Accounting Assignment: Strategic Information System in Business Environment
Question
Task: You are supposed to prepare a report on accounting assignment answering the following questions:
Question 1: ABC Limited is a manufacturing firm with a workforce of more than 100 employees. Mr Peter has recently joined the firm as the account payable clerk. Miss Emma is the accounting department head, and she is concerned about the cash disbursement system. Therefore, she has asked Mr Peter to analyse the firm's cash disbursement system and identify the internal control weaknesses from the system. Following is the description of the cash disbursement system. In the temporary file, the account payable clerk receives the supplier's invoice and reconciles it with the purchase order. The accounts payable clerk records the purchase in the purchases journal from the clerk's computer terminal and records the liability by adding a record to accounts payable subsidiary ledger. The clerk then updates the inventory control and accounts payable control accounts in the general ledger. The purchases order and invoice are later filed in the department.
Each day, the clerk visually searches the accounts payable subsidiary ledger from the computer terminal for invoices that are due to be paid. The clerk prepares the cheque and records it in the digital cheque register. The negotiable portion of the cheque is mailed to the supplier, and a cheque copy is filed. The clerk then closes the liability in the accounts payable subsidiary ledger and updates the accounts payable control and cash accounts in the general ledger.
Required: Analyse the internal control weakness in the system.
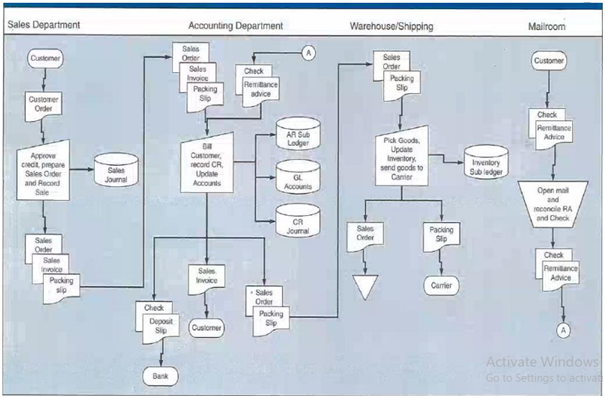
Question 2: XYZ Limited is a clothing wholesaler that sells the name-brand clothing to department stores and boutique dress shops. Figure describes the credit sales procedures of XYZ Limited. In particular, the Figure describes different business activities of four departments, including (1) Sales Department, (2) Accounting Department, (3) Warehouse/Shipping, and (4) Mailroom. Further, these activities are elaborated below.
The sales department received the customer orders by fax and email. You should be aware that these sales orders are usually unstandardized sales order. The sales clerk, who works on commission, performs the following tasks:
- approves the credit sales,
- calculates commission and discounts, and
- records the sales in the sales journal from the PC in the sales department.
After entering these records, the sales clerk then prepares three documents, including (1) a sales order, (2) a customer invoice, and (3) a packing slip. These documents are forwarded to the department of accounting for further processing.
The accounting clerk received these documents and updates the account receivable subsidiary ledger. After updating this subsidiary ledger, the accounting clerk forwards the invoice to the customer. According to the prevailing standards, the accounting clerk forwards the sales order and packing slip to the warehouse/shipping department. Based on this given information, the warehouse/shipping clerk arranges the inventory and sends the inventory along with the packing slip to the carrier for shipment to the customer. Finally, the clerk updates the inventory subsidiary ledger and files the sales order in the department.
Cash receipts from customers go to the mailroom, which has one supervisor overseeing 32 employees performing similar tasks:
- a clerk opens the envelope containing the customer check and remittance advice,
- inspects the check for completeness,
- reconciles it with the remittance advice, and
- sends the remittance advice and check to the accounting department.
The accounting department clerk reviews the remittance advice and the checks, updates the AR subsidiary ledger, and records the cash receipts journal's cash receipt. At the end of the day, the clerk updates the AR control, cash, and sales accounts in the general ledger to reflect the ' 'day's sales and cash receipts.
Required:
a) Describe the uncontrolled risk associated with this system as it is currently designed.
b) For each risk, describe the specific internal control weakness (s) in the system that causes or contributes to the risk.
Question 3:
a) Explain the importance of an active board of 'directors' audit committee to an organisation.
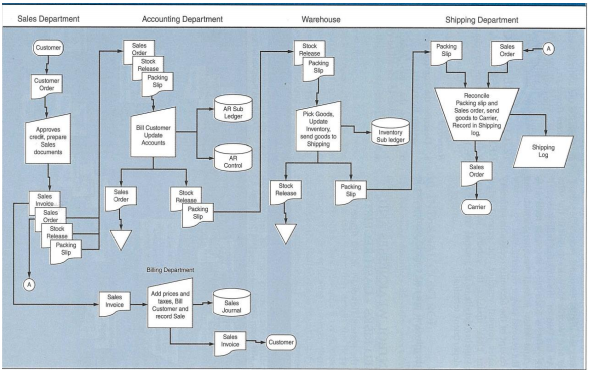
b) The given system flowchart elaborates the business activities involved in different departments, including
(1) Sales Department, (2) Accounting Department, (3) Warehouse, (4) Shipping Department, and (5) Billing Department. The bottom part of this Figure indicates that the Sales Department sends the sales invoice to the Billing Department. Here, it is assumed that this sales invoice only contains non-financial information. For instance, the customer and quantity details. We have discussed the control weakness and the risk associated with these control weaknesses during the Week 4 interactive tutorials. Based on these control weaknesses and the associated risk, what types of frauds are possible in this business environment.
Question 4: After finishing your accounting degree, you joined an accounting firm. This is a medium-size accounting firm with a reasonable range of clients. You are in an engagement meeting with one of your clients, and your client's management raises some concerns. In particular, the management is concerned that the audit tests that you perform will disrupt operations. Your client has recently implemented a data warehouse. The management suggests that you draw the data for analytical reviews and substantive testing from the data warehouse instead of the operational database. Further, the management points out that operational data are copied weekly into the data warehouse, and all data you need are contained there. Required: Based on the given scenario, outline your response to the management's proposal and mention any concerns you might have.
Question 5:
Part (a).
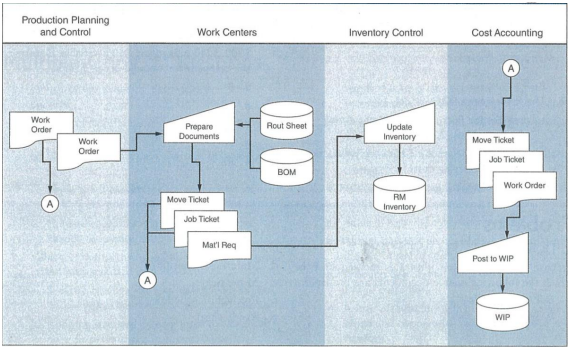
The flowchart on Page No 7 illustrates the business activities of four departments, including (1) Production Planning and Control, (2) Work Centres, (3) Inventory Control, and (4) Cost Accounting. Examine these activities and determine any control threats. In particular, discuss the control problems, the possible dangers, and any corrective procedures you would recommend.
Part (b).
There is an ongoing debate on the elimination of receiving functions. One strand of accountants argues that the receiving department should be eliminated. Conversely, another strand of accountants is in favour of receiving department. Discuss the objective of eliminating the receiving function. Also, discuss the accounting and audit problems need to be resolved.
Question 6:
After finishing Bachelor of Commerce, Miss Emma completed her Master of Computer Sciences (MCS) and started her career as a network engineer in XYZ Limited, Melbourne. She worked for six months in XYZ Limited. Unfortunately, she was fired from the firm last year. Due to the competitive market conditions, she could not find any position as a network engineer.
In 2018, she moved to Brisbane in search of a job. She was desperately working for the job when one of her roommates informed her about a vacant position for the post of account payable clerk in the ABC Limited. Miss Emma was successful in her interview, and she joined the ABC Limited as an account payable clerk. However, she did not disclose her technology background. Early on, Miss Emma established a reputation as a hard-working, enthusiastic, and reliable employee. She often works late and is dedicated to doing an excellent job. Her late-night presence in the company became a common occurrence that was at first appreciated by her boss, and then virtually went unnoticed. Overall, Miss Emma is considered the most hard-working employee of the company.
While working late, Miss Emma used her computer skills to install a sniffer program on the intranet to capture employee IDs and passwords. This information was beneficial for Miss Emma since she could play many roles and establish herself as a vendor, receiving clerk, cash disbursement clerk, and general ledger clerk. With this authority and her legitimate role of AP clerk, Miss Emma implemented a vendor fraud scheme, which she has been perpetrating for over a year for $150,000 to ABC Limited.
Required: Describe the controls that could have prevented Miss Emma from perpetrating this fraud.
Answer
First Question:
Analysing the Internal Control Weakness in the ABC Limited Cash Disbursement System:
Internal Control weakness is defined as the failure to implement the AIS system and failure in maintaining the effectiveness of the internal controls within the organisation. Internal control is implemented by the management of the organisation for assuring that company assets are safeguarded (Cheng et al., 2018). The accounting records are recorded with sufficient details that promote the operational efficiency of the organisation.
According to the given case study of ABC Limited, the followings are the main internal control weaknesses in the cash disbursement system of the firm:
In the AIS, it is important to maintain the policy of the segregation of duties. The segregation of duties defines that more than one employee should not have the responsibility of more than one accounting function (Dewi et al., 2019). It means more than one person cannot proceed with authorisation activity (approving transaction and making a decision), Recording activity (maintaining the ledger, files and journal, preparing the source documents, preparing the performance reports and preparing the reconciliation report) and custody activity (handling the business cash, receiving the incoming clients’ checks, maintaining the storeroom inventory and writing checks) together (Lai et al., 2017). It defines that one person should be responsible for performing the separate parts of any account-related task (Saedi and Dastgir, 2017). According to the case study, the account payable clerk receives the invoice of the suppliers that is part of the authorising of the documents (Jacoby et al., 2018). The clerk is also responsible for making the reconciliation paper of the purchase order and also recording the records of the purchase in the journals of the purchases. Moreover, the account payable clerk is responsible for recording the liability in the account payable subsidiary ledger. These activities are the individual part of the recording activity, so one account payable clerk does not have the authority to maintain the two parts of the recording activity (Donelson et al., 2017). The clerk is also responsible for updating the inventory control part and account payable control part in the AIS’s general ledger. The clerk is also responsible for preparing the check and recording it in the digital cheque register. These are separate part of the custody activity. However, in ABC Limited Company, the account payable clerk operates all these responsibilities in the firm. It is the main internal control weakness in the cash disbursement system of ABC Limited Company.
Second Question:
Part A:
The uncontrolled risk associated with the Account Information System of XYZ Limited:
Based on the case study of XYZ Limited, there are several risks associated with the credit sales procedure of XYZ Limited. The sales department receives the orders of the customers by email and fax in an unstandardised format (Rathwell et al., 2020). This format can increase the risk associated with mistakenly skipping the email and fax by the sales clerk. It can increase the risk of error or omission issue by the sales clerk.
The sales clerk is responsible for approving the credit sales, calculating the discounts and commission on credit sales and recording the sales in the AIS’s sales journal. The clerk is also responsible for preparing the three documents a customer invoice, a sales order and a packing slip (Ramesh et al., 2017). It indicates that more than one activities of the accounting function are operated by the sales clerk. It can increase the risk of conspiracy and fraud by the sales clerk of the company. The Sales clerk should not be allowed for preparing customer’s invoice because they might not prepare the invoice for certain customers to receive profits from those customers.
In this system, the accounting clerk is responsible for the receiving of three documents prepared by the sales clerk, updating the business sales records in the ledger of account receivable subsidiary. The clerk is also responsible for the review of the checks and remittance advice, updating the Account receivable subsidiary ledger and also a recording of the cash receipts in the cash receipt journal. The clerk is also responsible for updating cash, AR control, and sales account in the AIS general ledger system (Harp and Barnes, 2018). It indicates that the accounting clerk is responsible for more than separating parts of one accounting function. It can increase the risk of fraudulent activities by the accounting clerk while maintaining accounting records.
These are the main uncontrolled risks associated with the credit sales procedure system of XYZ Limited.
Specific Internal control weaknesses that cause the risks:
Based on the above analysis of the uncontrolled risks, the sales clerk, accounting clerk and mailroom clerk of the firm engaged in more than one accounting function. It indicates that the firm is not maintained the policy of the segregation of duties. The sales clerk is responsible for approving credit sales, calculating discounts and commission, and recording the entire details on the sales journal (Harp and Barnes, 2018). Also, the clerk is responsible for making the invoice for customers, packing slip and sales order. It is clear evidence of not approving the policies of segregation of duties. It is the main internal control weakness in the credit sales procedure system.
The accounting clerk is also responsible for maintaining the ledger of account receivable subsidiary and general ledger system and updating cash and AR control in the general ledger system. It is a clear indication of the internal control weakness by which a clerk can steal cash that can hamper the company assets. Moreover, the accounting clerk is also responsible for the review of checks and remittance advice (Rahim et al., 2017). It can be the reason for skimming issues inside the firm, like a clerk can steal the check and also a clerk can write the account receivable part of the customer as a bad debt.
Moreover, in this system, the mailroom clerk is also responsible for opening the envelope that contains remittance advice and customers’ check, inspecting the check for checking its completeness and reconciling the checks with the remittance advice and send to the accounting department. According to the accounting function rule, one clerk cannot do the operation of two separate parts of any accounting task (Lawrence et al., 2018). However, here the clerk is responsible for more than two activities. It is also another indication of internal control weakness in the system. According to this system, a clerk can pocket a customer’s check for receiving the profit from the client, and they can also issue the credit memo for that person to avoid the balance due issue on the name of that particular customer.
Third Question:
Part A: Importance of an active board of directors’ audit committee:
The active board of directors’ audit committee plays an important role in effectively and smoothly operating the accounting function in the organisation. It is important to give challenge the internal auditors to perform the particular function efficiently and appropriately. The presence of the audit committee members in the organisation is important to continue the management process smoothly in the organisation (Moses, 2019). They are responsible for investigating the entire management system and identify the risks associated with the management process. They should operate as the sounding board for the organisation’s employees. The presence of an active board of directors’ audit committee is important to observe suspicious behaviour and actively spot fraudulent activities within the organisation. They should have become the independent guardian of the firm’s assets (Al?Shaer and Zaman, 2018). They also should do the appropriate activities that are appropriate and effective for the company. The fraudulent corporate activities in the organisation often have some relationship with the poor audit committee members (Al-Dhamari et al., 2018). The active board of directors’ audit committee must be transparent, loyal and responsible to reduce the fraudulent activities inside the organisation. The active board of directors’ audit committee can be a failure in their activities due to lack of experienced committee members in the audit committee, lack of independence of the members and the absence of the members (Zhou et al., 2018).
Part B: Identification of frauds based on the internal control weaknesses and associated risks with it:
Based on the identified control weaknesses and risks associated with these control weaknesses, the following are the types of fraud that can be possible in the given business environment.
A sales clerk of the organisation is responsible for approving the credit and preparing the sales order of the products. If the sales clerk is responsible for preparing the order, then it can increase the risk of selling goods and products to un-creditworthy customers (DeLiema et al., 2020). It can increase the chance of Account receivable fraud by representing the fictitious sale in the sales report.
If the Account Receivable clerk has access to the AR-control account in the AIS general ledger system and AR-sub ledger, it can increase the risk of incorrect record of the transactions in the general leader or AR-sub ledger. It can increase Account payable fraud by which the clerk can submit the fake invoices and tamper with the check of the clients.
Billing clerks in this organisation are responsible for preparing customer bills, and recording the order of the sales without any evidence that goods are shipped or not (DeLiema et al., 2020). It can increase the risk of the recording of the wrong entry of sales transactions without any concern that products are shipped or not. It can increase the vendor fraud issue by generating a false payment in the name of the fictitious vendor.
The warehouse clerk in the firm has access to both maintaining the inventory record in AIS and inventory sub-ledger record in AIS. It can increase the risk of misappropriation of inventory records. It can increase the Asset misappropriation type fraud that can cause the check forgery by which the clerk can forge the signature of higher authority on a check made out to the name of the clerk (Putra and Dwirandra, 2019).
Shipping clerks of the firm prepares the shipping notice to notify the billing department that goods were shipped. Preparation of the shipping notice by the shipping clerk can increase the risk of business transaction recording error. It can also increase the chance of asset misappropriation fraud by the shipping clerk (Setiawan, 2018).
Fourth Question:
According to the given scenario, the management of the firm suggested drawing the data for analytical reviews of the data and substantive review of the data from the data warehouse instead of using the operational database system (Farooqui and Mehra, 2018). Based on this proposal, from the perception accounting clerk, the firm should transfer a certain amount of accounting data into the summary data views before loading the data into the data warehouse system. It will increase the operational efficiency of the AIS System (Nadikattu, 2019). It will help the decision-maker to see the summarised figure of product sales for a month, a week, a quarter or a year-wise. The data warehouse specifically contains the requested summary views of business data to reduce the time of processing of the data during the analysis. It will give analytical reviews of the business record (Bouali et al., 2019). The operational database shows the virtual views of the business data, where the data warehouse represents the business records and data on a de-normalised physical table.
However, the firm should separate the functions of the data warehouse from the functions of the operational database. The operational and structural requirements of processing the transactions and the system of data mining in the data warehouse system are different from the operational database system (Blaži? et al., 2017). However, it is also impractical to keep the archive data and operational and current data in the same database system. The transaction processing system of AIS needs a particular data structure that supports everyday business performance. However, the data mining system needs the data in an organised manner to permit the detection of the underlying trends in the system. Although business transaction record or data are loaded in the data warehouse after finishing the activity, and the data are always in a stable state. Still, it can sometimes hamper the data mining system (Solodovnikova and Niedrite, 2018).
Fifth Question:
Part A: Identification of control problems and the possible dangers:
Based on the given design, the work centre department of the AIS System in the firm prepares job ticket, move ticket and material requirement document based on the Bill of material, Rout sheet copy and work order evidence from the production planning department and control document. After preparing these documents, the department sends "move ticket" and "job ticket" documents to the accounting department and material requirement document to the inventory control system to update the inventory details and prepare the report of required material in inventory (Bure and Tengeh, 2019). The production planning and control department also sends the work order details to the accounting department. The accounting department reviews the work order, move ticket and job ticket to prepare the work in a progress report. The analysis of the entire system indicates that an inventory clerk has access to the move ticket and job ticket. They can misplace the ticket to steal the products of the company and also can update the inventory control table (Walker-Roberts et al., 2018). They can also list the product on the required material table. The accounting clerk can also misplace the move ticket, job ticket or work order paper. They can also prepare the fake Bill to steal the cash from the company (Chalmers et al., 2019). They can also prepare the negotiable amount of Bill for their favoured clients to get the profit from the clients.
Corrective procedure to control threats:
1. The firm can control these risk by ensuring that all business transactions (sales and purchases) are properly authorized.
2. Ensuring that all recorded business transactions are valid.
3. Ensuring that all business sale and purchase transactions, work order, work in a progress report, job ticket and move ticket and inventory control report are recorded accurately and efficiently.
4. The firm can use appropriate application access control mechanism (such as individual user ID and password for accessing the ERP system) for field checks and validity checks to enhance the accuracy and reliability of the system (Liu et al., 2018). The firm can use a one-time password system while login into the ERP.
Part B: Objectives of eliminating receiving function:
In the AIS system, an account receivable clerk can intentionally omit the business records and any receiving records of the products or any item. The functions of the account receiving function are also taking more time than other functions. Suppose an accounting clerk has access to receive the goods and updates the records in the account receivable sub-ledger and AR Control in the general ledger. However, it can increase the chance of fraudulent activities in the organisation that can harm the company’s assets.
The reason for resolving the accounting and auditing problem:
1. The accounting problem needs to resolve because the accounting information maintains the integrity of the entire process.
2. Accounting information provides a clear picture of the organisation’s needs and problems. It helps in the development of the AIS system in the organisation (David, 2017).
3. The appropriate accounting information system ensures the auditors that the entire AIS system is designed with accuracy, efficiency and using computer audit techniques (Balios, 2021).
4. Useful Accounting information helps in comparing the records of the competing project. These are the main reason to resolve the accounting problems in the system.
5. Auditing problems also need to resolve to develop careful planning for the firm in a cost-effective way to reduce the risk of an unwanted, unneeded, ineffective and inefficient system.
6. Auditing is important to validate the business transactions, identifying the risks in the system and develop a control structure to detect and prevent the risk in the accounting system efficiently (Shikdar et al., 2018).
7. The audit problem needs to resolve to reduce the issue of misuse, misappropriation of assets, corruption, and illegal use of accounting information in the system.
Sixth Question:
The control mechanism that can prevent Miss Emma from perpetrating this unwanted fraudulent activity:
The firm should implement the audit trail control mechanism to monitor access to business transactions and records. It will help the firm to monitor the unauthorised access attempts via offsite and network location (Kamaliah et al., 2018). The firm should implement an electronic sensitisation mechanism to detect unauthorised access by any people. The firm should be encrypted the sensitive data using the secured encryption method (RSA mechanism) to prevent fraudulent activities.
The firm should also use the one-time password mechanism system in their AIS. It would prevent the installation of the sniffer program (Duffany, 2018). It would also prevent the sniffer program to detect the user ID and passwords of employees.
The firm should establish a strong password control policy to ensure that the employees should create a strong password for login, and the password can be changed at regular intervals.
The firm should perform a background check on employees of the organisation who are in a financial sensitive position (Ali et al., 2019). It would help in revealing that Miss Emma was completed her master degree in computer science, then why she applied for the account payable clerk.
The firm should also implement the overtime policy to restrict and monitor the entire system and overtime hour worked by any employee.
The firm should develop the encrypted and valid file vendor transaction recording with the appropriate and accurate security procedures in the particular function and places to limit the unauthorised access to the secure encryption key (Ylmaz et al., 2018).
The firm can design the program in a certain way that only accepts certain inputs from the designated terminal, user and times of the day to prevent the input data alteration risk.
The firm can terminate Miss Emma immediately due to the reason of unauthorised access to all computer information and equipment. It will help the firm to prevent the destruction or alteration of their sensitive financial records of the business. These are the control mechanism that can prevent Miss Emma from perpetrating fraudulent activity in the organisation. ?
References:
Al-Dhamari, R., Almagdoub, A. and Al-Gamrh, B., 2018. Are audit committee characteristics important to the internal audit budget in Malaysian firms?. Contaduría y administración, 63(SPE2), pp.947-969.
Ali, M.A., Azad, M.A., Centeno, M.P., Hao, F. and van Moorsel, A., 2019. Consumer-facing technology fraud: Economics, attack methods and potential solutions. Future Generation Computer Systems, 100, pp.408-427.
Al?Shaer, H. and Zaman, M., 2018. Credibility of sustainability reports: The contribution of audit committees. Business strategy and the environment, 27(7), pp.973-986.
Balios, D., 2021. The impact of Big Data on accounting and auditing. International Journal of Corporate Finance and Accounting (IJCFA), 8(1), pp.1-14.
Blaži?, G., Poš?i?, P. and Jakši?, D., 2017, May. Data warehouse architecture classification. In 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO) (pp. 1491-1495). IEEE.
Bouali, H., Akaichi, J. and Gaaloul, A., 2019. Real-time data warehouse loading methodology and architecture: a healthcare use case. International Journal of Data Analysis Techniques and Strategies, 11(4), pp.310-327.
Bure, M. and Tengeh, R.K., 2019. Implementation of internal controls and the sustainability of SMEs in Harare in Zimbabwe. Entrepreneurship and Sustainability Issues, 7(1), p.201.
Chalmers, K., Hay, D. and Khlif, H., 2019. Internal control in accounting research: A review. Journal of Accounting Literature, 42, pp.80-103.
Cheng, Q., Goh, B.W. and Kim, J.B., 2018. Internal control and operational efficiency. Contemporary Accounting Research, 35(2), pp.1102-1139.
David, R., 2017. Contribution of records management to audit opinions and accountability in government. SA Journal of Information Management, 19(1), p.14.
DeLiema, M., Deevy, M., Lusardi, A. and Mitchell, O.S., 2020. Financial fraud among older americans: Evidence and implications. The Journals of Gerontology: Series B, 75(4), pp.861-868.
Dewi, N., Azam, S. and Yusoff, S., 2019. Factors influencing the information quality of local government financial statement and financial accountability. Management Science Letters, 9(9), pp.1373-1384.
Donelson, D.C., Ege, M.S. and McInnis, J.M., 2017. Internal control weaknesses and financial reporting fraud. Auditing: A Journal of Practice & Theory, 36(3), pp.45-69. Duffany, J.L., 2018. Computer Security. In Computer and Network Security Essentials (pp. 3-20). Springer, Cham.
Farooqui, N.A. and Mehra, R., 2018, December. Design of a data warehouse for medical information system using data mining techniques. In 2018 Fifth International Conference on Parallel, Distributed and Grid Computing (PDGC) (pp. 199-203). IEEE.
Harp, N.L. and Barnes, B.G., 2018. Internal control weaknesses and acquisition performance. The Accounting Review, 93(1), pp.235-258.
Jacoby, G., Li, Y., Li, T. and Zheng, S.X., 2018. Internal control weakness, investment and firm valuation. Finance Research Letters, 25, pp.165-171.
Kamaliah, K., Marjuni, N.S., Mohamed, N., Mohd-Sanusi, Z. and Anugerah, R., 2018. Effectiveness of monitoring mechanisms and mitigation of fraud incidents in the public sector. Administratie si Management Public, 30, pp.82-95.
Lai, S.C., Li, H., Lin, H. and Wu, F., 2017. The influence of internal control weaknesses on firm performance. Journal of Accounting and Finance, 17(6), pp.82-95.
Lawrence, A., Minutti-Meza, M. and Vyas, D., 2018. Is operational control risk informative of financial reporting deficiencies?. Auditing: A Journal of Practice & Theory, 37(1), pp.139-165.
Liu, L., De Vel, O., Han, Q.L., Zhang, J. and Xiang, Y., 2018. Detecting and preventing cyber insider threats: A survey. IEEE Communications Surveys & Tutorials, 20(2), pp.1397-1417.
Moses, T., 2019. Board Characteristics, Audit Committee Composition, And Financial Reporting in Nigeria. International Journal of Innovative Social Sciences & Humanities Research, 7(1), pp.37-44.
Nadikattu, R.R., 2019. Data Warehouse Architecture–Leading the Next Generation Data Science. Rahul Reddy Nadikattu" Data Warehouse Architecture–Leading the next generation Data Science" International Journal of Computer Trends and Technology, 67(2019), pp.78-80.
Putra, G.S.A. and Dwirandra, A.A.N.B., 2019. The effect of auditor experience, type of personality and fraud auditing training on auditors ability in fraud detecting with professional skepticism as a mediation variable. International research journal of management, IT and social sciences, 6(2), pp.31-43.
Rahim, S.A.A., Nawawi, A. and Salin, A.S.A.P., 2017. Internal control weaknesses in a cooperative body: Malaysian experience. International Journal of Management Practice, 10(2), pp.131-151.
Ramesh, R., Prabu, M., Magibalan, S. and Senthilkumar, P., 2017. Hazard identification and risk assessment in automotive industry. International journal of ChemTech research, 10(4), pp.352-358.
Rathwell, B.W., Van Bossuyt, D.L., Pollman, A. and Sweeney, J., 2020. A Method to Account for Personnel Risk Attitudes in System Design and Maintenance Activity Development. Systems, 8(3), p.26.
Saedi, R. and Dastgir, M., 2017. The effect of internal control weakness on investment efficiency of companies listed in Tehran stock exchange. International Journal of Finance & Managerial Accounting, 2(7), pp.25-31.
Setiawan, S., 2018. The effect of internal control and individual morality on the tendency of accounting fraud. Asia Pacific Fraud Journal, 3(1), pp.33-41.
Shikdar, M.A., Faruk, O. and Chowdhury, M.M.H., 2018. Reducing the audit expectation gap: A model for Bangladesh perspective. International Journal of Management, Accounting and Economics, 5(3), pp.169-180.
Solodovnikova, D. and Niedrite, L., 2018, July. Towards a Data Warehouse Architecture for Managing Big Data Evolution. In DATA (pp. 63-70).
Walker-Roberts, S., Hammoudeh, M. and Dehghantanha, A., 2018. A systematic review of the availability and efficacy of countermeasures to internal threats in healthcare critical infrastructure. IEEE Access, 6, pp.25167-25177.
Ylmaz, E.N., Ciylan, B., Gönen, S., Sindiren, E. and Karacay?lmaz, G., 2018, April. Cyber security in industrial control systems: Analysis of DoS attacks against PLCs and the insider effect. In 2018 6th International Istanbul Smart Grids and Cities Congress and Fair (ICSG) (pp. 81-85). IEEE.
Zhou, H., Owusu-Ansah, S. and Maggina, A., 2018. Board of directors, audit committee, and firm performance: Evidence from Greece. Journal of International Accounting, Auditing and Taxation, 31, pp.20-36.












