. ?
References
Bahtiyar, S. (2016).Anatomy of targeted attacks with smart malware.Security and Communication Networks, 9(18), pp.6215–6226.
Bhatt, M.W. and Shabaz, M. (2019).An Approach to Block Negative Posts on Social Media at Server Side.International Journal of Trend in Scientific Research and Development, Volume-3(Issue-3), pp.729–731.
Braun, S. and Oostveen, A.-M.(2019). Encryption for the masses?An analysis of PGP key usage.Mediatization Studies, 2, p.69.
Dhankani, M., Dhameja, A., Darda, S. and Bohra, D. (2015). Anonymous Communication System based on Onion Routing. International Journal of Computer Applications, 121(23), pp.12–15.
Kanwal, S. and Singh, P. (2015).Security Enhancement of 4G LTE system using PGP and Iterative RSA technique.International Journal Of Engineering And Computer Science.
Kolakalur, A., Kagalidis, I. and Vuksanovic, B. (2016). Wavelet Based Color Video Steganography. International Journal of Engineering and Technology, 8(3), pp.165–169.
Krombholz, K., Frühwirt, P., Kieseberg, P., Kapsalis, I., Huber, M. and Weippl, E. (2014). QR Code Security: A Survey of Attacks and Challenges for Usable Security. Lecture Notes in Computer Science, [online] pp.79–90. Available at: https://link.springer.com/chapter/10.1007/978-3-319-07620-1_8 [Accessed 27 Apr. 2019].
Pei, Y. and Oida, K. (2020). Tracing Website Attackers by Analyzing Onion Routers’ Log Files. IEEE Access, 8, pp.133190–133203.
Shahi (2020).Reversible Steganography for RGB Images Using Image Interpolation.Journal of Advanced Research in Dynamical and Control Systems, 12(3), pp.41–49.












